Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week and thankfully over Christmas nothing overly of note beyond the usual tempo.
In the high-level this week:
Gloucester City Council: Managing a cyber attack - This case study is based on the first hand experiences of key staff at the council of dealing with the cyber attack. It includes a timeline of the attack, its impact, the recovery process, the cost of the incident, and the lessons learnt by the council.
First filing under new US SEC rules - [we] detected unauthorized occurrences on a portion of its information technology (IT) systems. Upon detecting the unauthorized occurrences, the Company immediately began taking steps to contain, assess and remediate the incident, including beginning an investigation with leading external cybersecurity experts, activating its incident response plan, and shutting down some systems. The threat actor disrupted the Company’s business operations by encrypting some IT systems, and stole data from the Company, including personal data.
Lapsus$: GTA 6 hacker handed indefinite hospital order - much reporting on this as the supposed use of a Firestick in a hotel room to compromise a number of targets.
The [UK Government] Cyber Security Standard - The cyber security standard supports Government Functional Standard GovS 007: Security. GovS 007 sets out expectations and reasons for the security activities which organisations need to carry out to protect government assets. The cyber security standard defines the cyber security outcomes which organisations must meet and the assurance process which they must follow - this relates to GovAssure
2023 CBEST thematic - The annual UK Financial Services Red Team) thematic is intended to inform the sector on our findings and lessons learned - As regulators, we observe the whole-of-organisation effort required for firms/FMIs to remain resilient. This includes highly technical staff, ordinary users, and external-facing staff.
Cybersecurity Maturity Model Certification Program Proposed Rule Published - CMMC is designed to ensure that defense contractors and subcontractors are compliant with existing information protection requirements for federal contract information (FCI) and controlled unclassified information (CUI) and are protecting that sensitive unclassified information at a level commensurate with the risk from cybersecurity threats, including advanced persistent threats.
[US DoD] Cybersecurity Maturity Model Certification (CMMC) Program Guidance - The Department of Defense announces the availability of eight guidance documents for the CMMC Program. These documents provide additional guidance for the CMMC model, assessments, scoring, and hashing.
The first UK-EU Cyber Dialogue takes place in Brussels - Officials exchanged views on policies for secure technology, digital identity and cyber resilience, as well as deterrence strategies against cyber threats, cyber sanctions, and capacity building.
Cyber Rapid Response Teams Structure, Organization, and Use Cases - Multinational rapid response teams remain much more of an idea than a reality. Although in the past year, the EU CRRT has begun deploying teams to Moldova and Mozambique, it has done so proactively rather than reactively. In neither case was the CRRT responding to an acute, ongoing crisis. Instead, the CRRT teams conducted vulnerability assessments and other general cyber defense support assignments.
Action against digital skimming reveals 443 compromised online merchants - lots of countries involved here led by EuroPol.
Disgruntled Cloud Engineer Sentenced To Two Years In Prison - For Intentionally Damaging His Former Employer’s Computer Network After He Was Fired
Kazakhstan extradites to Russia a hacker who gained unauthorized access to company data - the USA had requested his extradition there instead.
Is It Raining Risk? What Data says about Cyber Risk in the Cloud
This graph says revenue correlates to level of security..
US and EU look for common ground on digital identity - Jointly authored by a subgroup within the EU-US Trade and Technology Council, the draft version of the Digital Identity Mapping Exercise Report aims to help define specific technical terminology related to digital identity in a transatlantic setting.
Nothing is certain but death and taxes (unless you get hacked): An international law perspective on Ukraine’s cyber attack against Russia’s Federal Tax Service - a permissive interpretation one might be tempted to endorse today may well have considerable detrimental effect on one’s own civilian population in a conflict tomorrow
Don’t ban payments to ransomware gangs, cyber experts say - around 74 percent of the experts who answered our survey were anti-ban. The rest said they favored a ban - underlying sample size not reported.
Findings and Updates from CISA’s Ongoing Collaboration with Education Technology Vendors to Address K-12 Cybersecurity Challenges - vendor security teams need further investment in tooling, training personnel, user experience, and secure software methodologies, all of which stem from executive-level business decisions.
FTC Proposes Strengthening Children’s Privacy Rule to Further Limit Companies’ Ability to Monetize Children’s Data - Proposed COPPA Rule would require targeted advertising to be off by default, limit push notifications, restrict surveillance in schools, and strengthen data security
Manuel Suter becomes deputy director of the new [Swiss] Federal Cybersecurity Office (BACS) - Due to the increasing importance of cybersecurity and thus of the NCSC, the Federal Council decided on December 2, 2022 to transfer the NCSC to a federal office and to locate it in the Federal Department of Defense, Civil Protection and Sport (DDPS).
EU on harmonised rules on fair access to and use of data and amending Regulation (EU) 2017/2394 and Directive (EU) 2020/1828 (Data Act) - This Regulation ensures that users of a connected product or related service in the Union can access, in a timely manner, the data generated by the use of that connected product or related service and that those users can use the data, including by sharing them with third parties of their choice.
Defending Democracy
What to do about disinformation - The proliferation of falsehood online is dividing the world as never before. Education, not regulation, is the answer, argues Bellingcat founder Eliot Higgins - or what Finland started in 2016..
Reporting on/from China
Pro-CCP network ‘Spamouflage’ weaponizes Gaza conflict to spread anti-US sentiment - For at least the past five years, a persistent online influence campaign linked to the Chinese Communist Party (CCP) has sought to capitalise on world events to promote anti-American and pro-CCP narratives. In the months since the Israel-Hamas conflict began, the campaign has pivoted to incorporate the unfolding conflict into its broader narrative universe.
Democratization, state capacity and developmental correlates of international artificial intelligence trade - Our work demonstrates that not only are Chinese AI/high-tech exports not congruous with importers’ democratic backsliding, but autocratization attributed to Chinese AI is also visible in importers of US AI. In addition, for most indicators, we do not observe any significant effect of acquiring AI from the US or China on importers’ state capacity or technological progress across the same period.
Artificial intelligence
The New York Times litigates against Microsoft and OpenAI - which it alleges - Defendants’ unlawful use of The Times’s work to create artificial intelligence products that compete with it threatens The Times’s ability to provide that service.
Randomized Controlled Trial for Microsoft Security Copilot - The findings below are based on 149 subjects - r. Using Incident Report, Copilot subjects were 151%** more accurate in answering questions about the incident facts. Using Guided Response, Copilot subjects were 73%** more accurate in answer
Governing AI for Humanity - from the UN AI Advisory Body - The risks of inaction are also clear. We believe that global AI global governance is essential to reap the significant opportunities and navigate the risks that this technology presents for every state, community, and individual today. And for the generations to come.
Generative AI and watermarking - Generative AI developers and policymakers now face a number of issues, including how to ensure the development of robust watermarking tools and how to foster watermarking standardisation and implementation rules.
Cyber proliferation
Who Is Killing All These Stories About a Controversial Tech Mogul? - This is not the first time Khare has flexed his legal muscles and managed to threaten reporters into removing his name from stories about the hack-for-hire industry.
Intellexa and Cytrox: From fixer-upper to Intel Agency-grade spyware
Reflections this week come from reading about the performance of Trusted Types in mitigating Cross Site Scripting as a vulnerability class in software which leverages it. The performance data is as impressive as it is valuable - performance evidence such as this is what we should strive for around any and all proposed security solutions..
Before Trusted Types adoption at Google, DOM-Based XSS accounted for >%50 of XSS reported to Google VRP.
Altogether, Trusted Types enable both writing new applications that are XSS-free, and eliminating DOM-Based XSS from existing applications, with a track record from Microsoft, Meta and Alphabet adoptions. As a data point, Alphabet applications migrated to Trusted Types have 0 reported XSS against them and we only see these bugs in applications not yet migrated, which is a significant reduction. In 2018 Google VRP rewarded $360K for all XSSes, in 2022 it was $95K.
Enjoying this? Don’t get via e-mail? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government, please see the legal text at the end.
Have a lovely Thursday
Ollie
Cyber threat intelligence
Who is doing what to whom and how.
Reporting on Russia
Fog of cyber war: spies from Cloud Atlas attack Russian companies under the guise of supporting SVO participants
Someone is throwing around vulnerabilities from 2017 within Russia..
Cloud Atlas is a pro-government APT group,specializing on cyber espionage and theft of confidential information. According to researchers,active at least since 2014. Most often, industrial enterprises and state-owned companies in Russia, Belarus, Azerbaijan, Turkey and Slovenia became the targets of Cloud Atlas. The main attack vector is targeted email with a malicious attachment.
The template downloaded from the link is an RTF file containing an exploit for the CVE-2017-11882 vulnerability. As a result of exploitation of this vulnerability, shellcode is launched that is designed to download an HTA file via a link and then execute it.
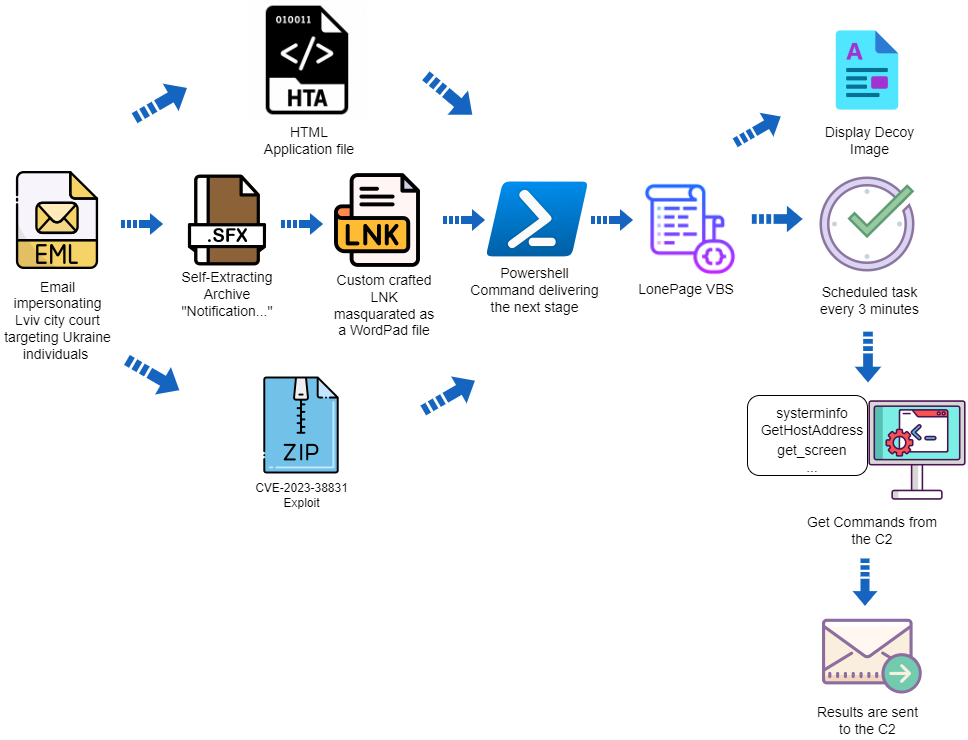
Threat Actor 'UAC-0099' Continues to Target Ukraine
An alleged pro-Russian group who has been leveraging a vulnerability in WinRAR. Of note in this reporting is the targeting on Ukrainians outside of Ukraine and their companies.
"UAC-0099" is a threat actor that has targeted Ukraine since mid-2022
The threat actor was observed leveraging CVE-2023-38831
The threat actor targets Ukrainian employees working for companies outside of Ukraine
https://www.deepinstinct.com/blog/threat-actor-uac-0099-continues-to-target-ukraine
Reporting on China
Barracuda Email Security Gateway Appliance (ESG) Vulnerability
Details of the vulnerability exploited by a suspected Chinese threat actor and apparently used against assets of governments. The threat actor spent the effort to do the device reverse engineering and code review to identify and exploit the vulnerability, even if the vulnerability itself was a shocker.
Dec 24th, 2023
… a threat actor has utilized an Arbitrary Code Execution (ACE) vulnerability within a third party library, to deploy a specially crafted Excel email attachment to target a limited number of ESG devices.
… this activity is attributable to continued operations of the China nexus actor tracked as UNC4841.
https://www.barracuda.com/company/legal/esg-vulnerability
technical details here - a raw eval …
https://infosec.exchange/@jann/111647974002373175
Reporting on North Korea
Analysis of Kimsuky Group's AppleSeed malware attack trends
Sanseo shows that being Persistent is enough even if you can’t be Advanced.
There is no significant change in the malicious codes used together, but the fact that similar attack methods have been used continuously for several years can be said to be a characteristic of attacks using AppleSeed. It is also true that the same files are still being used since information-stealing malware or RDP Patch malware, which are additionally used after taking control of the infected system, were first identified in 2022.
Reporting on Iran
Nothing this week.
Reporting on Other Actors
Understanding The Workings of Russian Hacker "Wazawaka"
A Manilia folder on this individual which is 68 pages in length.
Mikhail Pavlovich Matveev, also known by the monikers Wazawaka, Boriselcin, and Orange, has recently risen to prominence within the Threat Intelligence (TI) community, emerging as a key player in the dynamic digital threat landscape
Threat actor groups like Wazawaka and his team can operate in a tight-knit, flat hierarchy with operational flexibility. Individual members may develop a high level of trust in one another, exposing the group to operational security vulnerabilities when sharing sensitive personal information among the members.
Threat actors will exploit opportunities to turn victims’ IT staff into willing accomplices. IT leaders must consider the threat posed by malicious insiders, who may be motivated to avoid taking blame for successful attacks.
Additionally, threat actors target companies from various verticals that range in sizes and profits, showcasing no mercy for institutions operating in critical infrastructures. This reality heavily underlines companies’ need for robust cybersecurity solutions, ensuring that they won’t be left in a situation allowing exploitation or detrimental compromise
https://25491742.fs1.hubspotusercontent-eu1.net/hubfs/25491742/WAZAWAKA_TLPCLEAR_Report.pdf
New MetaStealer malvertising campaigns
Jérôme Segura does what he does best and walks through the mechanics of this campaign. The advent of advertising transparency provided a little more insight that would likely have been possible otherwise.
We captured two different ads for Notepad++ and AnyDesk via Google searches.
According to the Google Ads Transparency Center, one of the campaigns ran in November and December, during specific dates.
Users that clicked on the ads and met the selection criteria will get a malicious landing page and a download link
https://www.malwarebytes.com/blog/threat-intelligence/2023/12/new-metastealer-malvertising-campaigns
Android Banking Trojan Chameleon can now bypass any Biometric Authentication
Interesting technical sophistication on show here by criminal actors in forcing downgrade so they can capture the PIN.
The ability to bypass biometric prompts, and the ability to display an HTML page for enabling accessibility service in devices implementing Android 13's "Restricted Settings" feature.
The new Chameleon variant introduces a feature aimed at interrupting the biometric operations of the targeted device. This feature is enabled by issuing the command "interrupt_biometric". Upon receiving this command, the malware executes the "InterruptBiometric" method.
This method employs the KeyguardManager API and AccessibilityEvent to assess the screen and keyguard status. It evaluates the keyguard's state concerning various locking mechanisms, such as pattern, PIN, or password. Upon meeting the specified conditions, the malware utilizes the AccessibilityEvent action to transition from biometric authentication to PIN authentication. This bypasses the biometric prompt, allowing the trojan to unlock the device at will.
Forcing a fallback to 'standard' authentication provides underground actors with two advantages. Firstly, it facilitates the theft of PINs, passwords, or graphical keys through keylogging functionalities, because biometric data remains inaccessible to these threat actors.
https://www.threatfabric.com/blogs/android-banking-trojan-chameleon-is-back-in-action
Operation RusticWeb targets Indian Govt: From Rust-based malware to Web-service exfiltration
Sathwik Ram Prakki details a suspected Pakistani threat actor using rather basic tradecraft of .zip and .lnk files in one of their infection chain..
We have also identified targeting of both government and private entities in the defence sector over December. New Rust-based payloads and encrypted PowerShell commands have been utilized to exfiltrate confidential documents to a web-based service engine, instead of a dedicated command-and-control (C2) server.
Web injections are back on the rise: 40+ banks affected by new malware campaign
Tal Langus gives a sense as to the scale and extrapolated impact from these campaigns and the fact that the threat actors have a global outlook.
Since the beginning of 2023, we have seen over 50,000 infected user sessions where these injections were used by attackers, indicating the scale of threat activity, across more than 40 banks that were affected by this malware campaign across North America, South America, Europe and Japan.
https://securityintelligence.com/posts/web-injections-back-on-rise-banks-affected-danabot-malware/
Discovery
How we find and understand the latent compromises within our environments.
Threat Hunting Pids Within Apple’s Endpoint Security API
Jaron Bradley provides a walk through on the various IDs, which are immutable and which aren’t along with those which are Apple specific. A useful guide for those starting their macOS journey.
Every time a process is run (fork or exec) ES will provide us with details regarding said created process. Among the details it provides are a series of process ids each serving their own system internals purpose which means each one also serves its own threat hunting purpose.
https://themittenmac.com/threat-hunting-pids-within-apples-es-api/
godmode.yar
Florian Roth has released his god mode Yara rule for those that can run only one..
The primary focus of these "god mode" rules is to serve as a proof-of-concept for a special purpose: crafting a single rule that covers as many threats as possible while minimizing false positives.
https://github.com/Neo23x0/god-mode-rules/blob/master/godmode.yar
ALPChecker
Anastasiia Kro lays down the foundations with this script from the start of the year for an APLC canary should we so wish it..
a tool to detect spoofing and blinding attacks on the ALPC interaction
https://github.com/AnastasiKro/ALPChecker
SigmaToARM: Python script to convert Sigma rules to Azure ARM
Ollie Legg releases a useful tool for those on the Detection-as-Code path.
This project provides a method for converting the SigmaProject ruleset into Azure Resource Manager (ARM) templates specifically designed for use with Microsoft Sentinel Repositories. By automating this conversion process, the tool facilitates the integration of Sigma rules into Microsoft Sentinel, supporting DevOps and Sentinel-as-Code practices by creating a deployable rulebase. The library is easily modifyable to support RootA as well.
https://github.com/JawsCyber/SigmaToARM
Defence
How we proactively defend our environments.
Fara: Faux YARA
Bart P provides the Yara Dojo for the training montage..
a simple repository that contains a set of purposefully erroneous Yara rules. It is meant as a training vehicle for new security analysts, those that are new to Yara and even Yara veterans that want to keep their rule writing (and debugging) sharp.
https://github.com/bartblaze/FARA
smtpsmug: Script to help analyze mail servers for SMTP Smuggling vulnerabilities
Hanno Böck removes any excuse for not understanding if organisations are vulnerable or not to this vulnerability.
smtpsmugallows sending mails to an smtp server and ending it with various malformed end of data symbol. This tests whether servers are affected by SMTP Smuggling vulnerabilities. Please consider this preliminary and work in progress, I am still trying to fully understand the issue myself.By default,
smtpsmugwill send a test mail ending with a '\n.\n' symbol (Unix newlines instead of Windows '\r\n' newlines). It supports multiple other malformed endings. Use--list-teststo show them,--test [testname]to select one.
https://github.com/hannob/smtpsmug
Incident Writeups
How they got in and what they did.
Gloucester City Council: Managing a cyber attack
Much to be taken from this by everyone. Good of them for producing such a detailed writeup, which is why I included it twice.
In December 2021, Gloucester City Council was the subject of a targeted ransomware attack which encrypted its servers and temporarily prevented the council from providing services which relied on the data held on those servers
This case study is based on the first hand experiences of key staff at the council of dealing with the cyber attack. It includes a timeline of the attack, its impact, the recovery process, the cost of the incident, and the lessons learnt by the council.
https://www.local.gov.uk/case-studies/gloucester-city-council-managing-cyber-attack
Vulnerability
Our attack surface.
GPU.zip
Yingchen Wang, Riccardo Paccagnella, Zhao Gang, Willy R. Vasquez, David Kohlbrenner, Hovav Shacham and Christopher Fletcher once again evidence the quality of academic cyber research in 2023. This will likely have niche real-world exploitation value which we might get to hear about… one day…
GPU.zip is a new type of side channel that exposes visual data processed on the graphics processing unit (GPU). This channel exploits an optimization that is data dependent, software transparent, and present in nearly all modern GPUs: graphical data compression. We present the first security-centric analysis of this optimization and demonstrate that it can be abused to leak visual data. For example, using GPU.zip, a malicious webpage can leak pixels from another webpage in the latest version of Google Chrome, violating the browser security model.
…
We tested integrated GPUs from AMD, Apple, Arm, Intel, and Qualcomm and one discrete GPU from Nvidia. We have at least preliminary results to show that all tested GPUs are affected.
https://www.hertzbleed.com/gpu.zip/GPU-zip.pdf
Offense
Attack capability, techniques and trade-craft.
How adversaries infiltrate AWS cloud accounts
Thomas Gardner and Cody Betsworth detail a technique which likely a lot of people aren’t aware of but probably should be. Again provides evidence of cloud complexity and being a cloud cyber security expert is really is an art/domain of it self.
Adversaries are taking advantage of AWS’s Secure Token Service (STS) to generate short-term credentials to access organizations’ cloud assets
https://redcanary.com/blog/aws-sts/
Windows DHCP Server DNS Password Stealer
Grzegorz Tworek releases a tool which allows recovery of passwords from DHCP Servers which, if used, could cause havoc on a network.
https://github.com/gtworek/PSBits/tree/master/PasswordStealing/DHCP
CLR Heap encryption
Down the rabbit hole of .NET Common Language Runtime memory management to provide defence in depth of malicious payloads. We can expect this to be leveraged by the various implant framework if similar techniques aren’t already.
This is a POC for a CLR sleep obfuscation attempt. It use
IHostMemoryManagerinterface to control the memory allocated by the CLR. Turns out you can use bothICorRuntimeHostandICLRRuntimeHostat the same time, so we can still useICorRuntimeHostto run an assembly from memory while having all the benefits fromICLRRuntimeHost.
https://github.com/lap1nou/CLR_Heap_encryption
Exploitation
What is being exploited.
SharePoint Pre-Auth Code Injection RCE chain CVE-2023-29357 & CVE-2023-24955
Brace brace brace.. (for those who haven’t patched)
gist.github.com/testanull/dac6029d306147e6cc8dce9424d09868
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Graph neural network and code large model support
From China and a performance improvement..
Note our method as BinDiff+AI (combined comparison results of BinDiff and GNN+LLM)
Looking at F1, we found that after BinDiff plus embedding, XO and XC1 are basically consistent. XO+XC1 has been improved by about 2%, and XC2 and XO+XC2 have been improved by about 5% .
Adventures in reverse engineering Broadcom NIC firmware
Hugo Landau started reverse engineering these network cards in 2017 and provides the most wonderful writeup. This is also why we might get some enterprising group doing implants on network cards now..
The reverse engineering side is now pretty much done and availability of open source firmware for the BCM5719 is waiting on the completion of a reimplementation effort (thanks to Evan Lojewski). This is a cleanroom implementation and doesn't share any code with Project Ortega or the proprietary firmware, but is produced using the human-readable specifications delivered by Project Ortega. Once this is delivered, it will be possible to use Raptor's POWER9 systems with purely 100% free, open source firmware. As far as I am aware, there is no other machine in the same performance class which can make such a claim.
..
Most importantly of all, however, I was able to verify the complete absence of any RSA signature verification code. The RSA signature on the APE firmware appears, in fact, quite vestigial.
https://www.devever.net/~hl/ortega
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
REPORT TO THE CISA DIRECTOR - Technical Advisory Council - on Memory Safety December 5, 2023
NIST SPECIAL PUBLICATION 1800-29 - Data Confidentiality: Detect, Respond to, and Recover from Data Breaches - DRAFT December 2023
NIST SPECIAL PUBLICATION 1800-28 Data Confidentiality: Identifying and Protecting Assets Against Data Breaches- DRAFT December 2023
Chips to Compute With Encrypted Data Are Coming - Intel’s Cammarota sees the accelerator chips as just the starting point. FHE will also need software development tools to make programming easier as well as standardization. The two are in progress even without chips in hand, but there are many ways to do FHE and standardization work is in its early stages.
Medical Device Cybersecurity - U.S. Government Accountability Office review around interagency responsibilities.
Artificial intelligence
Lost in Translation: A Study of Bugs Introduced by Large Language Models while Translating Code - Our study, which involves the translation of 1,700 code samples from three benchmarks and two real-world projects, reveals that LLMs are yet to be reliably used to automate code translation -- with correct translations ranging from 2.1% to 47.3% for the studied LLMs.
Siracusa: A 16 nm Heterogenous RISC-V SoC for Extended Reality with At-MRAM Neural Engine - The fabricated SoC prototype achieves an area efficiency of 65.2 GOp/s/mm2 and a peak energy efficiency of 8.84 TOp/J for DNN inference while supporting complex, heterogeneous application workloads, which combine ML with conventional signal processing and control.
LLM in a flash: Efficient Large Language Model Inference with Limited Memory - paper by Apple - Our method involves constructing an inference cost model that harmonizes with the flash memory behavior, guiding us to optimize in two critical areas: reducing the volume of data transferred from flash and reading data in larger, more contiguous chunks
Gemini: A Family of Highly Capable Multimodal Models - Evaluation on a broad range of benchmarks shows that our most-capable Gemini Ultra model advances the state of the art in 30 of 32 of these benchmarks - notably being the first model to achieve human-expert performance on the well-studied exam benchmark MMLU, and improving the state of the art in every one of the 20 multimodal benchmarks we examined - a paper with a 1000 authors!
Time is Encoded in the Weights of Finetuned Language Models - Time vectors are created by finetuning a language model on data from a single time (e.g., a year or month), and then subtracting the weights of the original pretrained model. This vector specifies a direction in weight space that, as our experiments show, improves performance on text from that time period.
InstructVideo: Instructing Video Diffusion Models with Human Feedback - Extensive experiments, both qualitative and quantitative, validate the practicality and efficacy of using image reward models in InstructVideo, significantly enhancing the visual quality of generated videos without compromising generalization capabilities. Code and models will be made publicly available. - you can see how this becomes the basis of a new captcha to get that reward signal..
Zero-Shot Metric Depth with a Field-of-View Conditioned Diffusion Model - by employing a more diverse training mixture than is common, and an efficient diffusion parameterization, our method, DMD (Diffusion for Metric Depth) achieves a 25% reduction in relative error (REL) on zero-shot indoor and 33% reduction on zero-shot outdoor datasets over the current SOTA using only a small number of denoising steps.
Books
Nothing this week
Events
PIVOTcon 2024 :: CFP - Malaga (Spain), May 8-10, 2023 - an invite-only event (with a maximum of 150 vetted attendees) with focus on threat research and technical analysis tradecraft.
45th IEEE Symposium on Security and Privacy, May 20-22, 2024 - San Francisco
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.








But best bits be best bits. No worries!
Peach Sandstorm and False Font for Iran this week