CTO at NCSC Summary: week ending April 6th
More security solution vulnerability and exploitation..
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week more security solution vulnerability and exploitation. Remember to ask your vendors where on their roadmaps implementation of the Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliancess is and when it will be delivered.
In the high-level this week:
Cyber Security and Resilience Policy Statement to strengthen regulation of critical sectors - UK NCSC comments - “New proposals will combat the growing threat to UK critical national infrastructure (CNI).”
Cyber Security and Resilience Bill: policy statement - Department for Science, Innovation and Technology, Feryal Clark MP and The Rt Hon Peter Kyle MP publish - “This statement details the confirmed and proposed measures in the Cyber Security and Resilience Bill, which will be laid before Parliament later this year.”
New guidance on securing HTTP-based APIs - UK NCSC publishes -”NCSC has published new guidance on securing HTTP-based APIs, which is designed to help technical staff to design or build secure applications that offer an HTTP API.”
Device Security Guidance: Chrome OS - UK NCSC updates - “Whilst this guide does not apply to any specific version of ChromeOS, these recommendations were tested in January 2025”
Standard smartphones to receive signal from space - OFCOM announces - “UK first country in Europe to move ahead with innovative plans for standard smartphones to make satellite calls”
Reflections on his First 100 Days: A Conversation with Richard Horne - UK NCSC podcasts - “In this episode, we sit down with Richard Horne, our CEO, as he reflects on his first 100 days in the role. From surprises and challenges to insights on the evolving cyber security landscape, Richard shares his experiences and key takeaways from his time in post. Tune in for an inside look at his journey so far!”
Fast Flux: A National Security Threat - NSA alerts - “Many networks have a gap in their defenses for detecting and blocking a malicious technique known as “fast flux.” This technique poses a significant threat to national security, enabling malicious cyber actors to consistently evade detection.”
Aging Technology, Emerging Threats: Examining Cybersecurity Vulnerabilities in Legacy Medical Devices - US House Energy & Commerce Oversight and Investigations Subcommittee publishes - “One challenge with these devices is that the hardware can last 10 to 30 years, but the software becomes obsolete much sooner. Patching and updating software are common ways to address cybersecurity vulnerabilities, but it is unlikely that such vulnerabilities can be sufficiently mitigated through these approaches due to outdated technology and compatibility issues.”
Continuation of the National Emergency With Respect to Significant Malicious Cyber-Enabled Activities - The White House instructs - “For this reason, the national emergency declared in Executive Order 13694, and with respect to which additional steps were taken in Executive Order 13757, Executive Order 13984, Executive Order 14110 (revoked by Executive Order 14148), and Executive Order 14144, must continue in effect beyond April 1, 2025. Therefore, in accordance with section 202(d) of the National Emergencies Act (50 U.S.C. 1622(d)), I am continuing for 1 year the national emergency declared in Executive Order 13694.”
Foreign Information Manipulation and Interference Threats: Exposing the architecture of FIMI operations - European Union External Action reports - “The novelty of this years’ report is the exposure of massive digital arsenals put in place specifically by Russia and China to conduct their FIMI operations. As we increase our fluency in FIMI, the EU is also ramping up its punitive response. In December 2024, for example, the EU imposed the first ever sanctions for this behaviour”
Cyber Defense Assistance and Ukraine: Lessons and Moving Forward - Aspen Institute thinks - “Based on observations in early 2025, the private sector is largely sustaining capabilities provided through early CDA activities including intelligence support, software licenses, training programs and other assistance. However, the level of new requests and initiatives has diminished significantly. Various factors are influencing this situation including 1) successful Ukrainian digital resilience, 2) perceptions of Russian cyber ineffectiveness in the cyber domain, 3) fatigue among certain assistance providers, 4) lack of dedicated funding to support large-scale, systemic initiatives, and 5) uncertain impacts of assistance efforts”
Commission to invest €1.3 billion in artificial intelligence, cybersecurity and digital skills - European Commission announces - “Cybersecurity solutions such as the EU Cybersecurity Reserve will improve the resilience and security of critical infrastructures including hospitals and submarine cables.”
Driving Change, Building Resilience: ENISA’s revised Strategy and Structure - European Union Agency for Cybersecurity announces - “A reframed strategy for a clearer vision - The ENISA strategy now focuses on vertical and horizontal objectives to enhance cooperation and anticipate threats by:
Horizontal objectives:
Empowered communities in an involved and engaged cyber ecosystem;
Foresight on emerging and future cybersecurity opportunities and challenges;
Consolidated and shared cybersecurity information and knowledge support for Europe;
Vertical objectives:
Support for effective and consistent implementation of EU cybersecurity policy;
Effective Union preparedness and response to cyber incidents, threats and cyber crises;
Strong cyber security capacity within the EU;
Building trust in secure digital solutions.”
Red tape that tears us apart: regulation fragments Indo-Pacific cyber resilience - Ravi Nayyar observes - “The fragmentation of cyber regulation in the Indo-Pacific is not just inconvenient; it is a strategic vulnerability.”
EU capabilities in space: Scenarios for space security by 2050 - European Parliament Think Tank thinks - “Harmful interferences, such as satellite jamming and cyberattacks, emphasise the need for robust legal frameworks to safeguard space assets.”
Reporting on/from China
Improve the legal responsibility system and build a solid network security barrier - China Internet Information Office announces - “This revision intends to improve the legal liability system, stipulate the legal liability for illegal situations such as causing serious or particularly serious consequences that endanger network security, and increase the penalties for related illegal acts by increasing the amount of fines and adding more types of penalties.”
China claims AI chip progress as Loongson unveils CPUs amid self-sufficiency push - South China Morning Post reports - “The new processors, designated 2K3000 and 3B6000M, share identical silicon but differ in packaging; one for industrial control applications and the other for mobile devices. Both integrate eight Loongson’s central processing unit (CPU) cores, which are based on its LoongArch instruction set architecture.”
Huawei’s ternary logic patent could solve the problem of power-hungry AI chips - South China Morning Post reports - ”The approach could be used to reduce the number of transistors on a chip and therefore reduce energy consumption, according to the patent application, which comes at a time when advanced chip designs at the 2-nanometre level are approaching physical limits.”
Chinese scientists make brain-computer co-evolution possible for the first time - South China Morning Post reports (in Feb but mind blowing)- ”Chinese researchers say they have developed the world’s first two-way adaptive brain-computer interface (BCI), boosting efficiency 100-fold and moving the technology a step closer towards practical everyday use.”
AI
A Framework for Evaluating Emerging Cyberattack Capabilities of AI - Google DeepMind publish - “Our benchmark comprises 50 new challenges spanning various cyberattack phases. Using this benchmark, we devised targeted cybersecurity model evaluations, report on AI’s potential to amplify offensive capabilities across specific attack phases, and offer recommendations for prioritizing defenses. We believe this represents the most comprehensive AI cyber risk evaluation framework published to date.”
Large Language Models Pass the Turing Test - - the first canary has died - UC San Diego San Diageo announce - “The results constitute the first empirical evidence that any artificial system passes a standard three-party Turing test.” - now show the captcha evidence..
Tracing the thoughts of a large language model - Anthropic publish - “At the same time, we recognize the limitations of our current approach. Even on short, simple prompts, our method only captures a fraction of the total computation performed by Claude, and the mechanisms we do see may have some artifacts based on our tools which don't reflect what is going on in the underlying model.”
AI and Serious Online Crime - CeTAS publish - “There is considerable evidence emerging of a substantial acceleration in AI-enabled crime. This includes evidence of the use of AI for financial crime, phishing, distributed denial of service (DDoS), child sexual abuse material (CSAM) and romance scams.”
Generative AI in Cybersecurity: A Comprehensive Review of LLM Applications and Vulnerabilities - various universities publish - “Our evaluation of 40 LLM models in terms of cybersecurity knowledge and hardware security demonstrated their varying strengths and weaknesses. We also conducted a detailed assessment of cybersecurity datasets used for LLM training and testing, from data creation to usage, identifying gaps and opportunities for future research.”
Towards risk-based AI regulation - Goethe University publish - “existing definitions of AI do not meet the most important requirements for legal definitions. Therefore, policy makers should not rely substantially on the term AI to define the material scope of AI.”
Cyber proliferation
Joint Communiqué of France and the United Kingdom on the Paris Conference of the Pall Mall Process - UK Foreign, Commonwealth & Development Office publishes - “The Code of Practice builds upon the pillars highlighted in the 2024 Pall Mall Process declaration: accountability, precision, oversight and transparency, and draws from the Pall Mall Process consultation on good practices conducted in Autumn 2024. It represents a significant step forward towards the implementation of the United Nations framework on responsible State behaviour in cyberspace.”
Italian government reportedly admits targeting activists - Euractiv reports - “Undersecretary Alfredo Mantovano has reportedly admitted that Italy’s intelligence services authorised spyware surveillance on members of the NGO Mediterranea Saving Humans. Yet, a crucial mystery remains - who was behind the surveillance of Fanpage.it director Francesco Cancellato?”
Bounty Hunting
Nothing of note this week
Munich Re expects global cyber insurance market to double by 2030 - Risk and Insurance reports - “Munich Re projects the global cyber insurance market to reach $16.3 billion in gross written premiums in 2025 as organizations face intensifying threats from ransomware attacks, online scams, data breaches and supply chain vulnerabilities, according to a new report from the reinsurer… Although cyber premium growth has slowed in the past two years, Munich Re estimates that by 2030 the cyber insurance market will double from today’s volume to $32.4 billion in premiums.”
Reflections this week are around the Model Context Protocol (MCP) and its emerging status as a defacto standard for agentic AI integration.
You will see in the below (tools) that there are now various MCP integrations to drive reverse engineering so you can vibe away...
However on the flip side the cyber security of MCP implementations and integrations is not entirely understood or appreciated as yet.
For example a recently released paper Model Context Protocol (MCP): Landscape, Security Threats, and Future Research Directions outlines the challenges. Then we have AI Model Context Protocol (MCP) and Security which provides a good overview of how to approach.
Why do we need to care? Well jro shows it is possible to get arbitrary code execution through MCP when a malicious binary is analysed with a certain IDA Pro MCP server for example (writeup)…
Anyway, it looks like MCP is gaining traction.. but there are risks and further work is required to ensure we get the cyber security we want in this emergent agentic world..
Not getting this via email? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
UAC-0219: Cyber espionage using PowerShell stealer WRECKSTEEL
Ukrainian CERT details an alleged Russian campaign which is going after a very specific set of file types.
The purpose of the latter is to download and launch a PowerShell script that provides search and upload using cURL files according to the list of extensions ("*.doc", "*.txt", "*.docx", "*.xls", "*.xlsx", "*.pdf", "*.rtf", "*.odt", "*.csv", "*.ods", "*.ppt", "*.pptx", "*.png", "*.jpg", "*.jpeg"), as well as screenshots of the computer
https://cert.gov.ua/article/6282902
Reporting on China
The Espionage Toolkit of Earth Alux A Closer Look at its Advanced Techniques
Lenart Bermejo, Ted Lee and Theo Chen detail an alleged Chinese operation which leverages vulnerable edges for initial access before lateral movement.
The attacks are targeted toward the Asia-Pacific (APAC) and Latin American regions, hitting key sectors such as government, technology, logistics, manufacturing, telecommunications, IT services, and retail.
Regular patching and updating, vigilant monitoring for any signs of compromise, and proactive protection can help prevent such threats from infiltrating organizations’ systems.
To gain entry into the system, Earth Alux mostly exploits vulnerable services in exposed servers. It then implants web shells such as GODZILLA to facilitate the delivery of its backdoors.
https://www.trendmicro.com/en_us/research/25/c/the-espionage-toolkit-of-earth-alux.html
Reporting on North Korea
DPRK IT Workers Expanding in Scope and Scale
Jamie Collier details alleged North Korean IT worker activity is happening in the UK. I met with one organisation this week who mentioned their return-to-office is in part intended to mitigate this threat.
GTIG has also observed a diverse portfolio of projects in the United Kingdom undertaken by DPRK IT workers. These projects included web development, bot development, content management system (CMS) development, and blockchain technology, indicating a broad range of technical expertise, spanning traditional web development to advanced blockchain and AI applications.
Specific projects identified include:
Development of a Nodexa token hosting plan platform using Next.js, React, CosmosSDK, and Golang, as well as the creation of a job marketplace using Next.js, Tailwind CSS, MongoDB, and Node.js.
Further blockchain-related projects involved Solana and Anchor/Rust smart contract development, and a blockchain job marketplace built using the MERN stack and Solana.
Contributions to existing websites by adding pages using Next.js and Tailwind CSS,
Development of an artificial intelligence (AI) web application leveraging Electron, Next.js, AI, and blockchain technologies.
https://cloud.google.com/blog/topics/threat-intelligence/dprk-it-workers-expanding-scope-scale
From Contagious to ClickFake Interview: Lazarus lever
Amaury G., Coline Chavane and Felix Aimé provide further insight into alleged North Korean modus operandi. Note the targeting and variation in operating system specific tradecraft.
The infection chain varies by operating system: on Windows, a VBS script downloads and executes the GolangGhost backdoor via NodeJS. While on macOS, a Bash script downloads and extracts malicious components, then executes FrostyFerret to steal the system password before launching GolangGhost. This final implant enables remote control and data theft, including browser information exfiltration.
Fake job offers are designed to attract profiles different from software developers and engineers. This may reflect a new Lazarus strategy aimed at targeting cryptocurrency industry employees with limited technical expertise, making them less likely to detect the malicious command during the interview.
https://blog.sekoia.io/clickfake-interview-campaign-by-lazarus/
Reporting on Iran
Nothing of note this week
Reporting on Other Actors
Intrusion into the Threat Actor's Infrastructure
Resecurity do things which aren’t legal to do in lots of parts of the world in the private sector.
Around that time, Resecurity identified a vulnerability present at the Data Leak Site (DLS) of BlackLock in the TOR network - successful exploitation of which allowed our analysts to collect substantial intelligence about their activity outside of the public domain.
Since that time, our analysts from the HUNTER team have been covertly acquiring critical and previously undisclosed artifacts related to threat actors' network infrastructure, logs, ISPs and hosting providers involved, timestamps of logins, associated file-sharing accounts at MEGA, the group created to store stolen data from the victims (which later got published via DLS in TOR). A successful compromise of BlackLock's DLS allowed to uncover a trove of information about the threat actors and their Modus Operandi (MO), but more importantly, to predict and prevent some of their planned attacks and protect undisclosed victims by alerting them.
One Time Pwnage: SLOVENLY COMET
Security Alliance details some nightmare fuel. Also gives a reason why you moving away from SMS MFA to Passkeys (ideally) or app based is wise.
A crucial observation across successful account takeovers was the reliance on SMS-based account access codes. After testing multiple hypotheses, a coordinated effort by local security researchers and our team pointed an emerging theory: a compromise within SMS gateway providers.
Because many companies use the same handful of SMS gateway providers, attackers successfully intercepted SMS-based MFA messages from numerous prominent services including Google, Microsoft, Apple, Telegram, Facebook, Mercadolibre, Amazon, Binance, Betfun, Instagram, TikTok, Temu, and Signal, as well as regional services such as Mercado Pago, Mi Argentina (Argentina), Banco Formosa (Uruguay), TRANSVIP (Chile). Based on internal investigations, publicly available information, and leaked data, we believe at least 50 services were affected.
https://www.securityalliance.org/news/2025-03-slovenly-comet
Discovery
How we find and understand the latent compromises within our environments.
100 Days of KQL
Aura continues to pump out the goodness..
Detecting C2-Jittered Beacons with Frequency Analysis
Diego walks through how to detect in practice which some sublime applied tradecraft on show.
Now, we can see exactly the same thing, but this time, our Red signal (beacon) has jitter in terms of both amplitude and periodicity. It will ping back between 20 and 29 hours, and the amplitude also has a modifier to make it more random.
Upon analysis, we can see that we still have a spike, but it's much more difficult to detect. It’s flagged as the expected frequency where the beacon should be.Note that this example still has a beacon with significant amplitude compared to our original signal, and even with that, it is hard to find. So, what can we do?
https://www.diegowritesa.blog/2025/04/detecting-c2-jittered-beacons-with.html?m=1
DroidTTP: Mapping Android Applications with TTP for Cyber Threat Intelligence
Dincy R Arikkat, Vinod P., Rafidha Rehiman K. A., Serena Nicolazzo, Marco Arazzi, Antonino Nocera and Mauro Conti tease at the value of AI when used for cyber defence. This is a modern pipeline which should inspire..
Our structured pipeline includes dataset creation, hyperparameter tuning, data augmentation, feature selection, model development, and SHAP-based model interpretability. Among LLMs, Llama achieved the highest performance in Tactic classification with a Jaccard Similarity of 0.9583 and Hamming Loss of 0.0182, and in Technique classification with a Jaccard Similarity of 0.9348 and Hamming Loss of 0.0127. However, the Label Powerset XGBoost model outperformed LLMs, achieving a Jaccard Similarity of 0.9893 for Tactic classification and 0.9753 for Technique classification, with a Hamming Loss of 0.0054 and 0.0050, respectively. While XGBoo
https://arxiv.org/abs/2503.15866
How to detect it and Finding Evil in Memory with MemProcFS FindEvil Plugin
Dean (Akash Patel) shows the power of this approach..
MemProcFS FindEvil is an incredibly powerful tool for detecting hidden malware and process manipulation. By cross-referencing memory structures and leveraging YARA rules, it provides an in-depth look at suspicious activity that many traditional security tools might miss.
Theory: EDR Syscall hooking and Ghost Hunting, my approach to detection
Flux provides a super power in the detection arms race.
having implemented one Ghost Hunting technique already, what sets my technique apart:
If NTDLL gets remapped by malware (i.e. a fresh copy loaded from the system into the process) - it will not affect the ability of Sanctum to detect the malicious behaviour. If anything, this will raise the risk score generated.
This technique can detect direct syscalls, indirect syscalls, hells gate etc.
This technique thwarts dynamic syscall runtime resolution as we overwrite the entire stub (including the SSN) with NOPs before writing our jump instruction.
https://fluxsec.red/edr-syscall-hooking
Defence
How we proactively defend our environments.
Using KQL to Detect Gaps in your Conditional Access Strategy
Dylan Tenebruso provides a number of queries which will be useful in surfacing a subset of gaps in Microsoft environments.
https://attackthesoc.com/posts/detect-cap-gaps/
Model Context Protocol (MCP) and Security
Omar Santos provides an overview given the increasingly foundation nature of MCP in agentic AI integration.
The Model Context Protocol (MCP) is an open standard that provides a universal way to connect AI models and agentic applications to various data sources and tools. It's how AI applications and applications can supply context (documents, database records, API data, web search results, etc.) to AI applications. This capability is very powerful, but it also raises important cybersecurity-related questions.
Apple adds support for TCC events in macOS
Patrick Wardle details how this feature can be used to pragmatically subscribe to events and move away from logfile based approaches which will provide value in various use cases.
In macOS 15.4, Apple will (finally) add TCC events to Endpoint Security
https://objective-see.org/blog/blog_0x7F.html
New security requirements adopted by HTTPS certificate industry
Chrome Root Program and Chrome Security Team detail the changes
At a high-level, “Moving Forward, Together” is our vision of the future. It is non-normative and considered distinct from the requirements detailed in the Chrome Root Program Policy. It’s focused on themes that we feel are essential to further improving the Web PKI ecosystem going forward, complementing Chrome’s core principles of speed, security, stability, and simplicity. These themes include:
Encouraging modern infrastructures and agility
Focusing on simplicity
Promoting automation
Reducing mis-issuance
Increasing accountability and ecosystem integrity
Streamlining and improving domain validation practices
Preparing for a "post-quantum" world
Earlier this month, two “Moving Forward, Together” initiatives became required practices in the CA/Browser Forum Baseline Requirements (BRs). The CA/Browser Forum is a cross-industry group that works together to develop minimum requirements for TLS certificates. Ultimately, these new initiatives represent an improvement to the security and agility of every TLS connection relied upon by Chrome users.
https://security.googleblog.com/2025/03/new-security-requirements-adopted-by.html
What keeps kernel shadow stack effective against kernel exploits?
Satoshi details why a subset of kernel exploits are going to be harder..
Shadow stack enhances backward-edge code flow integrity but faces challenges in kernel-mode, where privileged attackers can manipulate page tables. Making SSS pages read-only with SLAT may not be viable protection against such attacks. Supervisor shadow stack restrictions (SSSCheck) on AMD and supervisor shadow-stack control on Intel address these issues. These features allow secure supervisor shadow stack enforcement with minimal performance impact.
https://tandasat.github.io/blog/2025/04/02/sss.html
Hotpatch for Windows client now available...
David Callaghan announce the reduced need to reboot on Windows to patch.
Hotpatch updates for Windows 11 Enterprise, version 24H2 for x64 (AMD/Intel) CPU devices are now available. With hotpatch updates, you can quickly take measures to help protect your organization from cyberattacks, while minimizing user disruptions.
Incident Writeups & Disclosures
How they got in and what they did.
Nothing overly of note this week
Vulnerability
Our attack surface.
Ivanti: Security Update: Pulse Connect Secure, Ivanti Connect Secure, Policy Secure and Neurons for ZTA Gateways
Invanti warn..
Customers have a significantly reduced risk from this vulnerability if they are running appliances on supported versions and in accordance with Ivanti's guidance:
This vulnerability was fully patched in Ivanti Connect Secure 22.7R2.6 (released February 11, 2025).
Ivanti Policy Secure should not be an internet facing solution. Users that follow Ivanti’s guidance regarding internet exposure are at a reduced risk from this vulnerability.
Neurons for ZTA gateways cannot be exploited when in production.
We are aware of a limited number of customers whose appliances have been exploited and are running Ivanti Connect Secure 22.7R2.5 or earlier or Pulse Connect Secure 9.1x.
Offense
Attack capability, techniques and trade-craft.
Browser Cache Smuggling: the return of the dropper
Aurelien Chalot details a technique it will be interesting see how quickly browser vendors respond to..
A year and a half ago I wrote a blog post describing how browsers’ cache system can be abused to drop malware on targets’ computers. As of today, this technique is still relevant. Browsers haven’t changed their behaviour and as such you can still use it for red team assessments.
I had the opportunity to present the technique at Insomni’hack 2025 and while the technique itself is, I believe, quite interesting, I wanted to go a little further and:
Weaponise the entirety of the technique to prove it’s impact and why you should care about it;
Present ways you can detect and protect yourself against it.
So without further ado, let’s dive into the Browser Cache Smuggling attack one more time!
https://sensepost.com/blog/2025/browser-cache-smuggling-the-return-of-the-dropper/
DocEx
DarkSpace Security give a capability which you may want to ensure you have detection coverage of.
APT Emulation tool to exfiltrate sensitive .docx, .pptx, .xlsx, .pdf files not detected by Defender of MDE
https://github.com/DarkSpaceSecurity/DocEx
Exploitation
What is being exploited..
CVE-2025-22457: Suspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability
John Wolfram, Michael Edie, Jacob Thompson, Matt Lin and Josh Murchie detail alleged Chinese exploitation of this zero-day.
On Thursday, April 3, 2025, Ivanti disclosed a critical security vulnerability, CVE-2025-22457, impacting Ivanti Connect Secure (“ICS”) VPN appliances version 22.7R2.5 and earlier. CVE-2025-22457 is a buffer overflow vulnerability, and successful exploitation would result in remote code execution. Mandiant and Ivanti have identified evidence of active exploitation in the wild against ICS 9.X (end of life) and 22.7R2.5 and earlier versions. Ivanti and Mandiant encourage all customers to upgrade as soon as possible.
The earliest evidence of observed CVE-2025-22457 exploitation occurred in mid-March 2025. Following successful exploitation, we observed the deployment of two newly identified malware families, the TRAILBLAZE in-memory only dropper and the BRUSHFIRE passive backdoor.
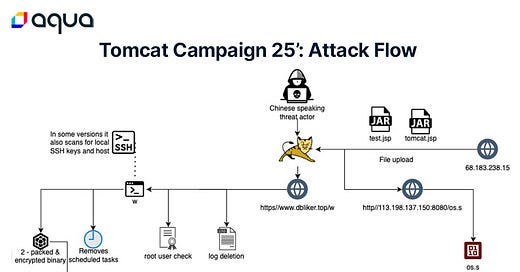
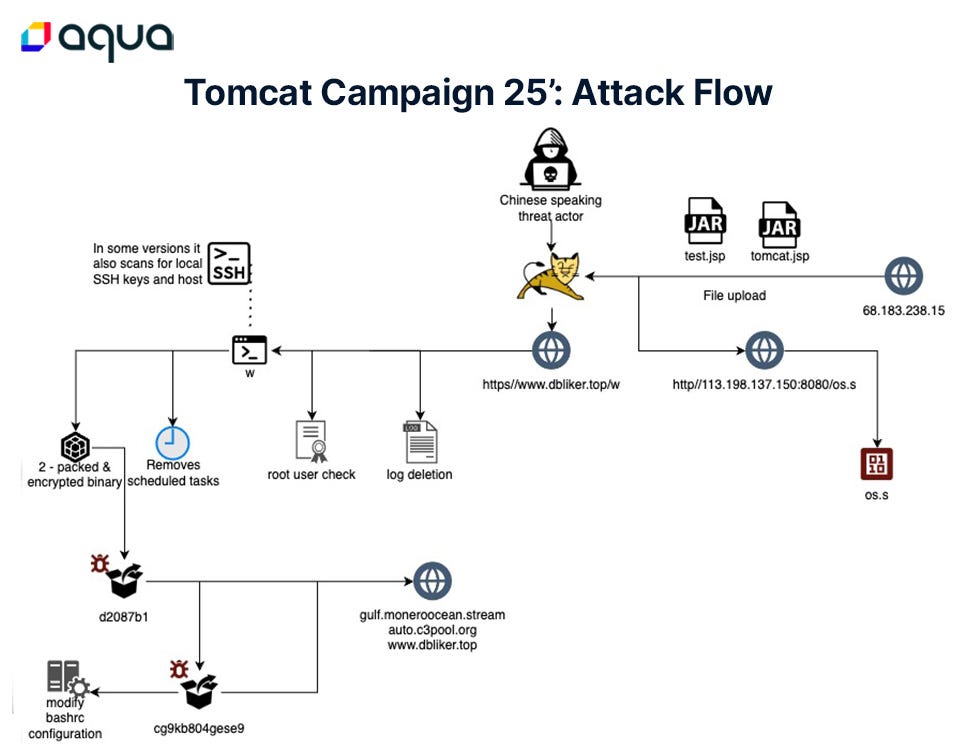
Tomcat in the Crosshairs
Assaf Morag details the attack chain seen in this exploitation.
News headlines reported that it took just 30 hours for attackers to exploit a newly discovered vulnerability in Apache Tomcat servers.
https://www.aquasec.com/blog/new-campaign-against-apache-tomcat/
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Ghidra MCP
Laurie Wired gives is agentic AI integration for Ghidra (risks previously mentioned not withstanding)…
ghidraMCP is an Model Context Protocol server for allowing LLMs to autonomously reverse engineer applications. It exposes numerous tools from core Ghidra functionality to MCP clients.
https://github.com/LaurieWired/GhidraMCP
IDA Pro MCP
Duncan Ogilvie gives us agentic integration for IDA Pro (risks previously mentioned not withstanding)…
Simple MCP Server to allow vibe reversing in IDA Pro.
https://github.com/mrexodia/ida-pro-mcp
OLLVM Unflattener
Chuong Dong shows the art of the possible against the perceived impossible..
OLLVM (Obfuscator-LLVM) is a popular code obfuscation tool that implements various obfuscation techniques, including control flow flattening on the function level. Control flow flattening transforms the original flow of a function into a flat structure using a state variable and a dispatch mechanism, making it difficult to understand the program's logic during the reverse engineering process.
This tool:
Reconstructs the original control flow of an obfuscated function by identifying and connecting basic blocks
Generates a deobfuscated binary with the original control flow restored
Supports multi-layered function deobfuscation by following calls made by the target function using breadth-first search (BFS)
Supports deobfuscation for Windows & Linux binaries for both x86 and x64 architectures
https://github.com/cdong1012/ollvm-unflattener
Code reuse in the age of kCET and HVCI
Slowerzs shows that some kernel exploitation primitives still exist.
The addition of kCET makes techniques such as KernelForge non-functionnal, which would craft a ROP chain on the stack of a dummy thread to chain arbitrary function calls.
..
While kCET seems pretty robust, kCFG is not as robust as Intel IBT, the hardware implementation of forward-edge CFI. As such, techniques like Jump-Oriented Programming (JOP) can get around kCET, but the first gadget in the chain is unlikely to be a valid call target. Therefore, we need to get around kCFG once, afterwards, it is no longer a concern during the execution of the JOP chain.
kCFG can only maintain the integrity of the control flow if every call site is instrumented. In practice however, in the Windows kernel, it is not uncommon to find unprotected calls or jumps.
https://blog.slowerzs.net/posts/keyjumper/
Protecting linear address translations with Hypervisor-enforced Paging Translation (HVPT)
Hilal Asmat details how this mitigation works.
One of our latest silicon-assisted security features that went live recently is called Hypervisor-enforced Paging Translation (HVPT). HVPT is an innovative new feature that leverages the power of Windows Hyper-V to help protect guest virtual address (GVA) to guest physical address (GPA) translation with the goal of protecting against 2 page-table-targeted attacks, known as aliasing and remapping attacks. HVPT can help protect the root OS as well as guest VMs running atop it. In this blog, we will cover the attacks HVPT is designed to help protect against, and dive into how HVPT helps protects GVA to GPA translations.
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Information security manual - Australia - March 2025
Artificial intelligence
Model Context Protocol (MCP): Landscape, Security Threats, and Future Research Directions
Graph neural networks extrapolate out-of-distribution for shortest paths
Symbolic Mixture-of-Experts: Adaptive Skill-based Routing for Heterogeneous Reasoning
Exploring Data Scaling Trends and Effects in Reinforcement Learning from Human Feedback
Books
Nothing of note this week
Events
Real World Crypto 2025 - Videos
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.