CTO at NCSC Summary: week ending December 8th
“China continues to be a highly sophisticated and capable threat actor, targeting a wide range of sectors and institutions across the globe, including in the UK.”
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note beyond alleged mass-compromise allegedly by Russia of a Pakistani APT’s command & control to deploy their own implants, an alleged Chinese threat actor exploiting old days in browsers and some data giving a insight into the prevalence of Pegasus implants within a certain mobile population..
In the high-level this week:
NCSC Annual Review 2024 - NCSC UK publishes our annual report - “China continues to be a highly sophisticated and capable threat actor, targeting a wide range of sectors and institutions across the globe, including in the UK.”
UK girls triumph in national cyber skills contest - NCSC UK - “The 2024 CyberFirst Girls Competition, run by GCHQ’s National Cyber Security Centre, saw the largest number of girls signing up since its inception”
Enhanced Visibility and Hardening Guidance for Communications Infrastructure - CISA publishes - “The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI), Australian Signals Directorate’s (ASD’s) Australian Cyber Security Centre (ACSC), Canadian Cyber Security Centre (CCCS), and New Zealand’s National Cyber Security Centre (NCSC-NZ) warn that People’s Republic of China (PRC)-affiliated threat actors compromised networks of major global telecommunications providers to conduct a broad and significant cyber espionage campaign.”
The UK’s requirements for visibility and hardening can be found in the Telecommunications Security Regulations 2022 - the code of practice provides the technical specifics.
Cybersecurity package: Council adopts new laws to strengthen cybersecurity capacities in the EU - European Union announces - “The new regulation also provides for the creation of a cybersecurity emergency mechanism to increase preparedness and enhance incident response capabilities in the EU. It will support:
preparedness actions, including testing entities in highly critical sectors (healthcare, transport, energy, etc.) for potential vulnerabilities, based on common risk scenarios and methodologies
a new EU cybersecurity reserve consisting of incident response services from the private sector ready to intervene at the request of a member state or EU institutions, bodies, and agencies, as well as associated third countries, in case of a significant or large-scale cybersecurity incident
technical mutual assistance”
Amending Regulation (EU) 2019/881 as regards managed security services - European Union passes - “The proposed targeted amendment aims to enable, by means of Commission implementing acts, the adoption of European cybersecurity certification schemes for ‘managed security services’, in addition to information and technology (ICT) products, ICT services and ICT processes, which are already covered under the Cybersecurity Act. Managed security services play an increasingly important role in the prevention and mitigation of cybersecurity incidents.”
2024 Report on the State of the Cybersecurity in the Union - ENISA publishes - “As the EU cybersecurity policy framework has evolved, implementation at a national level becomes a priority and national competent authorities are in the process of working towards this goal. However, the policy implementation process is demanding both in terms of time and resources.”
Japan tech companies scramble to comply with EU cybersecurity laws - Nikkei Asia reports - “Japanese tech companies like NEC and Mitsubishi Electric are struggling to keep up with cybersecurity regulations being enacted in the European Union, putting themselves at risk of being excluded from the market or hit with heavy fines.”
US Federal Trade Commission does double whammy against data brokers
Internet governance: Keeping the internet open, free and unfragmented - European Parliament briefs - “The EU is a strong supporter of the multi-stakeholder approach to internet governance. This approach incorporates the views of a variety of stakeholders, including governments, businesses, technical communities and civil society on an equal footing. Not all actors share this view, however. China and Russia in particular believe that states should have a greater role in deciding on the content, operations and norms of the internet within their borders. China has also proposed to change the internet's protocol design. The EU is a strong defender of an open, free and unfragmented internet that remains a singular, decentralised network of networks.”
Reporting on/from China
An Inside Look at China’s Hacking Competitions - China Observer looks inside - “The paper found that 63 percent of institutions consider hacking competitions effective for training, with 45 percent of students starting in their freshman year and 32 percent in their sophomore year. Additionally, 75 percent of universities offer financial incentives for top performers, and the same percentage funds attack-defense labs to enhance students’ skills through mandatory courses.”
China’s intelligence ministry warns of security risks from open-source data - South China Morning Post reports - “Ministry of State Security says improperly handled publicly available data such as social media is a ‘key source’ of intelligence for foreign spies”
Huawei has global ambitions for ‘pure blood’ OS, but challenges abound - South China Morning Post reports - “The flagship Mate 70 series, launched on Tuesday and shipping on December 4, is the Chinese tech giant’s first line of smartphones running on HarmonyOS Next. However, users who wish to can still choose the older, Android-based HarmonyOS 4.3, according to Richard Yu Chengdong, chairman of Huawei’s consumer business group.”
Norm diffusion in cyber governance: China as an emerging norm entrepreneur? - International Affairs researches - “This research also demonstrates that instead of using a single diffusion mechanism, China has relied on a dynamic combination of socialization and positive incentives which are driven by both state-led actors and private sectors to diffuse its cyber norms and approaches at regional and international levels.”
Alibaba’s DingTalk sees Hong Kong as pathway to expansion of collaboration app - South China Morning Post reports - “We will leverage the international influence of the Hong Kong market to accelerate DingTalk’s global development,” said Yang Meng, president of DingTalk’s global business.
Terabit-scale high-fidelity diamond data storage - Nature publishes - “High-speed readout through plane and volume imaging is demonstrated with a high fidelity exceeding 99%, showing that the approach addresses the practical demands of digital data storage and provides a promising solution for future storage requirements.”
AI
Japan Earmarks Extra $9.9 Billion for Chips and AI This Year - Bloomberg reports - “Japan is allocating another ¥1.5 trillion ($9.9 billion) to boost its chip and artificial intelligence endeavors including moonshot foundry project Rapidus Corp.”
HUDERIA: New tool to assess the impact of AI systems on human rights - Council of Europe launches - “It can be used by both public and private actors to help identify and address risks and impacts to human rights, democracy and the rule of law throughout the lifecycle of AI systems.”
ByteDance seeks $1.1 mln damages from intern in AI breach case, report says - Reuters reports - “China's ByteDance is suing a former intern for $1.1 million, alleging he deliberately attacked its artificial intelligence large language model training infrastructure, a case that has drawn widespread attention within China amid a heated AI race.”
How new digital workers will lead to an unlimited age - Time owner opinions (sales CEO of SalesForce) - “This shift to intelligent digital labor is already unlocking capacity across industries. It’s no longer constrained by human availability or physical limits, allowing businesses to scale their operations while driving down costs and improving responsiveness, or by geographical limits — opening opportunities preciously limited by location.”
Cyber proliferation
Poland’s former spy chief arrested over refusal to testify to parliament - Financial Times reports - “Poland’s former spy chief was detained and dragged before parliament on Monday as part of a probe into whether the previous rightwing government misused spyware to put its opponents under surveillance.”
Bounty Hunting
Russia arrests ransomware attacker Wazawaka - Yahoo News reports - “The Russian state news agency РИА Новости (translated on BlueSky by the Center for Strategic Research’s Oleg Shakirov) reported that the Kaliningrad Interior Ministry and Russian prosecutors sent a case of “a programmer accused of creating a malicious program” to court.”
Nebraska Man Pleads Guilty in Multi-Million Dollar “Cryptojacking” Case - Department of Justice reports - “Parks created and used a variety of names, corporate affiliations and email addresses, including emails with domains from corporate entities he operated called “MultiMillionaire LLC” and “CP3O LLC,” to register numerous accounts with the cloud providers and to gain access to massive amounts of computing processing power and storage that he did not pay for. Parks used those fraudulently obtained resources to mine various cryptocurrencies including Ether, Litecoin and Monero.”
Vodka maker Stoli files for bankruptcy in US after ransomware attack - Stoli files - “In August 2024, the Stoli Group’s IT infrastructure suffered severe disruption in
the wake of a data breach and ransomware attack. The attack caused substantial operational issues throughout all companies within the Stoli Group, including Stoli USA and KO, due to the Stoli Group’s enterprise resource planning (ERP) system being disabled and most of the Stoli Group’s internal processes (including accounting functions) being forced into a manual entry mode. These systems will be fully restored no earlier than in the first quarter of 2025”What's happening in cyber insurance pricing? - Insurance Business reports - ”If you have a premium binding in 2018 at $100,000, you can see how that premium tracked over the course of the hard market, to where we are today where that same premium would be $264,000.”
No reflections this week other than edge device security continues to be the plague on all our houses (see below)… but we have a plan here…
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Device Confiscated by Russian Authorities Returned with Monokle-Type Spyware Installed
Cooper Quintin, Rebekah Brown, and John Scott-Railton alleged that the Russian FSB install implants on devices when they detain individuals. The interesting aspect is it appears it might be developed commercially in Russia.
This joint investigation with First Department, a legal assistance organization, found spyware covertly implanted on a phone returned to a Russian programmer accused of sending money to Ukraine after he was released from custody.
He describes being subjected to beatings and an intense effort to recruit him as an informant for the Russian Federal Security Service (FSB).
Our analysis finds that the spyware placed on his device allows the operator to track a target device’s location, record phone calls, keystrokes, and read messages from encrypted messaging apps, among other capabilities.
The spyware bears many similarities to the Monokle family of spyware, previously reported on by Lookout Mobile Security, which they attribute to the “Special Technology Center,” a contractor to the Russian government.
Our analysis also finds certain differences from previously-reported samples of Monokle spyware, suggesting that it is either an updated version of Monokle or new software created by reusing much of the same code.
further reporting here:
https://theins.press/en/news/276867
BlueAlpha Abuses Cloudflare Tunneling Service for GammaDrop Staging Infrastructure
Insikt Group alleged this operation was undertaken by Gamaredon, a group operating out of Sevastopol, working under the directive of the Russian Federal Security Services FSB Centre 18 Centre for Information Security TsIB. The attack chain is rather basic other than the misuse of CloudFlare services.
BlueAlpha continues to target Ukrainian entities with spearphishing campaigns, leveraging HTML smuggling attachments to deliver Visual Basic Script VBScript)-based malware GammaLoad.
BlueAlpha has recently started using Cloudflare Tunnels to conceal staging infrastructure used by GammaDrop, an increasingly popular technique used by cybercriminal threat groups to deploy malware.
BlueAlpha continues to use domain name system DNS fast-fluxing of GammaLoad command-and-control C2 infrastructure to complicate tracking and disruption of C2 communications to preserve access to compromised systems.
This campaign has been ongoing since at least early 2024 and has remained largely consistent in its techniques, tactics, and procedures TTPs, with only slight changes in tooling and infrastructure.
https://go.recordedfuture.com/hubfs/reports/cta-ru-2024-1205.pdf
Snowblind: The Invisible Hand of Secret Blizzard
Black Lotus Labs details what they alleged is the compromise and use of Pakistani command and control infrastructure to deploy their own implants. APT piggybacking in action..
[We] uncovered a longstanding campaign orchestrated by the Russian-based threat actor known as “Secret Blizzard” (also referred to as Turla). This group has successfully infiltrated 33 separate command-and-control (C2) nodes used by Pakistani-based actor, “Storm-0156.”
In December 2022, Secret Blizzard initially gained access to a Storm-0156 C2 server and by mid-2023 had expanded their control to a number of C2s associated with the Storm-0156 actor. From their vantage point within these servers, Secret Blizzard leveraged the pre-existing access obtained by Storm-0156 to deploy their own malware, “TwoDash” and “Statuezy,” into a handful of networks linked to various entities within the Afghan government.
https://blog.lumen.com/snowblind-the-invisible-hand-of-secret-blizzard/
Microsoft has also reported on this:
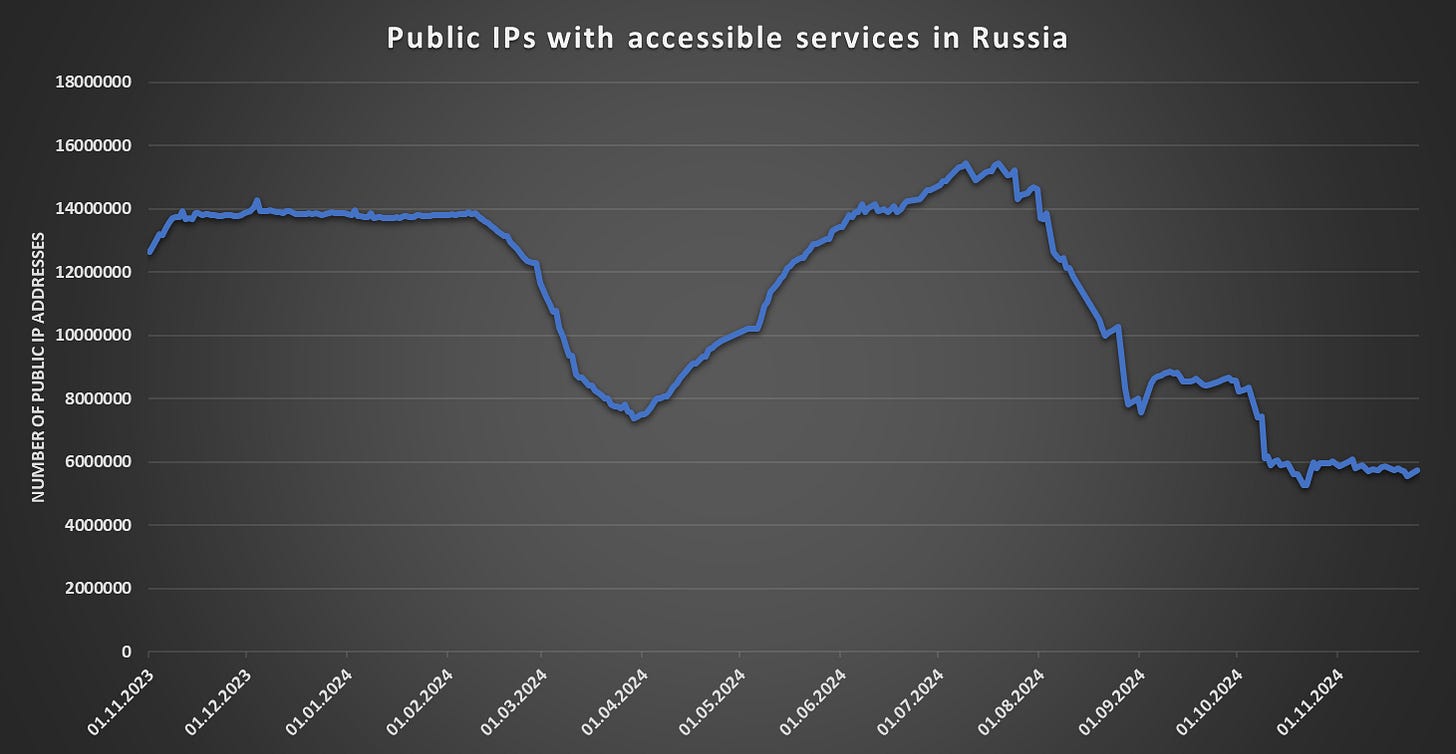
The strange case of disappearing Russian servers
Jan Kopriva notices an interesting change in internet posture of Russia.
https://isc.sans.edu/diary/rss/31476
Reporting on China
U.S. Organization in China Targeted by Attackers
Symantec detail several alleged intrusions of US institutions in China. This set of events should serve as a warning to all.
A large U.S. organization with a significant presence in China was the subject of a targeted attack earlier this year, during which the attackers obtained a persistent presence on its network, seemingly for the purpose of intelligence gathering. The attack was likely carried out by a China-based threat actor, since some of the tools used in this attack have been previously associated with Chinese attackers
..
The file textinputhost.dat was previously reported by Sophos and RecordedFuture as being leveraged by China-based espionage group Crimson Palace in attacks against Southeast Asia. In that case, it was used in conjunction with an executable named rc.exe. The same file name was also used by the attackers who conducted this attack.
https://www.security.com/threat-intelligence/us-china-espionage
MOONSHINE Exploit Kit and DarkNimbus Backdoor Enabling Earth Minotaur’s Multi-Platform Attacks
Joseph C Chen and Daniel Lunghi detail what they alleged is a weakly linked Chinese campaign exploiting old days. Exploiting the patch gap must be working for them given the scale of the deployment. If your organisation needs evidence to focus on addressing said patch gaps (as vendors or customers) this should be it..
Trend Micro researchers investigated a group named Earth Minotaur that used the MOONSHINE exploit kit in the wild. MOONSHINE, which has over 55 servers identified as of 2024, has been updated with more exploits and functions compared to its previous version reported in 2019.
MOONSHINE exploit kit targets vulnerabilities in instant messaging apps on Android devices, primarily affecting Tibetan and Uyghur communities.
They also discovered an unreported Android backdoor, DarkNimbus, that was used by Earth Minotaur. This backdoor also has a Windows version.
Earth Minotaur uses MOONSHINE to deliver the DarkNimbus backdoor to Android and Windows devices, targeting WeChat, and possibly making it a cross-platform threat.
MOONSHINE exploits multiple known vulnerabilities in Chromium-based browsers and applications, requiring users to update software regularly to prevent attacks.
These findings are not strong enough for attribution to a known threat actor; however, they highlight the connections that exist between multiple campaigns attributed to Chinese operations, and their sharing of malware families. It also adds another group to the long list of Chinese threat actors that are using Shadowpad.
https://www.trendmicro.com/en_us/research/24/l/earth-minotaur.html
Reporting on North Korea
Analysis of Kimsuky Threat Actor's Email Phishing Campaign
Genians details what they alleged is a recent North Korean phishing campaign. Interesting they have moved to Russian infrastructure for their emails..
Stimulate the curiosity of email recipients by incorporating various themes and materials
Attempts to hijack accounts of North Korea researchers and figures from related organizations for several years
Evading tracking by shifting email attack base from Japan to Russia
Malwareless attack strategy is also used in conjunction with threats closely related to familiar financial life
Reporting on Iran
APT35 Forges Recruitment Sites, Launches Attacks on Aerospace and Semiconductor Industries in Multiple Countries
TheatBook details what they alleged is an Iranian campaign against some very specific sectors which one might infer all have military applications.
The analysis revealed the following findings:
The attack activities mainly involve the aerospace and semiconductor industries, with regional distribution in the United States, Thailand, the United Arab Emirates, Israel, etc.
The group uses forged recruitment sites and corporate sites to host white and black components; it uses site access or VPN access to lure targets into downloading and executing malicious processes.
During the attack, legitimate internet resources such as OneDrive, Google Cloud, and GitHub were utilized.
..
We also captured a fake site attacking a semiconductor company, where the attacker uses access restrictions to lure target users to download and install a VPN program with a malicious payload.
https://threatbook.io/blog/id/1095
Reporting on Other Actors
iVerify Mobile Threat Investigation Uncovers New Pegasus Samples
Matthias Frielingsdorf details at a high-level how their visibility across 2,500 devices highlighted seven infections. The interesting point of this is that these 2,500 are really self selecting and highly sensitised to the risk.
2,500 of our users jumped at the chance to scan their devices.
The results of those scans validated what we already assumed: if you scan for it, you will find it. We uncovered seven Pegasus infections – a number that might seem small, but represents a massive red flag in the world of mobile security.
These weren't just recent infections. Our analysis revealed a complex timeline of compromise: one exploit from late 2023 on iOS 16.6, another potential Pegasus infection in November 2022 on iOS 15, and five older infections dating back to 2021 and 2022 across iOS 14 and 15.
Our investigation detected 2.5 infected devices per 1,000 scans – a rate significantly higher than any previously published reports. However, it's crucial to understand the context of this data:
Targeted Scanning: These 2,500 devices represent populations most likely to be targeted by advanced spyware
Not a Global Representation: This sample is not indicative of iVerify’s entire device population
High-Risk Focus: Devices belonged to journalists, government officials, and corporate executives.
https://iverify.io/blog/iverify-mobile-threat-investigation-uncovers-new-pegasus-samples
Unidentified Threat Actor Utilizes Android Malware to Target High-Value Assets in South Asia
Unattributed but clumsy..
The sample was part of a targeted attack on highly valued individuals in southern Asia. The team observed that the unknown actor tried to deliver the Android payload via WhatsApp which seems like a terrible move from the threat actor’s viewpoint. The victim received a total of four payloads with different names, three of which were the same size, hinting at an effort by the threat actor to compromise the victim. The apps were named “Best Friend, Best-Friend 1, Friend, best”. All four apps had the same command and control server. During analysis, it was found that the code for the Android payloads was obfuscated. The app was installed and was concealed within seconds while operating in the background.
..
The attack was aimed at high-value targets in the Southern Asian region. Based on the knowledge we gained about the victim; we believe it was carried out by an APT group that remains unidentified or if not then an unknown threat actor. The continued use of SpyNote is notable, as it highlights the threat actors’ preference for leveraging this tool to target high-profile individuals despite being publicly available on various underground forums and telegram channels.
Discovery
How we find and understand the latent compromises within our environments.
Detecting WiFi dumping via direct WinAPI calls and introduction to “Immutable Artifacts”
Daniel Koifman details how to detect this scenario..
We can leverage Sysmon’s Event ID 7 (WHICH IS DISABLED BY DEFAULT!), in order to alert on any unknown EXEs that are calling “wlanapi.dll”.
Defence
How we proactively defend our environments.
Enhanced Visibility and Hardening Guidance for Communications Infrastructure
CISA et al release this in the wake of SALT TYPOON
The UK already has a higher set of requirements through its Telecommunications Security Regulations 2022, the code of practice can be found here:
Incident Writeups & Disclosures
How they got in and what they did.
The Curious Case of an Egg-Cellent Resume
The DFIR Report does what they do best with this end-to-end writeup
https://thedfirreport.com/2024/12/02/the-curious-case-of-an-egg-cellent-resume/
Vulnerability
Our attack surface.
CVE-2024-5910 Expedition: Missing Authentication Leads to Admin Account Takeover
…
Missing authentication for a critical function in Palo Alto Networks Expedition can lead to an Expedition admin account takeover for attackers with network access to Expedition.
Note: Expedition is a tool aiding in configuration migration, tuning, and enrichment. Configuration secrets, credentials, and other data imported into Expedition is at risk due to this issue.
https://security.paloaltonetworks.com/CVE-2024-5910
SonicWall Releases Security Updates for SMA100 SSL-VPN Products
…
A vulnerability in the SonicWall SMA100 SSLVPN allows a remote authenticated attacker can circumvent the certificate requirement during authentication.
..
Use of Cryptographically Weak Pseudo-Random Number Generator (PRNG) in the SonicWall SMA100 SSLVPN backup code generator that, in certain cases, can be predicted by an attacker, potentially exposing the generated secret.
…
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0018
Offense
Attack capability, techniques and trade-craft.
BootExecute EDR Bypass
Rad is back…
Boot Execute allows native applications—executables with the NtProcessStartup entry point and dependencies solely on ntdll.dll—to run prior to the complete initialization of the Windows operating system. This occurs even before Windows services are launched. Historically, attackers have exploited this mechanism as a rudimentary persistence method. However, utilizing this feature requires administrative privileges, both to modify the corresponding registry key and to place the executable within the %SystemRoot%\System32 directory.
Because these native applications execute before security mechanisms are fully operational, this presents an opportunity to disrupt antivirus (AV) and endpoint detection and response (EDR) systems by deleting critical application files as we run with SYSTEM privileges.
https://github.com/rad9800/BootExecuteEDR
Corrupted Files to Bypass Detection: Technical Analysis
khr0x details how maliciously crafted Microsoft Word documents which are corrupted but recoverable in order to deliver their final payloads.
Our study revealed a vulnerability in document and archive structures. By manipulating specific components like the CDFH and EOCD, attackers can create corrupted files that are successfully repaired by applications but remain undetected by security software. As a result, we face a situation when security systems have not yet developed a clear logic for detecting such attacks, exposing the security of their users.
https://any.run/cybersecurity-blog/corrupted-files-attack/
Data exfiltration from remote session using loopback audio driver
James Brine gives another exfiltration path to consider..
I've created a tool that encodes and transmits data over a loopback audio device (or a speaker and microphone if you like the idea of listening to noise) with the idea of extracting information from a remote session (Citrix, RDP, TeamViewer, VNC etc.) where sound output is available and other mechanisms such as shared clipboard, remote file transfer are not - or some more covert channel is needed.
Rusty-Telephone encodes files into audio signals and transmits them between systems using audio loopback. It uses:
FSK modulation with multiple frequencies for data encoding
Reed-Solomon error correction
SHA-256 checksums for data integrity
Sync sequences and preambles for reliable transmission
Digital signal processing for audio analysis
https://github.com/referefref/Rusty-Telephone
Exploitation
What is being exploited..
Zyxel security advisory: protecting against recent firewall threats
More edge device pain..
Zyxel is aware of recent attempts by threat actors to target Zyxel firewalls through previously disclosed vulnerabilities, as reported in Sekoia’s blog post. We confirm that firewall firmware version 5.39, released on September 3, 2024, and later versions are immune to the mentioned exploitation, as we have addressed all known vulnerabilities, including CVE-2024-11667, and performed a series of security enhancements in version 5.39.
BSI’s advisory on the exploitation
On November 21, Zyxel published a security advisory confirming Sekoia's report of Helldown ransomware attacks and stating that the vulnerability exploited in the latest firmware version 5.39, released on September 3, was not reproducible and therefore customers with the latest firmware and swapped credentials were no longer at risk.
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Decrypting CryptProtectMemory without code injection
Nathan Blondel walks us through, will have potential value in the memory forensics space..
To summarize, to decrypt memory that was protected with
CryptProtectMemoryand theCRYPTPROTECTMEMORY_SAME_PROCESSflag in another process, one must:
Get the encrypted data, and its length in the target process
Get the value of the
CookieandCreateTimevalue in theEPROCESSstructure of the target processGet the value of
cng!RandomSaltandcng!g_ShaHash
If the length of the encrypted data is a multiple of
8, then
derive a
3DESkey from twoSHA1hashes, starting with an initial state ofg_ShaHashthe first one with the state updated with
b"aaa"and then updated with theCookieandCreateTime, taken in fullthe second one with the state updated with
b"bbb"and then updated with theCookieandCreateTime, truncated to the first4bytesElse, if the length of the encrypted data is a multiple of
16, then
derive an
AES128key from theSHA1hash starting with an initial state ofg_ShaHash, and updated withCookieandCreateTime, truncated to the first16bytes.Finally, decrypt the memory using the corresponding key and cipher, as well as an IV of
cng!RandomSalt, all16bytes forAES128, or the first8bytes for3DES.
https://blog.slowerzs.net/posts/cryptdecryptmemory/
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Evaluation Melissa: insights into the successful (co)operation in combating ransomware
On the global retreat of correspondent banks - bifurcation of finance
Does the Foreign Office need a new Information Research Department? - likely no, but a some good challenge.
Artificial intelligence
Books
Nothing this week
Events
The Last Four Years of Cyber Policy: A Retrospective - Center for Strategic & International Studies - December 9th
The Kernel of the Matter: CrowdStrike and the Future of Software Regulation - December 12th
Videos of the week
Attacking and defending downstream oil infrastructure
Inside West Point: bridging the gap between humans and machines using data science, particularly in cyber, intelligence, and special operations.
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.