CTO at NCSC Summary: week ending August 3rd
NCSC offers bespoke guidance to support practitioners working with victims of technology-facilitated domestic abuse, stalking & harassment.
Welcome to the weekly highlights and analysis of the blueteamsec Lemmy (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note…
In the high-level this week:
Guidance for practitioners supporting victims of technology-facilitated domestic abuse - NCSC UK publish - “Working in partnership with charities, law enforcement, and independent domestic violence advisors, the NCSC offers bespoke guidance to support practitioners working with victims of technology-facilitated domestic abuse, stalking & harassment.”
Inside the UK’s Cyber Strategy: - NCSC’s Richard Horne on Resilience, Risk, and AI - McCrary Institute vodcasts
NCSC and CERT NZ integration now complete - NCSC NZ publish - “Reporting cyber security incidents and understanding how to withstand the cyber threats facing New Zealand is now easier with the completion of the integration of CERT NZ with the National Cyber Security Centre (NCSC).”
From Georgia to Ukraine: Seventeen Years of Russian Cyber Capabilities at War - West Point Modern War Institute release - “In the weeks leading up to the Russo-Georgian War, Russian hackers attacked Georgia’s digital ecosystem to sow chaos within the Georgian government and society as Russian troops were amassing along the northern border. This marked the dawn of modern hybrid or gray zone warfare, which blends conventional military force with unconventional tactics, such as cyberattacks.”
Naming country linked to UNC3886 attack not in Singapore’s best interest at this point in time: Shanmugam - Channel News Asia reports - “The decision to identify cyber threat group UNC3886 was because Singaporeans “ought to know about it” given the seriousness of the threat, said the minister.”
More than 90 state, local governments targeted using Microsoft SharePoint vulnerability, group says - Reuters reports - "None have resulted in confirmed security incidents," Randy Rose, the center's vice president of security operations and intelligence, said in an email.
CISA and USCG Issue Joint Advisory to Strengthen Cyber Hygiene in Critical Infrastructure - CISA publishes - ”During this engagement, CISA and USCG did not find evidence of malicious cyber activity or actor presence on the organization’s network but did identify several cybersecurity risks. CISA and USCG are sharing their findings and associated mitigations to assist other critical infrastructure organizations identify potential similar issues and take proactive measures to improve their cybersecurity posture.”
Huawei, at the heart of the Post outage - Paperjam reports - “The hackers who targeted Post--and indirectly Luxembourg--a week ago are believed to have attacked Huawei routers and their operating software. These are routers that in particular enable connection to European financial centres, from London to Paris, via Frankfurt or Amsterdam, according to two sources.”
Russia launches an Iranian communications satellite into orbit - AP News reports - “A Russian rocket sent an Iranian communications satellite into orbit Friday, a launch that highlighted strong ties between the two countries.”
Reporting on/from China
Chinese hackers have seized control. How did we let this happen? - The Telegraph reports - “An official advisory was recently sent out to the US military, warning that all forces must now assume their networks have been breached. “
Microsoft Probing If Chinese Hackers Learned SharePoint Flaws Through Alert - Bloomberg reports - “The technology company is looking into whether the program — designed to give cybersecurity experts a chance to fix computer systems before the revelation of new security concerns — led to the widespread exploitation of vulnerabilities in its SharePoint software globally over the past several days, the people said, asking not to be identified discussing private matters.”
China’s tech hub Shenzhen mandates leniency for innovators whose state-funded projects fail - South China Morning Post reports - “The new rules applied to all universities, hospitals and companies that undertake technical innovation with government financial aid, the commission said in a statement on its website last Monday.”
Chinese Crypto Giant Bitmain Plans US Factory in Trump-Era Push - Bloomberg reports - “the world’s largest manufacturer of crypto mining hardware, plans to open its first US facility in the coming months, a strategic pivot riding the “Made in America” boom in digital assets.”
Does China Actually Need Yuan Stablecoins? - Caixin Global explores - “For instance, stablecoin issuance must be conducted on a public blockchain, but existing public blockchains are developed by crypto issuers, none of which are based on the mainland. Therefore, some have suggested that state-owned enterprises should take the lead in building China’s own public blockchains.”
Fintech Adoption: Progress and Future Directions - Hong Kong Monetary Authority publishes - “the adoption of sophisticated, infrastructure-level technologies like High-Performance Computing is still in exploratory phases across the banking sector, with 23% of institutions actively piloting these solutions. Representing a frontier area”
China-Africa economic and trade cooperation adds impetus to the sustainable development of the world economy - Guangming Daily reports - ”the Fourth China-Africa Economic and Trade Expo, themed "China and Africa Acting Together, Pursuing the Dream of Modernization," was held in Changsha”
Discipline and Resistance: The Construction of a “Digital Home” for TikTokRefugeeson Xiaohongshu - The Chinese University of Hong Kong researches - “examines how “TikTok refugees” moved to Xiaohongshu after TikTok was about to be banned in the United States. It utilizes Foucault’s idea of heterotopia to demonstratehow Xiaohongshu became a crisis space for cross-cultural discussions across the Great Firewall.”
TikTok owner ByteDance debuts robotic system in latest AI development - South China Morning Post reports - “In a separate technical report, the development team said the robot could handle short-sleeved clothes even though “all the clothes in the training data were long-sleeved”.”
AI
GenAI Code Security Report - Veracode researches - “Across all models and all tasks, only 55% of generation tasks result in secure code. In other words, in 45% of the tasks the model introduces a known security flaw into the code.”
Promoting the export of the America AI technology stack - The White House announces - “It is the policy of the United States to preserve and extend American leadership in AI and decrease international dependence on AI technologies developed by our adversaries by supporting the global deployment of United States-origin AI technologies.”
China’s Li Qiang calls for global AI centre as US tech rivalry intensifies - South China Morning Post reports - “Without directly mentioning the US, Li warned that AI, which required high concentrations of technology, capital and talent, could become an “exclusive game” for a select few nations and companies that control critical resources.”
China’s Overlooked AI Strategy - Foreign Affairs reports - “But the threat posed by Chinese open models is not simply about China catching up to the United States in the AI race. It is also about the broader global adoption of AI. For the month of January 2025, the DeepSeek R1 app had 33 million active users across the world; by April, that number had nearly tripled to 97 million.”
Cyber proliferation
Nothing overly of note this week..
Bounty Hunting
University student who sold phishing kits to fraudsters jailed - UK Crown Prosecution Service announces - “He was sentenced at Southwark Crown Court to seven years imprisonment on Wednesday, 23 July 2025. He was also given a Serious Crime Prevention Order following an application from the prosecution.”
Illumina Inc. to Pay $9.8M to Resolve False Claims Act Allegations Arising from Cybersecurity Vulnerabilities in Genomic Sequencing Systems - US Department of Justice announce - “The settlement resolves allegations that, between February 2016 and September 2023, Illumina sold government agencies genomic sequencing systems with software that had cybersecurity vulnerabilities, without having an adequate security program and sufficient quality systems to identify and address those vulnerabilities.”
Polish Train Maker Is Suing the Hackers Who Exposed Its Anti-Repair Tricks - IFIXIT reports - “In total, the two lawsuits seek the equivalent of over $3 million USD.”
Clorox versus Cognizant Complaint - Clorox files, claims and alleges - “For over a decade, Clorox entrusted Cognizant, a self-proclaimed leader in digital and cybersecurity services, to play critical roles in Clorox’s cyber environment…. Cognizant’sconduct on August 11, 2023, demonstrated spectacularly that it was failing to do so. Cognizant repeatedly gave a cybercriminal access to Clorox’s network by handing them credentials without properly authenticating them or otherwise following Clorox’s process.” - includes call transcript..
The Illumina Inc settlement above led to this weeks reflections.. They are based on a version (or part of) of a futures talk I give internally as well as externally…
It goes along the lines of - there is a future where cyber security will meet biology in a hybrid world. This will be for a whole host of reasons and we will likely benefit from being prepared. If we want evidence that this future is a possibility then we should look at:
DNA data storage and the recently initiated project to make Synthetic DNA as Mass Data Storage of the Future by Fraunhofer.
DNA computing and the first attempts to productise. by DNA Ascendancy.
Cortical Labs and their foundational dish brain work from 2022 and their synthetic neurons in the cloud which you will be able to interact with via Python via an FPGA.
Then we have Two-way adaptive brain-computer interfaces (BCI) by Chinese scientists i.e. interacting via the brain via a two way interface and not just passively monitoring..
It finishes with… it might all sound a little Black Mirror but there are those who really are trying to take make these technologies a reality. Given this, how do we learn from our experiences of a silicon powered software world and cyber security? It starts with recognising this future in cyber security will be more multi-disciplinary and not less…
Not getting this via email? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Friday…
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Frozen in transit: Secret Blizzard’s AiTM campaign against diplomats
Microsoft details this alleged Russian operation which relies on a degree of sophistication at various levels in order to achieve. Looking for unexpected root certificates is a strong TTP.
Microsoft Threat Intelligence has uncovered a cyberespionage campaign by the Russian state actor we track as Secret Blizzard that has been targeting embassies located in Moscow using an adversary-in-the-middle (AiTM) position to deploy their custom ApolloShadow malware. ApolloShadow has the capability to install a trusted root certificate to trick devices into trusting malicious actor-controlled sites, enabling Secret Blizzard to maintain persistence on diplomatic devices, likely for intelligence collection.
Reporting on China
China’s Covert Capabilities | Silk Spun From Hafnium
Dakota Cary details new capabilities which belong to an alleged Chinese threat actor.
SentinelLABS identified 10+ patents for highly intrusive forensics and data collection technologies that were registered by companies named in U.S. indictments as working on behalf of the Hafnium threat actor group.
These technologies offer strong, often previously unreported offensive capabilities, from acquisition of encrypted endpoint data, mobile forensics, to collecting traffic from network devices.
Our research explores the relationships between indicted hackers, ownership of the firms they are associated with, and the relationships those firms have with several government entities who conduct offensive cyber operations on behalf of China.
https://www.sentinelone.com/labs/chinas-covert-capabilities-silk-spun-from-hafnium/
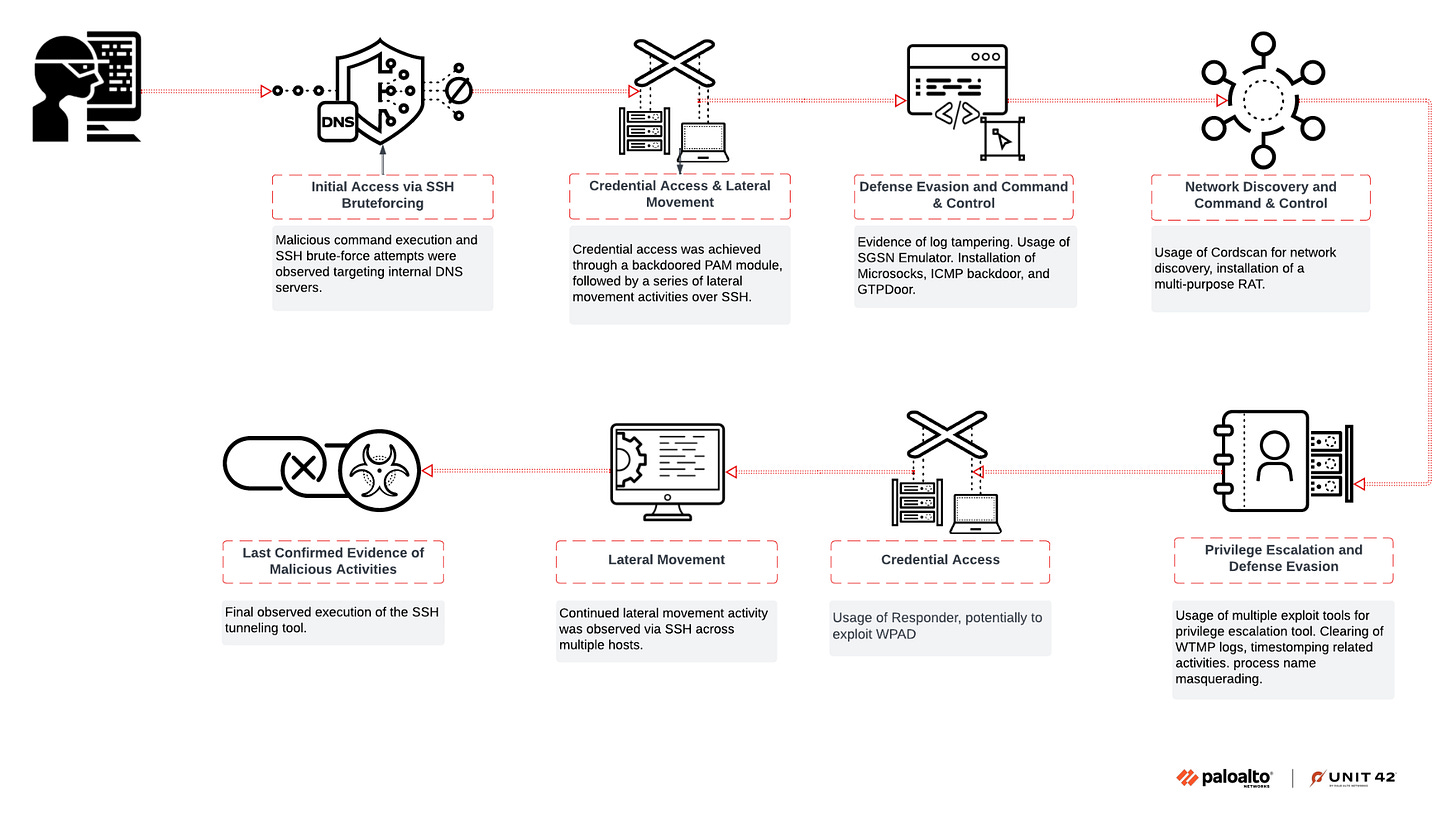
The Covert Operator's Playbook: Infiltration of Global Telecom Networks
Palo Alto details a campaign which whilst they do not name China link to a range of third party reporting and/or use names of activity previously alleged by others to be. Most interesting is they detail some of the initial access tradecraft.
We found no clear evidence of data collection or exfiltration from the investigated systems and networks, nor any attempts to track or communicate with target devices within mobile networks. However, the threat actor behind CL-STA-0969 maintained high operational security (OPSEC) and employed various defense evasion techniques to avoid detection.
With high confidence, we assess this activity is associated with a nation-state nexus. Based on observed activity and victimology, this cluster heavily overlaps with activity attributed to Liminal Panda, a nation-state adversary tracked by CrowdStrike.
https://unit42.paloaltonetworks.com/infiltration-of-global-telecom-networks/
Fire Ant: A Deep-Dive into Hypervisor-Level Espionage
Sygnia detail what is loosely alleged to be Chinese in origin that is notable to a degree of operational discipline and capability to move latterly.
After re-compromising assets, the threat actor rotated the deployed toolsets, altered execution methods, and renamed binaries to avoid detection.
..
Fire Ant moved laterally by compromising infrastructure components that naturally bridge network boundaries. By tunneling through trusted services and pivoting from one network to another via legitimate paths, the threat actor reached highly restricted environments while evading traditional ACLs, firewall policies, and segmentation controls. By bridging these segmented environments, the threat actor gained the ability to operate freely within networks that were otherwise considered secure and trusted, effectively collapsing internal trust boundaries.
..
The active working hours of the threat group throughout the incidents and minor input errors observed during command execution aligned with Chinese-language keyboard layouts, consistent with prior regional activity indicators.
https://www.sygnia.co/blog/fire-ant-a-deep-dive-into-hypervisor-level-espionage/
When Privileged Access Falls into the Wrong Hands: Chinese Companies in Microsoft’s MAPP Program
Eugenio Benincasa, Dakota Cary, and Natto Team research and document the programme whilst highlight a subset of local legislation which creates likely conflict.
Chinese companies operating within MAPP present a unique risk due to national regulations mandating the disclosure of vulnerabilities to the state. In September 2021, China implemented the Regulations on the Management of Network Product Security Vulnerabilities (RMSV), which require any organization doing business in China to report newly discovered zero-day vulnerabilities to government authorities within 48 hours. This gives Chinese state agencies early access to high-impact vulnerabilities – often before patches are available.
nattothoughts.substack.com/p/when-privileged-access-falls-into
Reporting on North Korea
How North Korea-Backed Lazarus Group Is Weaponizing Open Source to Target Developers
Sonatype detail both the alleged scale of the campaign but also the potential scale of the impact of this alleged North Korean operation. The ability for these library distribution platforms to protect themselves and their uses is becoming paramount..
Since January 2025 alone, [we] uncovered and blocked 234 unique open source malware packages that can be attributed to the North Korea-backed Lazarus Group
..
While each package alone may appear unremarkable, taken together they reveal a sophisticated strategy of deception, persistence, and exploitation with over 36,000 potential victims.
Reporting on Iran
Nothing overly of note this week..
Reporting on Other Actors
Scattered Spider Advisory
FBI, CISA and friends assemble with this advisory..
The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Royal Canadian Mounted Police (RCMP), Australian Signals Directorate’s (ASD’s) Australian Cyber Security Centre (ACSC), Australian Federal Police (AFP), Canadian Centre for Cyber Security (CCCS), and United Kingdom’s National Cyber Security Centre (NCSC-UK)—hereafter referred to as the authoring organizations—are releasing this joint Cybersecurity Advisory in response to recent activity by Scattered Spider threat actors against the commercial facilities sectors, subsectors, and other sectors. This advisory provides tactics, techniques, and procedures (TTPs) obtained through FBI investigations as recently as June 2025.
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-320a
PyPI Users Email Phishing Attack
The Python Package Index detail an unattributed phishing campaign against their supply base. The supply chain threat is real..
PyPI has not been hacked, but users are being targeted by a phishing attack that attempts to trick them into logging in to a fake PyPI site.
Over the past few days, users who have published projects on PyPI with their email in package metadata may have received an email titled:
https://blog.pypi.org/posts/2025-07-28-pypi-phishing-attack/
Microsoft OAuth App Impersonation Campaign Leads to MFA Phishing
Proofpoint detail a campaign that once again highlights yet another social engineering attack surface.
Threat actors are impersonating various enterprises with fake Microsoft OAuth applications to steal credentials.
These campaigns bypass multifactor authentication (MFA).
While many impersonate enterprise apps, some are customized to specific software used in targeted industries.
The fake Microsoft 365 applications impersonate various companies including RingCentral, SharePoint, Adobe, and DocuSign. Proofpoint first observed this activity in early 2025 and remains ongoing.
Attackers abusing Proofpoint & Intermedia link wrapping to deliver phishing payloads
Cloudflare provide evidence for phishing resistant authentication i.e. passkeys.
From June 2025 through July 2025, the Cloudflare Email Security team has been tracking a cluster of cybercriminal threat activity leveraging Proofpoint and Intermedia link wrapping to mask phishing payloads, exploiting human trust and detection delays to bypass defenses.
Link wrapping is designed by vendors like Proofpoint to protect users by routing all clicked URLs through a scanning service, allowing them to block known malicious destinations at the moment of click. For example, an email link to http://malicioussite[.]com might become https://urldefense[.]proofpoint[.]com/v2/url?u=httpp-3A__malicioussite[.]com. While this is effective against known threats, attacks can still succeed if the wrapped link hasn’t been flagged by the scanner at click time.
Recent campaigns observed by the Cloudflare Email Security team reveal how attackers are abusing Proofpoint’s and Intermedia’s link wrapping features to bypass detection and redirect victims to a variety of Microsoft Office 365 phishing pages.
Email-Delivered RMM: Abusing PDFs for Silent Initial Access
Jeremy Ong details a rather novel campaign which should be easy enough to detect. But also highlights why software controls are worth their weight in gold.
Since November 2024, WithSecure has been tracking a slight uptick of targeted activities leveraging Remote Monitoring and Management (RMM) tools embedded within PDF documents. The activity primarily targets organizations in France and Luxembourg, using socially engineered emails to deliver a clean PDF containing an embedded link to an RMM installer, a simple but effective method of bypassing many email and malware defences.
https://labs.withsecure.com/publications/email-delivered-rmm
Plague: A Newly Discovered PAM-Based Backdoor for Linux
Pierre-Henri Pezier gives a reality check..
What caught our attention: although several variants of this backdoor have been uploaded to VirusTotal over the past year, not a single antivirus engine flags them as malicious (see screenshot). To our knowledge, there are no public reports or detection rules available for this threat, suggesting that it has quietly evaded detection across multiple environments.
https://www.nextron-systems.com/2025/08/01/plague-a-newly-discovered-pam-based-backdoor-for-linux/
Discovery
How we find and understand the latent compromises within our environments.
Detecting ADCS Privilege Escalation
Alyssa Snow details how to detect if you enable auditing.. in short: enable auditing!
Misconfigurations in ADCS can introduce critical vulnerabilities into an enterprise Active Directory environment
By default, ADCS does not have auditing enabled. Enable ADCS auditing to detect ADCS exploitation.
https://www.blackhillsinfosec.com/detecting-adcs-privilege-escalation/
From IOC Whack-a-Mole to Hypothesis-Driven Sleuthing
Mat Cyb3rF0x Fuchs highlights what it takes to move from a world where you consume IoCs to one where you consume TTPs and the enact a detection plan off the back of it..
Threat hunting has come a long way from its humble beginnings of simple IOC lookups. It has matured into a hypothesis-driven, risk-aligned practice that not only finds hidden adversaries but also shines a light on an organization’s weaknesses. When done with skill and purpose, threat hunting can help drive security strategy: exposing where you’re blind, informing where to bolster defenses, and validating that your crown jewels are indeed safe from the tactics you fear most. It’s proactive cybersecurity at its finest — part detective work, part quality assurance, part continuous improvement.
LOTS Project Rework
Aura is back with this super useful rework..
The LOTS-Project website never had a CSV and/or JSON export of all its entries, making it hard to incorporate and/or use it in detection and/or threat hunting as an external entity, such as with KQL's externaldata(). Having it as a CSV (and maybe even a JSON someday?) will now make it possible to be used:
In languages such as KQL that supports the ingestion of external data format (CSV, JSON)
In solutions that supports the upload of custom tables, lookups, etc. that can be used for enrichment and/or lookup purposes (e.g.: Microsoft Sentinel, Splunk, etc.)
By scripts (e.g.: PowerShell or Python) that wants to use LOTS as a reference to lookup and/or match sites/domains with other sources (e.g.: audit logs, Web Proxy logs, etc.)
https://github.com/SecurityAura/DE-TH-Aura/tree/main/Data%20Sources/LOTS-Project-Rework
Hardware-Backed Telemetry for Detecting Out-Of-Context Execution
Matt Hand, Michael Barclay, Connor McGarr, Mitchell Turner, Tyler Holmwood, John Uhlmann, Robin Williams, Keith Robertson, Isaac Chen and Lewis Zimmerman details a technique which will be a super power when generally available in various solutions..
This paper introduces a novel paradigm for endpoint security by establishing an unavoidable chokepoint at the fundamental point of execution itself. Our system leverages low-level, hardware-assisted telemetry, including Last Branch Record (LBR) and Intel Processor Trace (IPT), correlated with OS context switch and Performance Monitor Interrupt (PMI) events. By observing the CPU directly, we can reliably observe the execution of code residing in private memory, a core attribute of contemporary threats. In response to that observation, the system generates a rich, graph-based representation of the event’s full provenance, mapping the inter-relationships between processes, threads, memory regions, and other artifacts to provide deep, actionable insights for security analysts. This approach moves beyond chasing the ever-changing symptoms of malware and instead focuses on the immutable essence of its execution, creating a more durable, proactive, and effective defense against the next generation of advanced threats.
https://info.preludesecurity.com/hubfs/Content/Closing%20the%20Execution%20Gap.pdf
Defence
How we proactively defend our environments.
Eviction Strategies Tool
CISA release this cyber super power..
ISA has developed and maintains the publicly accessible Eviction Strategies Tool to support cyber defenders during the containment and eviction phases of incident response (IR). The tool comprises:
Playbook-NG, a web application for next-generation operations; and
COUN7ER, a database of atomic post-compromise countermeasures mapped to adversary tactics, techniques, and procedures (TTPs).
Together, Playbook-NG and COUN7ER can assemble a systematic eviction plan that leverages distinct countermeasures to contain and evict a unique intrusion. CISA offers Playbook-NG and COUN7ER to the public under the MIT Open Source License to encourage development. CISA designed Playbook-NG and COUN7ER to substantially accelerate the creation of response plans and to assist defenders with tailored adversary eviction strategies
https://www.cisa.gov/resources-tools/resources/eviction-strategies-tool
No[one|thing] will be left behind — Manual guide to patch your the exiled SharePoint/Exchange server
Jang provides in Thai probably one of the more extreme patching strategies..
With the vulnerability related to DataSetSurrogateSelector , to completely fix it will require modifying many files.
Instead, I suggest fixing it by removing the Deserialization step that causes the error at ExcelDataSet.get_DataTable :
Above are just some of my most rudimentary suggestions on how to manually patch vulnerabilities in case there is no patch available.
Warren
Masayoshi Mizutani hints at the future of AI enabled security operations and analyst augmentation with this release.
Warren is an open-source security alert management system that automates the tedious parts of alert triage. It ingests alerts from your existing tools, enriches them with AI and threat intelligence, and helps you focus on actual incidents instead of noise.
https://github.com/secmon-lab/warren
https://zenn.dev/mizutani/articles/secmon-warren
Microsegmentation in Zero Trust Part One: Introduction and Planning
CISA provide an important guide for zero trust in practice..
Microsegmentation can be applied to any technology environment, such as information technology (IT), operational technology (OT), industrial control system (ICS), internet of things (IoT), as well as any implementation model, including cloud, on premise and hybrid. Microsegmentation enables applying risk- and threat-appropriate protections and visibility capabilities for the specific system(s) or data within the microsegment. Microsegmentation can significantly enhance the security of systems and data and helps reduce the blast area that a compromised resource can impact.
https://www.cisa.gov/sites/default/files/2025-07/ZT-Microsegmentation-Guidance-Part-One_508c.pdf
Incident Writeups & Disclosures
How they got in and what they did.
Important Security Update Regarding the OP1w 4k v2 Configuration Tool
Endgame Gear detail an incident which will be of concern to some..
we are issuing this statement to inform you of an isolated security incident involving a malware-infected version of our Configuration Tool for the OP1w 4k v2 mouse. This compromised file was distributed unnoticed via the OP1w 4k v2 product page on our brand store between June 26th to July 9th on this domain only: www.endgamegear.com/gaming-mice/op1w-4k-v2.
What happened: During the period of June 26th to July 9th, a version of the Configuration Tool for the Endgame Gear OP1w 4k v2 wireless mouse, available for download on the OP1w 4k v2 product page, was found to contain malware. We have since removed the infected file.
https://www.endgamegear.com/security-update
Vulnerability
Our attack surface.
Node-SAML SAML Signature Verification Vulnerability
Be interesting to see the long tail / impact of this..
Node-SAML loads the assertion from the (unsigned) original response document. This is different than the parts that are verified when checking signature.
This allows an attacker to modify authentication details within a valid SAML assertion. For example, in one attack it is possible to remove any character from the SAML assertion username.
To conduct the attack an attacker would need a validly signed document from the identity provider (IdP).
In fixing this we made sure to process the SAML assertions from only verified/authenticated contents. This will prevent future variants from coming up.
Note: this is distinct from the previous xml-crypto CVEs.
https://github.com/node-saml/node-saml/security/advisories/GHSA-4mxg-3p6v-xgq3
SRAM Has No Chill: Exploiting Power Domain Separation to Steal On-Chip Secrets
Jubayer Mahmod and Matthew Hicks shows the person who understand how the hardware works in practice is able to achieve what others would deem impossible.
While SRAM protects against traditional cold boot attacks, we show that there is another way to retain information in on-chip SRAM across power cycles. This paper presents Volt Boot, an attack that demonstrates a vulnerability of on-chip SRAM due to the physical separation common in modern system-on-chip power distribution networks. Volt Boot leverages asymmetrical power states (for example, on vs. off) to force SRAM state retention across power cycles, eliminating the need for traditional cold boot attack enablers, such as low-temperature or intrinsic data retention time. Using three modern ARM Cortex-A SoCs, we demonstrate the effectiveness of the attack in caches, registers, and iRAMs. Unlike other forms of SRAM data retention attacks, Volt Boot retrieves data with 100% accuracy—without any complex post-processing
Tracing Bugs Across Kernels: SMB Vulnerabilities in macOS and FreeBSD
Tielei Wang shows the way of the experienced vulnerability researcher with this case study. Variant discovery and resolution by vendors is a common capability gap for most.
I’ll walk through a vulnerability in macOS’s in-kernel SMB client that led me to a related issue in FreeBSD. The two systems share a common SMB implementation, originally written for FreeBSD and later imported by Apple. By analyzing how code is inherited and reused across platforms, we can uncover bugs that are otherwise easy to overlook.
Traditional vulnerability discovery techniques like fuzzing are powerful but have limitations. For the two vulnerabilities discussed here, simple fuzzing alone would likely struggle to find the issues because the exploit conditions are quite specific:
In the macOS case, the file descriptor must correspond to a device node with an overly large minor number—something that normal usage or random fuzzing inputs rarely produce.
In the FreeBSD case, the file descriptor must refer to a valid, open device file that supports
devfs_get_cdevpriv(), but actually be of the wrong device type, which is a subtle state unlikely to be reached by blind fuzzing.These constraints mean the vulnerabilities are “hidden” in uncommon or unexpected scenarios that require understanding the kernel’s internal assumptions and device handling semantics.
By contrast, cross-codebase variant analysis leverages knowledge of code inheritance and architectural similarities across platforms.
https://github.com/wangtielei/Slides/blob/main/SMB_Vulnerability_Analysis.md
Offense
Attack capability, techniques and trade-craft.
Modular PIC C2 Agents
Rasta Mouse shows how memory implant components and framework approaches are evolving..
I have demonstrated how multiple PICOs can be loaded into memory by a reflective loader; configured to accept parameters and return data; and how to dynamically patch data into them at link-time. I hope you can visualise how such an architecture can be extended to build a modular C2 agent.
https://rastamouse.me/modular-pic-c2-agents/
related he also released A small collection of Crystal Palace PIC loaders designed for use with Cobalt Strike
https://github.com/rasta-mouse/Crystal-Loaders
Escaping the Confines of Port 445
Costa Papadatos shows how Windows complexity still has edges to be found which enable relay attacks in ways not expected.
NTLM relay attacks on SMB restrict lateral movement to port 445/TCP capabilities. To extend beyond, leverage the Service Control Manager (SCM) remotely to initiate the Webclient service. This approach allows integration with computer account takeover methods such as shadow credentials or resource-based constrained delegation (RBCD), enhancing attack flexibility through the LDAP service targeting domain controllers (DCs).
https://specterops.io/blog/2025/07/24/escaping-the-confines-of-port-445-ntlm-relay/
Ghosting the Sensor: Disrupting Defender for Identity Without Detection
Elli Shlomo details a technique to be aware of..
DNS layer sensor disruption offers a powerful and stealthy method of evading Microsoft Defender for Identity telemetry without stopping services, altering binaries, or triggering local tampering alerts
https://cyberdom.blog/ghosting-the-sensor-disrupting-defender-for-identity-without-detection/
Macro-header for compile-time C obfuscation
DosX, Hors and EvoX show a capability which could be ported to other operating systems and by doing so impose cost on traditional reverse engineering..
obfus.h is a macro-only library for compile-time obfuscating C applications, designed specifically for the Tiny C (tcc). It is tailored for Windows x86 and x64 platforms and supports almost all versions of the compiler. Very reliable armor for your C programs!
https://github.com/DosX-dev/obfus.h
Hells Hollow: A new SSDT Hooking technique
flux releases code which will have a variety of uses both good and bad..
Hells Hollow is my name for a technique which has come about from my research into Alt Syscalls. In that post, I explained how when using the Alt Syscalls technique (for defensive EDR purposes) you must always return 1. This time, we are going to return something else and start messing with the Operating System, allowing you to hook and modify the actual KTRAP_FRAME of all syscalls (not just a copy of the trap).
Whilst in this post we focus on ETW, Hells Hollow can be used in any number of creative ways - this name can describe any number of malicious activities we can conduct via this technique, essentially, a SSDT bypass for rootkits that Microsoft managed to defeat via PatchGuard, for Windows 11.
https://fluxsec.red/hells-hollow-a-new-SSDT-hooking-technique-with-alt-syscalls-rootkit
Ring Reaper
Matheuz and Brosck those protecting and detecting within Linux estates will want to ensure coverage of.
RingReaper is a simple post-exploitation agent for Linux designed for those who need to operate stealthily, minimizing the chances of being detected by EDR solutions. The idea behind this project was to leverage io_uring, the new asynchronous I/O interface in the Linux kernel, specifically to avoid traditional system calls that most EDRs tend to monitor or even hook.
https://github.com/MatheuZSecurity/RingReaper
Exploitation
What is being exploited..
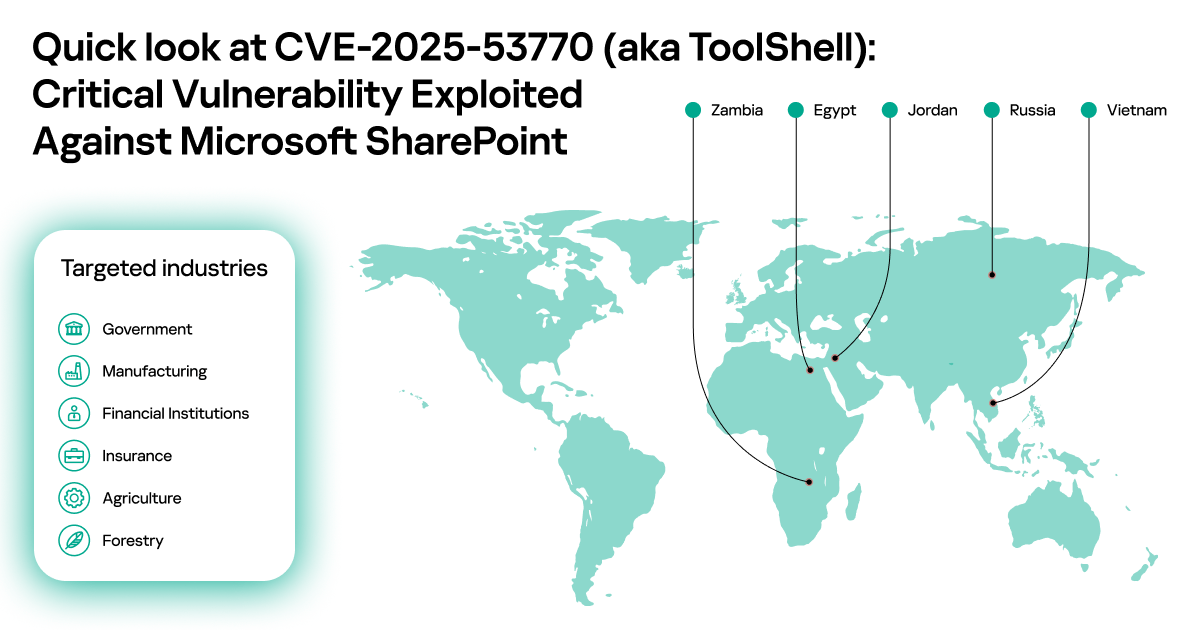
ToolShell
A story of five vulnerabilities in Microsoft SharePoint
Boris Larin, Georgy Kucherin and Ilya Savelyev provide some insights into victimology in a subset of geographies..
https://securelist.com/toolshell-explained/117045/
SentinelOne also noted an interesting fact..
first observed ToolShell exploitation on July 17th, ahead of official Microsoft advisories. Since then, we’ve identified three distinct attack clusters, each with unique tradecraft and objectives.
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
NtCreateFile to craft a raw TCP socket via AFD.sys on Windows 11
Mateusz Lewczak details a technique that detection engineers will want to be aware of..
The first reason for talking directly to
AFD.sysinstead of going through Winsock is to dodge the hooks used by some protection systems - like anti-cheat or anti-malware (though the latter usually rely on NDIS filters in kernel mode).
https://leftarcode.com/posts/afd-reverse-engineering-part1/
Process Injection using Return-Oriented Programming
Bramwell Brizendine, Shiva Shashank Kusuma and Bhaskar P. Rimal add a degree of complexity for detection engineers..
We show how to generalize a complex exploit chain that invokes advanced malicious functionality consisting of multiple function calls that are made using only ROP. We generalize this approach by creating a library of nearly 150 parameter-loading patterns, thereby making process injection as a complete ROP technique portable across multiple, dissimilar binaries. Previously, only a few APIs were documented with parameter-loading patterns, making advanced ROP techniques on Windows less straightforward. Experimental validation on several Windows builds confirms our approach is reliable on the modern Windows operating system. This work advances the state-of-the-art in offensive security, offering a foundation for future research, both defensively and in software exploitation.
https://ieeexplore.ieee.org/stamp/stamp.jsp?arnumber=11095694
AntiDebug
axxo1337, Sambor, Matteo M and Kapitche release this work aid..
A simple terminal interface tool to test Windows x86_64 anti-debugging techniques.
https://github.com/haxo-games/AntiDebug
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Annual, quarterly and monthly reports
The vanishing watchman: the rise and decline of early warning
What the Israel-Iran conflict revealed about wartime cyber operations
Artificial intelligence
Books
Noting overly of note this week
Events
‘Objective for the We' v3.0 - Slides and videos
BSides Bournemouth - August 16th - see you there!
Finally I did a podcast with Ian L Paterson which you can see/listen to here..
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.