CTO at NCSC Summary: week ending December 24th - 🎄🎅 edition
Happy 25th Birthday SQL Injection....
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note beyond the usual tempo.
In the high-level this week:
New SEC rules came into force
Cybersecurity Disclosure - To help investors evaluate this, the final rule has two components: a requirement to disclose material cybersecurity incidents four business days after a public company determines the incident is material and a requirement to disclose annually information regarding cybersecurity risk management, strategy, and governance.
FAQ - Some of the interpretations included here were originally published in the sources noted above, and have been revised in some cases. The bracketed date following each interpretation is the latest date of publication or revision.
SEC Cyber Rules Loom Over Public Companies - Starting Friday, the Securities and Exchange Commission will oblige companies to disclose how they manage cyber risk in annual reports, known as 10-Ks. Companies will be expected to detail how they assess threats and protections, and to what degree their boards exercise oversight on cyber issues. Annual filings must also describe the potential material effects of a successful attack.
Protecting and enhancing the security and resilience of UK data infrastructure - This consultation will gather further views and evidence to inform development of proposals to improve and assure the security and resilience of UK data infrastructure. Proposals focus on third-party data centre services, which face:
Security threats such as cyber attacks, physical attacks, and insider threats.
Resilience risks resulting from hazards such as equipment malfunction and extreme weather.
Poor information-sharing and cooperation across industry, and with HMG, which hamper our ability to appropriately identify and address risks.
The proposals focus on a new proposed statutory framework applying to UK-based data centre services provided to third parties, but potentially applicable in future where other risks are evidenced.
Ghana’s Cyber Security Authority elected to lead the African Network of Cybersecurity Authorities - The countries include Benin, Burkina Faso, Cameroon, Chad, Congo Republic, Djibouti, Gabon, Ghana, Guinea, Kenya, Morocco, Mozambique, Rwanda, Senegal, Sierra Leone, Togo and Tunisia.
NSA 2023 Cybersecurity Year in Review - One emerging threat – and opportunity – is Artificial Intelligence (AI). AI and machine learning technologies are being developed and proliferating faster than companies and governments can shape norms, create standards, and ensure positive outcomes
Aussie Government’s Overview of Cyber Security Obligations for Corporate Leaders Leadership in cyber security governance - This document is our first step to clarify cyber obligations for corporate leaders. Next, we will explore options to provide additional information on cyber governance obligations under current regulation.
Joint Statement of the Quad Senior Cyber Group - Together, we reaffirm our steadfast commitment to an Indo-Pacific that is resilient and equipped to detect and deter cyber attacks. Quad countries are among the world’s leaders in advancing digital technology, connectivity, and resilience and are undertaking efforts to provide capacity building in the Indo-Pacific region to strengthen the ability to defend their government networks and critical infrastructure from cyber disruptions.
[UK] Ministry of Justice Cyber Security Strategy: 2023 to 2028 - The aim is to embed ‘Secure by Design’ thinking into everything the department does, ensuring everyone can confidently perform their security responsibilities.
Justice Department Disrupts Prolific ALPHV/Blackcat Ransomware Variant - The FBI developed a decryption tool that allowed FBI field offices across the country and law enforcement partners around the world to offer over 500 affected victims the capability to restore their systems.
Former Security Engineer For International Technology Company Pleads Guilty To Hacking Two Decentralized Cryptocurrency Exchanges - Shakeeb Ahmed Admits to Hacking Nirvana Finance and Another Decentralized Cryptocurrency Exchange in First Ever Conviction for the Hack of a Smart Contract
A Russian banker, residing in Cyprus, suspected in this affair, was arrested last Tuesday in Paris - related to Hive ransomware - très bon!
Cybercrime: the fear of a possible misuse of personal data is capable, in itself, of constituting non-material damage - The fear experienced by a data subject with regard to a possible misuse of his or her personal data by third parties as a result of an infringement of the GDPR is capable, in itself, of constituting ‘non-material damage’ - be interesting to see how this plays out.
Agreement between the Council and the European Parliament makes EU liability rules fit for the digital age and circular economy - The Council and Parliament also agreed that any natural person who suffers damage by a defective product is entitled to compensation. Such damages include death or personal injury, including medically recognised damage to psychological health, damage to or destruction of property, as well as destruction or irreversible corruption of data.
Cybersecurity Tech Accord calls for International Norms to Protect the ICT Supply Chain - As a community of more than 150 technology firms from around the world, we can say with confidence that cyberattacks against the ICT supply chain can never be consistent with responsible state behavior as they are inherently indiscriminate, irresponsibly disrupting individual citizens’ lives and livelihoods.
Tokyo Electron says China is snapping up its less advanced chip tools amid export controls - Asia’s largest semiconductor equipment maker Tokyo Electron says it has largely managed to offset the impact of controls on exports to China by expanding its sales of less advanced products to the country’s chip industry.
We call on States to stop turning a blind eye to the participation of civilian hackers in armed conflict - Call by the International Council of the Red Cross
Civilian hackers blur the lines of modern conflict - IHL sets out essential rules to limit the effects of armed conflicts on civilians. No one who participates in armed conflict is beyond these rules. Every hacker who conducts operations in the context of an armed conflict must respect them
Defending Democracy
Joint Statement from the Departments of Justice and Homeland Security Assessing the Impact of Foreign Interference During the 2022 U.S. Mid-Term Election - … the government detected some foreign government-affiliated and criminal cyber activity targeting election infrastructure, including activity by suspected People’s Republic of China cyber actors and activity claimed by pro-Russian hacktivists … electoral cyber is going to get more nuanced..
Aggressive Malign Influence Threatens to Shape US 2024 Elections - The identified overarching influence trends include increasing polarization and undermining confidence in US democratic institutions, reducing domestic support for aiding US allies, and undermining political candidates with unfavorable policies while promoting those with favorable policies.
Deepfakes mislead voters in Bangladesh election - Public pressure is rising on tech platforms to crack down on misleading AI content ahead of several big elections expected in 2024, including in the US, the UK, India and Indonesia.
Meet Ashley, the world's first AI-powered political campaign caller - She is capable of having an infinite number of customized one-on-one conversations at the same time.
Massive Russian influence operation targeted former Ukrainian defense minister on TikTok - The increasing ease with which malign actors can create large quantities of videos in an attempt to have some of them go viral presents an all-too-tempting opportunity for those intent on spreading malicious information.
Reporting on/from China
Under China’s new security rules, internet operators must report hacks and cybercrimes within an hour - According to the draft, all operators must report the incidents to local or national cyberspace offices, and those who work with “key information infrastructure” or face crime-related incidents should also report breaches to the police.
Research Report of Domestic and Foreign Research Teams on Software Security (Part 1) - Chinese analysis of foreign academic teams.
Research Report of Domestic and Foreign Research Teams on Software Security (Part 2) - Chinese analysis of domestic academic teams
Shadow Play - A pro-China technology and anti-US influence operation thrives on YouTube - a network of at least 30 YouTube channels that have produced more than 4,500 videos. At time of publication, those channels have attracted just under 120 million views and 730,000 subscribers
Artificial intelligence
[EU] Artificial Intelligence [Regulation] – Questions and Answers
Israel's Policy on Artificial Intelligence Regulation and Ethics
World first supercomputer capable of brain-scale simulation being built at Western Sydney University - DeepSouth uses a neuromorphic system which mimics biological processes, using hardware to efficiently emulate large networks of spiking neurons at 228 trillion synaptic operations per second - rivalling the estimated rate of operations in the human brain.
Generative Artificial Intelligence and the Creative Economy Staff Report: Perspectives and Takeaways - Although many of the concerns raised at the roundtable lay beyond the scope of the Commission’s jurisdiction, targeted enforcement under the FTC’s existing authority in AI-related markets can help to foster fair competition and protect people in creative industries and beyond from unfair or deceptive practices.
Cyber proliferation
TVP must apologize to Krzysztof Brejza. It's about stolen text messages - The court in Bydgoszcz ruled: just before "Wiadomości", TVP is to apologize to Krzysztof Brejza for publishing his private SMS correspondence, stolen with the help of Pegasus and manipulated.
Cybersecurity Futures 2030: New Foundations - from the World Economic Forum - Shoring up trust will be a key goal of cybersecurity efforts over the next decade. The online spread of mis- and disinformation are now core cybersecurity concerns. Cybersecurity will become less about protecting the confidentiality and availability of information and more about protecting its integrity and provenance.
Swiss Re brings first cyber industry-loss cat bond under Matterhorn Re - Global reinsurance giant Swiss Re is bringing the first industry-loss triggered cyber catastrophe bond to market, seeking $50 million of retrocession against systemic cyber loss events through a Matterhorn Re Ltd. (Series 2023-1) transaction.
Reflections this week come from the UK IC Postdoctoral Research Fellowships being published and this one in particular - using homomorphic encryption for machine learning on sensor data and privacy. This type of novel blended thinking has potential to unlock latent value in data if we can pull it off securely..
Finally SQL Injection turns 25 this Christmas day and serves as another example of a vulnerability class which is proving rather stubborn in reality to eradicate. This is compounded with evidence this week (see GambleForce) of sectoral targeting by a criminal gang using just this technique - which shows how far we have to go.
Enjoying this? Don’t get via e-mail? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government, please see the legal text at the end.
Have a lovely Wednesday
Ollie
Cyber threat intelligence
Who is doing what to whom and how.
Reporting on Russia
Russia’s largest hacking conference: Biggest hits from Positive Hack Days 2023
Justin Sherman provides an analysis of the themes from Russia’s cyber conference which shows that themes in the industry are at times universal but also sanctions a potential impact on open source adoption rates.
Market transparency in the Russian cyber sector has fallen post-February 2022 (after—which participants did not say—the Russian government launched a full-scale, illegal war on Ukraine and was hit with Western sanctions), including because many companies are “shadow” installing foreign tech products and not reporting it.
Demand for cybersecurity services is increasing in most sectors, except insurance.
There are still many barriers within Russia’s cyber sector to effective cooperation and threat information-sharing, as well as in developing community platforms for practitioners to communicate with one another.
Ransomware groups targeting the Russian private sector have, among other things, exploited vulnerabilities in Linux.
Many companies are using open-source technology where possible.
Russia still struggles to replace foreign-made hardware, including because Russia does not have the requisite domestic microelectronics manufacturing capability.
Technological independence does not mean technological isolation, and Russia should explore working more with Asian countries, such as India, and the Shanghai Cooperation Organization (SCO) countries (which includes China) on tech development.
Russian Foreign Intelligence Service (SVR) Cyber Actors Use JetBrains TeamCity CVE in Global Targeting
Polish, US and British Governments came out with alerting on this threat actor. Note the use of EDR disabling techniques. Raises the importance of ensuring integrity and correct functioning of EDR in states.
To avoid detection, the SVR used a “Bring Your Own Vulnerable Driver” [T1068] technique to disable or outright kill endpoint detection and response (EDR) and antivirus (AV) software [T1562.001]. This was done using an open source project called “EDRSandBlast.” The authoring agencies have observed the SVR using EDRSandBlast to remove protected process light (PPL) protection, which is used for controlling and protecting running processes and protecting them from infection.
https://www.gov.pl/attachment/f111510e-f9b6-40e7-b3f0-7cae28c8ff38
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-347a
CALISTO doxxing: [Our] findings concurs to Reuters’ investigation on FSB-related Andrey Korinets
Third party analysis which ties together various bits of other reporting and creates a technical link between this activity.
With this infrastructure investigation, we demonstrated that a Russian individual, whose name was disclosed by Reuters, did in fact register phishing domains used by the CALISTO intrusion set to conduct at least a phishing campaign targeting UK entities, including the Parliament.
Russia’s Tolerance for Allied Cyberspying Is About Keeping Friends Close
Emilio Iasiello provides a brief analysis of what is originally Russian reporting to highlight the scale of alleged PRC interest in Russia through cyber means. Frenemies it would appear..
Per the company, Chinese-related activity consisted of aggressive and frequent cyber espionage campaigns that sought out in some cases 20-40 Russian organizations every day and infecting them with malware.
Reporting on China
Routers Roasting on an Open Firewall: the KV-botnet Investigation
Indications that compromise of SOHO routers to build covert infrastructure might be a thing from this reporting…
From July 2022 through February 2023, we observed overlap between NETGEAR ProSAFE firewalls acting as relay nodes for networks compromised by a threat group known as Volt Typhoon. Also known as “Bronze Silhouette,” this group is a “state-sponsored actor based in China that typically focuses on espionage and information gathering.”
https://blog.lumen.com/routers-roasting-on-an-open-firewall-the-kv-botnet-investigation/
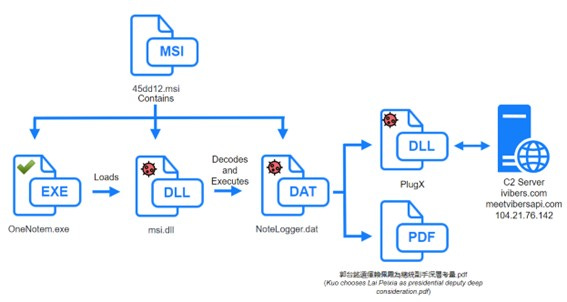
Mustang Panda’s PlugX new variant targeting Taiwanese government and diplomats
Reporting which indicates iterative development of capability with language divergence and crypt changes yet underlying tradecraft is broadly consistent. Shows there is wisdom in the Pyramid of Pain (which is now over 10 years old).
Both the infection chain and the various artefacts used in the cyberattack share multiple similarities with the SmugX campaign, attributed to threat actors Red Delta and Mustang Panda, allegedly linked to the Chinese government.
The malicious DLL is written in the Nim programming language.
This new variant uses its own implementation of the RC4 algorithm to decrypt PlugX, unlike previous versions that use the Windows Cryptsp.dll library.
Undocumented 8220 Gang Activities - widely believed to be of Chinese origin
Daniel Johnston details evolution of Chinese cyber criminal activity living off of a diet of n-days to mine crypto currency.
As well as the recently disclosed use of CVE-2021-44228 and CVE-2017-3506, [We] observed the group’s attempted exploitation of CVE-2020-14883, a Remote Code Execution vulnerability in Oracle WebLogic Server, to propagate malware.
https://www.imperva.com/blog/imperva-detects-undocumented-8220-gang-activities/
Reporting on North Korea
Investigation: Probable DPRK Online Personas Used To Fraudulently Obtain Remote Employment at U.S. Companies
Reporting which indicates DPRK continues to try and get remote IT jobs in countries where we likely would prefer they did not. When you are going for the crypto jobs directly it shows a degree of focus to say the least..
[We] identified a number of online personas probably used by the Democratic People’s Republic of Korea (DPRK, a.k.a. North Korea) information technology (IT) workers to fraudulently obtain remote employment from unwitting companies in the United States.
https://www.nisos.com/blog/dprk-it-worker-scam/
How one country is impacting supply chains - DPRK attacks on GitHub, NPM, PyPi, etc.
Yehuda Gelb details the extent to which they claim North Korea is going after various open source supply chains. This reporting should serve as a warning to any security team who is tasked with helping secure the development process.
Attack Strategies: In 2023, North Korea displayed significant activity by utilizing various strategies to undermine global supply chains.
Public open source poisoning: These attacks focus on exploiting the trust in shared code repositories, such as open-source packages available on NPM, PyPi, etc.
Private packages poisoning using GitHub Platform: A more sophisticated approach, where the attackers utilize GitHub as a distribution channel for the malicious software.
https://checkmarx.com/blog/how-one-country-is-impacting-supply-chains/
Analysis of Konni organization's secret theft operation using email security check manual as bait
Chinese reporting on alleged regional targeting which highlights continued regional software targeting - by virtue of the file types used. The tradecraft is run of the mill for this threat actor otherwise.
[We] discovered some malicious LNK files targeting South Korea. The LNK files release decoy files and VBS scripts after running. The decoy HWP document used by one of the samples is an instruction manual on how to perform email security checks.
Reporting on Iran
Seedworm: Iranian Hackers Target Telecoms Orgs in North and East Africa
Reporting which shows tradecraft specifically around remote access tooling and proxies which should be of note to telecommunications providers globally.
Seedworm has been active since at least 2017, and has targeted organizations in many countries, though it is most strongly associated with attacks on organizations in the Middle East. It has been publicly stated that Seedworm is a cyberespionage group that is believed to be a subordinate part of Iran’s Ministry of Intelligence and Security (MOIS).
The attackers used a variety of tools in this activity, which occurred in November 2023, including leveraging the MuddyC2Go infrastructure,.
The attackers also use the SimpleHelp remote access tool and Venom Proxy, which have previously been associated with Seedworm activity, as well as using a custom keylogging tool, and other publicly available and living-off-the-land tools.
OilRig’s persistent attacks using cloud service-powered downloaders
Zuzana Hromcová and Adam Burgher provides reporting which indicates a diverse set of infrastructure and focus on cloud by this threat actor. This technical tradecraft is in addition to multiple waves of campaign against the targets put the P in persistent.
OilRig actively developed and used a series of downloaders with a similar logic throughout 2022: three new downloaders – ODAgent, OilCheck, OilBooster – and newer versions of the SC5k downloader.
The downloaders use various legitimate cloud service APIs for C&C communication and data exfiltration: Microsoft Graph OneDrive API, Microsoft Graph Outlook API, and Microsoft Office EWS API.
Targets, all in Israel, included an organization in the healthcare sector, a manufacturing company, a local governmental organization, and other organizations.
All targets were previously affected by multiple OilRig campaigns.
Reporting on Other Actors
Opening a Can of Whoop Ads: Detecting and Disrupting a Malvertising Campaign Distributing Backdoors
Ryan Tomcik, Adrian McCabe, Rufus Brown and Geoff Ackerman give an indication as to the scale of malvertising and the enduring nature of its use.
[We track] around 30 threat clusters that use malicious advertisements for the delivery of malware, including backdoors, data stealers, and downloaders. Since at least 2021, a threat actor tracked as UNC2975 has leveraged this technique to distribute downloader malware for second-stage payloads on victim endpoints.
https://www.mandiant.com/resources/blog/detecting-disrupting-malvertising-backdoors
Hacktivism in the Israel-Hamas Conflict | Citizen Data Leaked Using Old Malware
Jim Walter provides reporting which indicates the current skill and capability level of hacktivism around this conflict. There should be lessons taken from this for any future events as capability continues to proliferate..
The hacktivist groups currently active in the Israel-Hamas conflict are ramping up in both intent and skill level. Though these groups are still relatively small, it is clear that they are carrying out successful attacks and putting ordinary citizens at risk. This class of criminal activity is often viewed as being of a lower tier, however, ongoing fighting in Gaza has provided a springboard for these groups to leverage political chaos to further their malicious cyber goals.
We believe that these groups are of relatively low-sophistication and financial resources. The malicious actors’ use of tools like Redline and PrivateLoader speak to their position of having to use what is at their disposal. This is bolstered by the example of using in-the-wild Redline samples with known hashes, revealing that the actors are not making the effort to modify or customize the older malware.
Gaza Cybergang | Unified Front Targeting Hamas Opposition
Aleksandar Milenkoski provides further insights into regional conflict aspects with this reporting.
Overlaps in targeting, malware characteristics, and long-term malware evolutions post 2018 suggest that the Gaza Cybergang sub-groups have likely been consolidating, possibly involving the establishment of internal and/or external malware supply lines.
Gaza Cybergang has upgraded its malware arsenal with a backdoor that we track as Pierogi++, first used in 2022 and seen throughout 2023.
Recent Gaza Cybergang activities show consistent targeting of Palestinian entities, with no observed significant changes in dynamics since the start of the Israel-Hamas war.
[Our] analysis reinforces the suspected ties between Gaza Cybergang and WIRTE, historically considered a distinct cluster with loose relations to the Gaza Cybergang.
https://www.sentinelone.com/labs/gaza-cybergang-unified-front-targeting-hamas-opposition/
Ace in the Hole: exposing GambleForce, an SQL injection gang
Nikita Rostovcev provides further evidence as to the impact of SQL Injection and the effect use by a criminal group..
GambleForce is a previously unknown threat actor involved in SQL injection attacks
Since it appeared in September 2023, the group has targeted 24 websites (government, gambling, retail, travel, and job-seeking)
The group primarily focuses on the Asia-Pacific region: Australia, China, Indonesia, Philippines, India, South Korea, Thailand
GambleForce uses a set of publicly available open-source tools for pentesting: dirsearch, redis-rogue-getshell, Tinyproxy, sqlmap, and Cobalt Strike
The version of Cobalt Strike discovered on the gang’s server used commands in Chinese
In one attack in Brazil, the attackers exploited CVE-2023-23752, a vulnerability in Joomla CMS, but they failed to exfiltrate any data
Group-IB took down the gang’s C&C and sent notifications to the identified victims
Group-IB’s Threat Intelligence unit believes that the group may soon rebuild the infrastructure and we continue monitoring their activity
https://www.group-ib.com/blog/gambleforce-gang/
QR Phishing Leads to Microsoft 365 Account Compromise
Reporting which shows ‘yes they would’ when people say ‘people wouldn’t do that’. Also the intricate and distributed infrastructure is of note..
[We] investigated a network compromise that originated from a phishing email containing a PDF attachment. The PDF included a QR code that directed recipients to malicious content hosted on an interplanetary file system (IPFS) gateway. Using this gateway allows threat actors to save the cost and effort associated with hosting their own infrastructure and makes it difficult for law enforcement to take down the malicious content.
https://www.secureworks.com/blog/qr-phishing-leads-to-microsoft-365-account-compromise
Discovery
How we find and understand the latent compromises within our environments.
kunai: Threat-hunting tool for Linux
From Luxemburg with ❤️
The goal behind this project is to bring relevant events to achieve various monitoring tasks ranging from security monitoring to Threat Hunting on Linux based systems. If you are familiar with Sysmon on Windows, you can think of Kunai as being a Sysmon equivalent for Linux.
events arrive sorted in chronological order
benefits from on-host correlation and events enrichment
works well with Linux namespaces and container technologies (you can trace all the activity happening inside your containers)
https://github.com/0xrawsec/kunai
Toward Ending the Domain Wars: Early Detection of Malicious Stockpiled Domains
Janos Szurdi, Shehroze Farooqi and Nabeel Mohamed give a sense of which features (in a feature extraction sense) they rely on to perform this type of actvity.
Certificate Features
Domain Name Lexical Features
Certificate Domain Aggregation Features
Certificate Reputation and Aggregation Features
pDNS and Certificate Aggregation Features
pDNS Reputation and Aggregation Features
https://unit42.paloaltonetworks.com/detecting-malicious-stockpiled-domains/
Bulk Analysis of Cobalt Strike's Beacon Configurations
Jared Stroud provides some useful data if we wanted to become more data driven around aspects to focus detection around.
https://www.archcloudlabs.com/projects/bulk-cs-analysis/
Defence
How we proactively defend our environments.
New Microsoft Incident Response team guide shares best practices for security teams and leaders
Or how to make leaders more sophisticated customers..
One note—this guidance is not intended to replace comprehensive incident response planning, which should occur outside of a live incident. It is a tactical, people-centric guide to help both security teams and senior stakeholders navigate an incident response investigation, should you find yourself in the deep end during an incident.
CISA Releases SCuBA Google Workspace Secure Configuration Baselines for Public Comment
Only good will come from this..
The draft baselines offer minimum viable security configurations for nine GWS services: Groups for Business, Google Calendar, Google Common Controls, Google Classroom, Google Meet, Gmail, Google Chat, Google Drive and Docs, and Google Sites. The ScubaGoggles tool assesses GWS tenants' compliance against the baselines.
Incident Writeups
How they got in and what they did.
MongoDB is actively investigating a security incident
Ongoing and full extent not known..
At this time, as a result of our investigation in collaboration with outside experts, we have high confidence that we were victims of a phishing attack.
…
We are aware of unauthorized access to some corporate systems that contain customer names, phone numbers, and email addresses among other customer account metadata, including system logs for one customer. We have notified the affected customer. At this time, we have found no evidence that any other customers’ system logs were accessed.
https://www.mongodb.com/alerts
Vulnerability
Our attack surface.
Apache Struts2 file upload vulnerability analysis (CVE-2023-50164)
Chinese analysis of this vulnerability and how to exploit.
https://xz-aliyun-com.translate.goog/t/13172?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en-US&_x_tr_pto=wapp
SMTP Smuggling - Spoofing E-Mails Worldwide
Timo Longin shows why DMARC is your friend.
Threat actors could abuse vulnerable SMTP servers worldwide to send malicious e-mails from arbitrary e-mail addresses, allowing targeted phishing attacks. Due to the nature of the exploit itself, this type of vulnerability was dubbed SMTP smuggling. Multiple 0-days were discovered, and various vendors were notified during our responsible disclosure in 2023
https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/
Google OAuth is broken (sort of)
Dylan Ayrey highlights the potential every growing attack surface and complexity that cloud creates that we must contend with.
The issue is, we can actually create Google accounts off of corporate Google organization, via email aliases, and email plus sign forwarding. In google youremail+anystringhere@anydomain.com will be forwarded to youremail@anydomain.com‘s inbox.
This creates a window of opportunity to create a non-Gmail Google account with a plus sign email using your company’s Google organization email, that cannot be deleted or off-boarded by your organization:
https://trufflesecurity.com/blog/google-oauth-is-broken-sort-of/
Offense
Attack capability, techniques and trade-craft.
Poor Mans Sim Porting - Using USSD functionality to remotely hijack SIM cards
Jamieson O'Reilly details a technique that will be old news to anyone who grew up in the WAP era but will likely now we adopted at scale by some criminal groups in blended human/tech operations.
The focus of this report is to shed light on the high-risk configuration of telecommunications systems, specifically examining the misuse of
tel://links in SMS messages. Remote attackers can exploit these links to initiate unauthorised call forwarding with minimal user interaction.
https://dvuln.com/blog/poor-mans-sim-porting
Mute the Sound: Chaining Vulnerabilities to Achieve RCE on Outlook
Ben Barnea details his research hoping the world has patched and there aren’t latent variants to be found.
[We] found two vulnerabilities in Microsoft Windows, which were assigned CVE-2023-35384 and CVE-2023-36710.
An attacker on the internet can chain the vulnerabilities together to create a full, zero-click remote code execution (RCE) exploit against Outlook clients.
The first vulnerability lies in the parsing of a path by the MapUrlToZone function. Exploiting this vulnerability requires sending a crafted email to an Outlook client, which in turn will download a special sound file from an attacker-controlled server.
The second vulnerability lies in the Audio Compression Manager (ACM). This vulnerability is exploited when the downloaded sound file is autoplayed, and it can lead to code execution on the victim machine. This vulnerability is described in detail in part 2 of this blog post.
The vulnerabilities were responsibly disclosed to Microsoft and addressed on the August 2023 and October 2023 Patch Tuesdays.
Windows machines with the October 2023 software update installed are protected from these vulnerabilities. Additionally, Outlook clients that use Exchange servers patched with March 2023 software update are protected against the abused feature.
https://www.akamai.com/blog/security-research/chaining-vulnerabilities-to-achieve-rce-part-one
https://www.akamai.com/blog/security-research/chaining-vulnerabilities-to-achieve-rce-part-two
Let Me Manage Your AppDomain: Abuse the CLR memory un(safety)
A technique to go threat hunting for..
To backdoor .NET Framework applications we’re going to abuse a very well-known technique:
App Domain Manager Injection
https://ipslav.github.io/2023-12-12-let-me-manage-your-appdomain/
PoolPartyBof: A beacon object file implementation of PoolParty Process Injection Technique
Shashwat Shah provides capability which will likely be adopted by some with access to Cobalt Strike to evade EDR.
The BOF supports the 5 technique/variant:
Insert TP_IO work item to the target process's thread pool.
Insert TP_ALPC work item to the target process's thread pool.
Insert TP_JOB work item to the target process's thread pool.
Insert TP_DIRECT work item to the target process's thread pool.
Insert TP_TIMER work item to the target process's thread pool.
https://github.com/0xEr3bus/PoolPartyBof
DarkGate Install Script via DNS TXT Record
Why logging any DNS resolutions in corporate environments is good and why DOH can blindside.
I developed a PoC for the new DarkGate Install script retrieval technique via DNS TXT Record and uploaded it in the following repo which consists of -
PDF with embed link (Name: Bank-Statement-poc.pdf)
ZIP Archive (Name: Bank-Statement-20231523-poc.pdf.zip)
consists of the LNK (Shortcut) file which retrieves install script via DNS TXT Records (Name: Bank-Statement-20231523-poc.pdf.lnk)
https://github.com/knight0x07/DarkGate-Install-Script-via-DNS-TXT-Record
Data Bouncing - PowerShell Version
Coming to an offensive operation by your adversary of choice soon. This is going to compound some of the detection headaches.
Data Bouncing is a technique for transmitting data between two endpoints using DNS lookups and HTTP header manipulation. This PowerShell version encapsulates core functionalities of data bouncing, including reconnaissance, data exfiltration, and file reassembly
https://github.com/Unit-259/DataBouncing
Exploitation
What is being exploited.
Magento wish list exploit bypasses WAF protection
Evidence that criminal threat actors can adapt and evolve due to competition. Also the fact that Magento continues to get pounded by the criminal fraternity.
[We] observed a spike in hacked Magento 2 stores. Our investigations led to a (likely) single attacker, who used a combination of clever techniques to bypass WAFs and competing threat actors.
https://sansec.io/research/magento-wish-list-exploits
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
ssh3: SSH3: faster and rich secure shell using HTTP/3
François Michel makes some blue teams sob as the convergence on HTTPS continues..
Significantly faster session establishment
New HTTP authentication methods such as OAuth 2.0 and OpenID Connect in addition to classical SSH authentication
Robustness to port scanning attacks: your SSH3 server can be made invisible to other Internet users
UDP port forwarding in addition to classical TCP port forwarding
All the features allowed by the modern QUIC protocol: including connection migration (soon) and multipath connections
https://github.com/francoismichel/ssh3
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
State of the threat targeting the telecommunications sector - from the French government
Be Jolly, But Watch Out For Zero and N-day Follies!l - cyber-attacks stemming from zero-day exploits surged in 2023, with about 70 zero-day exploits disclosed between January to September 2023, a 40% increase from the whole of 2022
TSUBAME Report Overflow (Jul-Sep 2023) - This TSUBAME Report Overflow series discuss monitoring trends of overseas TSUBAME sensors and other activities which the Internet Threat Monitoring Quarterly Reports does not include
JPCERT/CC Incident Handling Report July 1, 2023 - September 30, 2023 - published December
JPCERT/CC Internet Threat Monitoring Report July 1, 2023 - September 30, 2023 - published December
JPCERT/CC Activities Overview Topics July 1, 2023 - September 30, 2023 - Published December
Trends in Digital Markets: a Competition Market Authority horizon scanning report
Your Smart TV Knows What You’re Watching – ACR identifies what’s displayed on your television, including content served through a cable TV box, streaming service, or game console, by continuously grabbing screenshots and comparing them to a massive database of media and advertisements - they will know which TVs are likely in corporate settings due to atypical consumer behaviour
MITRE PANOPTIC™: the Pattern and Action Nomenclature Of Privacy Threats In Context
Disrupting the gateway services to cybercrime - Storm-1152 runs illicit websites and social media pages, selling fraudulent Microsoft accounts and tools to bypass identity verification software across well-known technology platforms
Project Silica: Towards Sustainable Cloud Archival Storage in Glass - : the first cloud storage system for archival data underpinned by quartz glass, an extremely resilient media that allows data to be left in situ indefinitely. The hardware and software of Silica have been co-designed and co-optimized from the media up to the service level with sustainability as a primary objective
Artificial intelligence
Application practice of large models in the field of code defect detection - Through theory and practice, it has been proved that it is feasible to let the computer learn the programming language independently and complete the defect detection task.
Introducing Fuzzomatic: Using AI to Automatically Fuzz Rust Projects from Scratch
VGen - an open-source video synthesis codebase … featuring state-of-the-art video generative models - from China with
Toward General-Purpose Robots via Foundation Models: A Survey and Meta-Analysis
Liquid Time-constant Networks - We introduce a new class of time-continuous recurrent neural network models. Instead of declaring a learning system's dynamics by implicit nonlinearities, we construct networks of linear first-order dynamical systems modulated via nonlinear interlinked gates. related article Liquid AI, a new MIT spinoff, wants to build an entirely new type of AI
Books
Nothing this week
Events
Webinar: The Psychological Impact of Ransomware - A new RUSI report highlights the psychological harm caused by ransomware - 17th January 2024
Amsterdam 2024 FIRST Technical Colloquium - Call for Papers
European Cyber Conflict Research Initiative (ECCRI) Virtual Workshops - Call for Abstracts
Video of the week The UN cybercrime convention: Implementing a global treaty and managing risks
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.