Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note..
In the high-level this week:
Telecommunications Security
US alleges China hacked calls of 'very senior' political figures - Reuters reports - While a large number of Americans' metadata likely has been stolen, U.S. officials understand that "the purpose of the operation was more focused," Neuberger said. "We believe ... the actual number of calls that they took, recorded and took, was really more focused on very senior political individuals,
Implications of Salt Typhoon Attack and FCC Response - FCC outlines -
Affirming Cybersecurity Obligations and Increasing Accountability
New Compliance Framework
Seeking Broader Action
Telecommunications Security bill arrives in senate - Senator Wyden introduces - “To require the Federal Communications Commission to promulgate certain cybersecurity rules.”
Offensive cyber operations exercise Crossed Swords gets underway in Tallinn - NATO announces - “The goal of the Crossed Swords exercise is to practice and experiment in a field that is highly relevant in today’s world,” stated Dr Mart Noorma, Director of NATO CCDCOE. “We are a defensive alliance by nature. In order to understand how our adversaries think we also need to master offensive cyber skills. Deterrence in cyberspace is complicated, but we continue doing our best to keep our nations safe.”
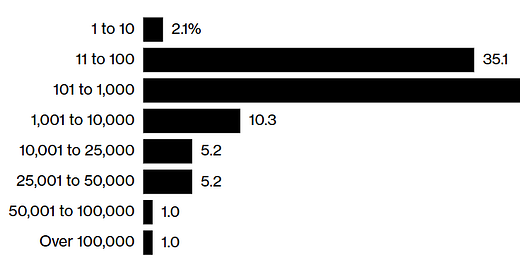
Ransomware Gangs’ Merciless Attacks Bleed Small Companies Dry - Bloomberg reports - this graph is interesting although underlying dataset source is not shared:
Okta's Costly Cyber Security Failures: A $60 Million Lesson in Transparency - Benzinga reports - “Amid these security threats and litigation issues, Okta stock has declined 35% in the last 5 years despite its revenue increasing substantially from just $399 million in 2019 to $2.26 billion in 2023.” -from September but interesting nevertheless due to business value impact
Exploring the AI-ICT Security Nexus - The United Nations Institute for Disarmament Research publishes - “This brief draws from multiple sources3 to create a simplified model of these steps, and is intended to inform policymakers and diplomats engaged in international ICT security discussions. The proposed model, referred to as the ICT Intrusion Path, maps the various actions based on where they are taking place with respect to the targeted networks and examines them through the lens of AI’s potential role in both malicious ICT acts and in the related defences.”
Information integrity online and the European democracy shield - European Parliament Think Tank publishes - “The increased focus on information integrity by multilateral organisations makes room for coordinating actions to boost the resilience of information ecosystems more broadly, safeguarding human rights. This concept ties in with key parts of the work planned under the future 'European democracy shield'.”
Data free flow with trust: current landscape, challenges and opportunities - Université Grenoble Alpes publishes - “This article explores the efforts to achieve ‘data free flow with trust', highlighting concerns around foreign government access to personal data for national security and law enforcement. Governments increasingly seek data held by private firms, raising significant data protection challenges and leading to mistrust among jurisdictions and the implementation of data localization mandates.”
Reporting on/from China
US House to vote to provide $3 billion to remove Chinese telecoms equipment - Reuters reports - “FCC Chair Jessica Rosenworcel last week again called on the U.S. Congress to provide urgent additional funding, saying the program to replace equipment in the networks of 126 carriers faces a $3.08 billion shortfall "putting both our national security and the connectivity of rural consumers who depend on these networks at risk."
Studying China in the Absence of Access: Rediscovering a Lost Art - SAIS China Research Center publishes - “To address the challenges facing China specialists today, when access to China has once more become problematic, Johns Hopkins University School of Advanced International Studies (SAIS) China studies called upon four leading China specialists who studied and were trained in the 1960s and 1970s, when China was essentially closed to American researchers.”
Chinese Assessments of Starlink and U.S.-China Space Relations - Interpret: China analyses - “First, they reveal how misperceptions and ambiguities about U.S. space technologies can magnify PRC threat assessments. While the United States tends to obfuscate where it is weak in space, the authors of these articles tend to fill in those blanks by ascribing functions, scale, and operational status to U.S. space capabilities that likely far exceed reality”
Assessing the Impact of China ICT Presence in Underdeveloped Economies: Evidence from the African States - Journal of the Knowledge Economy asserts - “The result further suggests that with the presence of Chinese ICTs, African states may have better access to advanced digital technology that can bring more economic stability and values. Therefore, this study recommends African countries to craft more China technology adoption strategies that involve investment in vocational education and digital skills development.” - warning here on multiple fronts - would be interesting to see if a similar analysis undertaken by Western academics showed the same thing.
China Telecom releases the country's largest superconducting quantum computer "Tianyan-504" - IT Home reports - “With the 504-bit real machine connected to the quantum computing cloud platform and serving external services, the "Tianyan" cloud platform has achieved dual upgrades in computing power scale and computing power type. It is the largest quantum computing cluster in China, consisting of one 24-bit machine, two 176-bit machines and one 504-bit machine , and provides 5 types of high-performance simulators and the Cqlib quantum programming framework.”
AI
Artificial Intelligence (AI) Model Risk Management - Monetary Authority of Singapore publishes - “This information paper sets out good practices for AI and Generative AI model risk management that were observed during the review, focusing on those relating to governance and oversight, key risk management systems and processes, and development and deployment of AI.”
Cyber proliferation
US senators, green groups call for accountability over hacking of Exxon critics - Reuters reports - “In late November, Reuters reported that more than 500 email accounts belonging to environmentalists and their allies were targeted by mercenary hackers between 2015 and 2018 as part of an effort to help beat back climate change investigations and lawsuits being mounted against Exxon.”
Bounty Hunting
Yanbian Silverstar and Volasys Silverstar - Rewards for Justice bounties - ”Rewards for Justice is offering a reward of up to $5 million for information that leads to the disruption of financial mechanisms of persons engaged in certain activities that support North Korea (Democratic People’s Republic of Korea, DPRK), including the exportation of workers from North Korea to generate revenue, money laundering, and specified cyber-activity and actions that support North Korea’s weapons of mass destruction proliferation.”
DOJ indicts 14 North Koreans working for US firm - US Department of Justice indicts -
The workers operated from China and Russia, funneling funds to support the DPRK regime.
Yanbian Silverstar and Volasys Silverstar employed at least 130 North Korean IT workers under fake U.S. identities.
Over six years, the scheme generated $88M for North Korea, with workers expected to earn $10K monthly.
Leaders like Jong Song Hwa incentivized workers with competitions, bonuses, and prizes for top earners.
U.S. indictments expose their use of identity theft, fake credentials, and extortion tactics.
Is Anyone Happy With the UN Cybercrime Convention? - Lawfare opines - “These protocols only need to be submitted by at least 60 states, and while they should preferably be adopted by consensus, a two-thirds majority vote of the states parties present and voting would be enough to adopt them. This means that nothing prevents Russia or China, supported by 60 states, from proposing the adoption of a protocol that includes a provision against extremism-related offenses—opening the door for broad domestic interpretations.”
Air Traffic Control:Urgent FAA Actions Are Needed to Modernize Aging Systems - US Government Accountability Office publishes - “Our testimony highlights that 17 of these unsustainable systems are especially concerning. However, FAA doesn't plan to complete modernization projects for some of these systems for at least 10 years. FAA also doesn't have plans to modernize other systems in need—3 of which are at least 30 years old.”
Lloyd’s of London Launches First-of-its-kind Consortium Built on HITRUST Certification to Shape the Future of Cyber Insurance - HITRUST announces - “The newly formed consortium with Lloyd's of London unites additional capital from a global network of Moody’s recognized AA-rated insurers to establish an innovative shared risk facility. This novel initiative leverages the proven link between HITRUST certification and superior and measurable risk management, enabling insurers to confidently deliver enhanced and more consistent insurance products. The facility is designed to scale as additional insurers join, ensuring greater capacity to meet the evolving demands of organizations with HITRUST certifications across the globe.”
Reflections this week are around threat hunting maturity in organisations. It is clear that adversary capability means it will be required more. It is also clear that relying on known knowns such as indicators of compromise will only increasingly get you so far. In discussions with various organisations there appears to be a real opportunity to help organisations both demonstrably upskill in their ability to effectively threat hunt whilst ensuring they have the requisite observability to do so in a range of environments..
.. then we have the managed security service provider community/sector and what they should be doing in this space where the clients do not and rely on them ..
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Two Russian Android Spyware Families from Gamaredon APT
Lookout details an interesting alleged Russian operation which relies on social engineering to get down onto Android devices.
Lookout has discovered BoneSpy and PlainGnome Android surveillance families and attributed them to the Russian Gamaredon (Primitive Bear, Shuckworm) APT group associated with the Federal Security Service (FSB).
BoneSpy has been in use since at least 2021, while PlainGnome first appeared in 2024. Both families are still active at the time of writing.
BoneSpy and PlainGnome target former Soviet states and focus on Russian-speaking victims. Lookout assesses this targeting may be related to worsening relations between these countries and Russia since the outbreak of the Ukraine invasion.
Both BoneSpy and PlainGnome collect data such as SMS messages, call logs, phone call audio, photos from device cameras, device location, and contact lists.
PlainGnome acts as a dropper for a surveillance payload, stored within the dropper package, while BoneSpy is deployed as a standalone application.
…
PlainGnome consists of a two-stage deployment in which a very minimal first stage drops a malicious APK once it’s installed. While the first and second stages use some variation on the Telegram package name, the actual functionality presented to the user is essentially the same as that observed in previous BoneSpy samples using the “image gallery” theme. This lure theme continued through most of PlainGnome’s deployment throughout 2024.
https://www.lookout.com/threat-intelligence/article/gamaredon-russian-android-surveillanceware
Phishing attacks targeting Ukrainian defense sector
CERT-UA warns of this alleged Russian operation which uses basic phishing as the initial attack mechanism. Notable for the sectors being targeted more than anything..
[We] detected a new series of cyberattacks targeting Ukrainian defense companies and security and defense forces. The phishing emails mimicked official messages from the Ukrainian League of Industrialists and Entrepreneurs. The emails advertised a conference held on December 5th in Kyiv, aimed at aligning the products of domestic defense industry companies with NATO standards.
The emails also contained a URL titled "Attachment contains important information for your participation". Clicking the link and opening the attached files allowed hackers to infect the victim's computer with malware.
The culprit is the UAC-0185 group, which has been active since at least 2022. The group has primarily focused on compromising the accounts in messaging apps like Signal, Telegram, and WhatsApp, as well as military systems DELTA, Teneta, and Kropyva. The hackers have also launched a number of cyberattacks to get unauthorized access to the PCs of defence companies' workers and representatives of the security
https://cip.gov.ua/en/news/cert-ua-warns-of-phishing-attacks-targeting-ukrainian-defense-sector
Frequent freeloader part II: Russian actor Secret Blizzard using tools of other groups to attack Ukraine
Microsoft alleges that the Russian state is benefiting from cybecrime initial access in its activities against Ukraine. A good reminder for those threat scenarios..
After co-opting the tools and infrastructure of another nation-state threat actor to facilitate espionage activities, as detailed in our last blog, Russian nation-state actor Secret Blizzard used those tools and infrastructure to compromise targets in Ukraine. Microsoft Threat Intelligence has observed that these campaigns consistently led to the download of Secret Blizzard’s custom malware, with the Tavdig backdoor creating the foothold to install their KazuarV2 backdoor.
Between March and April 2024, Microsoft Threat Intelligence observed Secret Blizzard using the Amadey bot malware relating to cybercriminal activity that Microsoft tracks as Storm-1919 to download its backdoors to specifically selected target devices associated with the Ukrainian military. This was at least the second time since 2022 that Secret Blizzard has used a cybercrime campaign to facilitate a foothold for its own malware in Ukraine.
Reporting on China
Operation Digital Eye
Aleksandar Milenkoski & Luigi Martire detail a campaign which is somewhat technically novel, although inspired by work done in the commercial red team space, but also finite in length. The sectoral targeting is also interesting by this alleged Chinese threat actor..
From late June to mid-July 2024, a suspected China-nexus threat actor targeted large business-to-business IT service providers in Southern Europe, an activity cluster that we dubbed ‘Operation Digital Eye’.
The intrusions could have enabled the adversaries to establish strategic footholds and compromise downstream entities.
The threat actors used a lateral movement capability indicative of the presence of a shared vendor or digital quartermaster maintaining and provisioning tooling within the Chinese APT ecosystem.
The threat actors abused Visual Studio Code and Microsoft Azure infrastructure for C2 purposes, attempting to evade detection by making malicious activities appear legitimate.
Our visibility suggests that the abuse of Visual Studio Code for C2 purposes had been relatively rare in the wild prior to this campaign. Operation Digital Eye marks the first instance of a suspected Chinese APT group using this technique that we have directly observed.
..
The attack campaign, which we have dubbed Operation Digital Eye, took place from late June to mid-July 2024, lasting approximately three weeks. The targeted organizations provide solutions for managing data, infrastructure, and cybersecurity for clients across various industries, making them prime targets for cyberespionage actors.
Likely China-based Attackers Target High-profile Organizations in Southeast Asia
Symantec detail what they alleged in a Chinese operation where the initial vector is not documented but the length of operation is. Looks like a red team stomping around from the tools and tradecraft..
Threat actors using tools linked to China-based APT groups have targeted multiple high-profile organizations in Southeast Asia, including government ministries in two different countries, an air traffic control organization, a telecoms company, and a media outlet.
The attacks, which have been underway since at least October 2023, appear to have intelligence gathering as their main goal. The attackers use a variety of both open-source and living-off-the-land tools in their operations.
While attribution to a specific threat group cannot be determined, multiple tools used in the campaign have links to several China-based actors (see Tools section for details). Of note is the use of a proxy tool called Rakshasa and a legitimate application file used for DLL sideloading, both of which were used previously by the Chinese advanced persistent threat (APT) group known as Earth Baku (aka APT41, Brass Typhoon).
A typical attack involves the use of a remote access tool that leverages Impacket to execute commands via WMI (Windows Management Instrumentation). The attackers then install keyloggers, password collectors, and reverse proxy tools (Rakshasa, Stowaway, ReverseSSH) to maintain connections to attacker-controlled infrastructure. The threat actors also install customized DLL files that act as authentication mechanism filters, allowing them to intercept login credentials.
..
The following activity occurred on one of the targeted organizations’ networks. In this instance, the attackers remained active for at least three months, between June and August 2024, focusing on intelligence gathering—specifically collecting and likely exfiltrating data of interest. While this case highlights a particular approach, in other attacks, the threat actors employed additional tactics, techniques, and procedures (TTPs), such as DLL sideloading, and leveraged tools like Rakshasa and SharpGPOAbuse, among others, to achieve their objectives.
https://www.security.com/threat-intelligence/china-southeast-asia-espionage
MoqHao Leverages iCloud and VK in Campaign Targeting Apple IDs and Android Devices
Hunt.io detail an criminal campaign which allegedly originates from China. The use of legitimate infrastructure for staging is of note..
MoqHao, also known as Wroba and XLoader, is a mobile malware family linked to Roaming Mantis, a cybercrime group believed to be operating out of China. Malicious payloads are usually delivered through "Smishing" attacks or SMS phishing targeting mobile devices.
..
As shown in Figure 4, the malicious APK file is downloaded from cvws.icloud-content[.]com. This is not a spoofed domain but legitimate Apple infrastructure, which the operators abuse to host and distribute the malware.
https://hunt.io/blog/moqhao-icloud-vk-targets-apple-android
Reporting on North Korea
Hack, heist, and havoc: The Lazarus Group’s triple threat to global cybersecurity
Arif Perdana, Muhamad Erza Aminanto and Bayu Anggorojati bring an academic view of the group to bare..
The Lazarus Group, a North Korean state-sponsored cyber threat actor, has become a significant player in cybersecurity. This case study examines the group’s cyber operations through a structured analysis of their techniques and tactics, which include social engineering, malware injection, disruption, evasion, and espionage. By progressing through these stages, the Lazarus Group combines human factor exploitation with technical prowess to execute high-impact campaigns, such as hacking, theft, and widespread disruption. This case classifies these campaigns into espionage, financial heists, and destructive operations, advancing North Korea’s strategic interests while exposing critical vulnerabilities in global cybersecurity. The analysis reveals how the interplay between human and organisational weaknesses, alongside systemic technical vulnerabilities, enables these large-scale cybercrimes. Key lessons are drawn from these operations, emphasising the necessity of addressing human and technical factors in cybersecurity frameworks. Furthermore, the case highlights the broader societal effects of cyberattacks, especially on critical infrastructure, and underscores the global impact of cybercrime. To counter such sophisticated threats, this study stresses the importance of international cooperation, cybersecurity awareness, and a comprehensive approach that addresses human and technical vulnerabilities.
https://journals.sagepub.com/doi/pdf/10.1177/20438869241303941
Reporting on Iran
Inside a New OT/IoT Cyberweapon: IOCONTROL
Team82 detail what they alleged is Iranian OT/IoT capability.. we have been warned..
Team82 obtained a sample of a custom-built IoT/OT malware called IOCONTROL used by the Iran-affiliated attackers to attack Israel- and U.S.-based OT/IoT devices.
IOCONTROL has been used to attack IoT and SCADA/OT devices of various types including IP cameras, routers, PLCs, HMIs, firewalls, and more. Some of the affected vendors include: Baicells, D-Link, Hikvision, Red Lion, Orpak, Phoenix Contact, Teltonika, Unitronics, and others.
We’ve assessed that IOCONTROL is a cyberweapon used by a nation-state to attack civilian critical infrastructure.
Our analysis of IOCONTROL includes an in-depth look at the malware’s capabilities and unique communication channels to the attackers’ command-and-control infrastructure.
…
This specific sample was extracted from a Gasboy/ORPAK device, which is a fuel system platform. However, IOCONTROL was used to attack IoT and SCADA devices of various types including IP cameras, routers, PLCs, HMIs, firewalls, and more from different vendors such as Baicells, D-Link, Hikvision, Red Lion, Orpak, Phoenix Contact, Teltonika, Unitronics, and others.
https://claroty.com/team82/research/inside-a-new-ot-iot-cyber-weapon-iocontrol
Reporting on Other Actors
Cloudflare’s pages.dev and workers.dev Domains Increasingly Abused for Phishing
Numbers are interesting in this report by PhishLabs
https://www.fortra.com/blog/cloudflare-pages-workers-domains-increasingly-abused-for-phishing
Discovery
How we find and understand the latent compromises within our environments.
Behind the Mask: Unpacking Impersonation Events
Jonathan Johnson details these new features which will help discover shenanigans..
Introduction
Microsoft continuously marches forward in providing us security events that uncovers activity that has long been used by attackers. In this write-up I want to document and talk about 3 new events that are provided in the Threat-Intelligence (TI) ETW Provider:
THREATINT_PROCESS_IMPERSONATION_UP (EID 33)
THREATINT_PROCESS_IMPERSONATION_REVERT (EID 34)
THREATINT_PROCESS_IMPERSONATION_DOWN (EID 36)
These events became publicly available in Windows 24H2 and have previously been in preview builds for the past couple of years. With these events now being in 24H2 defenders have a good way of picking up on token impersonation attacks. However, there are some caveats that should be mentioned about these events.
https://jsecurity101.medium.com/behind-the-mask-unpacking-impersonation-events-fca909e08d00
Unveiling Dark Internet Service Providers: Bulletproof Hosting
Knownsec 404 team show the way of the mapping..
In this paper, we first introduce bulletproof hosting services, then focus on describing the cybercriminal activities of the bulletproof hosting service provider ELITETEAM and its owned network segment. Finally, based on the ZoomEye cyberspace search engine [1], combined with the concept of “behavioural mapping”, we observe and analyse the asset mapping data of this network segment. Through open ports, SSL certificate Subject values, SSL certificate fingerprints, JARM values, and unique HTTP content, we attempt to associate and expand to discover more suspected bulletproof hosting networks.
Enhancing Cyber Resiliency of Industrial IoT Attack Detection
Jermaine M. Cameron tantalises with this use case for FHE..
This praxis contributes to the body of knowledge by empirically evaluating the performance and feasibility of using fully homomorphic encryption as a privacypreserving technique in machine learning-based DDoS attack detection in industrial IoT environments. First, this praxis demonstrates that machine learning models can successfully perform inference on encrypted industrial IoT network traffic data for intrusion detection. This praxis addresses the computational limitations of fully homomorphic encryption in privacy-preserving machine learning by implementing a sampling methodology to efficiently perform inference on encrypted network traffic data and assess the execution time of different models
https://www.proquest.com/openview/025b98cfdd6a18c543025d3caffec41e/1.pdf
Defence
How we proactively defend our environments.
Automated Configuration for Defender for Identity
Nathan McNulty automates..
This is a collection of commands that will help automate the configuration of the Defender for Identity settings. To use this, you must obtain the sccauth value and xsrf-token value from the browser and use it to create cookies and headers for our API calls. This is because we are using an internal API to configure settings, and there isn't a public way to get the right tokens.
https://github.com/nathanmcnulty/nathanmcnulty/tree/master/DefenderForIdentity/AutoConfig
Introducing Supply-Chain Firewall: Protecting Developers from Malicious Open Source Packages
Ian Kretz releases this which may have utility is more mature environments..
a Python tool for preventing the installation of malicious and vulnerable PyPI and npm packages. Its primary goal is to protect software engineers’ development workstations from compromise via exactly these sorts of software supply-chain attacks.
https://securitylabs.datadoghq.com/articles/introducing-supply-chain-firewall/
Incident Writeups & Disclosures
How they got in and what they did.
Electrica Group is under a cyber attack -
Romanian electricity supplier..
Electrica Group is under a cyber attack. The teams of specialists are working closely with the national cybersecurity authorities to manage and resolve the incident, aiming to address the situation as quickly as possible, identify the source of the attack, and limit its impact.
We want to emphasize that the Group's critical systems have not been affected, and any disruptions in interaction with our consumers are the result of protective measures for internal infrastructure. These measures are temporary and are designed to ensure the security of the entire system.
At this time, all specific response protocols have already been activated in accordance with internal procedures and current regulations. Our primary priority remains maintaining continuity in the distribution and supply of electricity, as well as protecting the managed personal data and the operational data of all entities within Electrica Group.
Radiant Capital Incident Update
Allegedly North Korea...
We have an important update on the October 16, 2024 incident in which Radiant Capital was targeted by a highly sophisticated cyberattack that resulted in a loss valued at approximately $50M USD. On October 17, 2024, Radiant published a post-mortem of the attack and thereafter retained Mandiant, a leading cybersecurity firm, to assist in the investigation, particularly with on-device forensics. In parallel, the Radiant Capital DAO engaged zeroShadow and Hypernative for on-chain asset tracking and enlisted SEAL 911 for additional support.
..
Mandiant attributes this attack to UNC4736, commonly referred to as AppleJeus or Citrine Sleet. Mandiant assesses with high-confidence that UNC4736 has a Democratic People’s Republic of Korea (DPRK) nexus. Specifically, this group is aligned with DPRK’s Reconnaissance General Bureau (RGB) and has close ties with TEMP.Hermit.
https://medium.com/@RadiantCapital/radiant-capital-incident-update-e56d8c23829e
Vulnerability
Our attack surface.
BadRAM: Breaching Processor Security via Rogue Memory Modules
Jesse De Meulemeester, Luca Wilke, David Oswald, Thomas Eisenbarth, Ingrid Verbauwhede and Jo Van Bulck detail this vulnerability which will only apply to the very niche situation such as supply chain..
Modern computers increasingly use encryption to protect sensitive data in DRAM, especially in shared cloud environments with pervasive data breaches and insider threats. AMD's Secure Encrypted Virtualization (SEV) is a cutting-edge technology that protects privacy and trust in cloud computing by encrypting a virtual machine's (VM's) memory and isolating it from advanced attackers, even those compromising critical infrastructure like the virtual machine manager or firmware.
We found that tampering with the embedded SPD chip on commercial DRAM modules allows attackers to bypass SEV protections — including AMD’s latest SEV-SNP version. For less than $10 in off-the-shelf equipment, we can trick the processor into allowing access to encrypted memory. We build on this BadRAM attack primitive to completely compromise the AMD SEV ecosystem, faking remote attestation reports and inserting backdoors into any SEV-protected VM.
SD Express Card Flaw Exposes Laptops and Consoles to Memory Attacks
gesser details the next DMA access vector when you are next the device..
DaMAgeCard attack targets memory directly thru SD card reader
Offense
Attack capability, techniques and trade-craft.
pytune.py
Yuya Chudo releases this which will need detection around..
Pytune is a post-exploitation tool for enrolling a fake device into Intune with mulitple platform support.
https://github.com/secureworks/pytune
GimmeShelter.py
RWXstoned releases a tool which if used in an intrusion should be easy enough to detect..
GimmeShelter.py is a lightweight Python script which will help you get a good view of what a Windows environment looks like, and highlight opportunities for hiding/running malware from unusual modules, or memory setups.
https://rwxstoned.github.io/2024-12-06-GimmeShelter/
DCOM Upload & Execute
Eliran Nissan releases this lateral movement tool which some will want to get after..
DCOM Lateral movement POC abusing the IMsiServer interface
https://www.deepinstinct.com/blog/forget-psexec-dcom-upload-execute-backdoor
The solution contains 2 projects
DCOMUploadExec - A C++ project which hosts the lateral movement attack code
AssemblyPayload - A .NET DLL that pops a MessageBox. It is the default payload DCOMUploadExec uses
https://github.com/deepinstinct/DCOMUploadExec
Quality of Life Beacon Object Files
Andy gives a list of Cobalt Strike BOFs blue teams should likely develop detection engineering analytics for..
A curated collection of BOFs for operational ease.
Simplified submodule management for seamless updates.
Contributions from trusted developers and projects in the community.
https://github.com/ZephrFish/QoL-BOFs
NativeBypassCredGuard
Ricardo Ruiz gives a memory fingerprint to go after..
NativeBypassCredGuard is a tool designed to bypass Credential Guard by patching WDigest.dll using only NTAPI functions (exported by ntdll.dll). It is available in two flavours: C# and C++.
https://github.com/ricardojoserf/NativeBypassCredGuard
Process Inject Kit
Rasta Mouse ports this kit..
The built in fork and run process injection techniques can be change with the
PROCESS_INJECT_SPAWNandPROCESS_INJECT_EXPLICIThooks.This repo provides the following:
Source code implementing the built-in techniques.
Aggressor script to implement the hooks.
Visual Studio solution to compile and generate a distribution directory.
https://github.com/rasta-mouse/process-inject-kit
Exploitation
What is being exploited..
Cleo Software Actively Being Exploited in the Wild
John Hammond details this in the wild exploitation..
This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable. We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released.
Based on our analysis, all versions prior to and including 5.8.0.21 are vulnerable:
Cleo Harmony® (5.8.0.21)
Cleo VLTrader® (5.8.0.21)
Cleo LexiCom® (5.8.0.21)
Our team is working to reach the Cleo team to report our findings and develop a new patch to fully mitigate exploitation. This blog will be frequently updated as more details emerge.
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Malimite
Laurie Wired released this at Objective by the Sea..
is an iOS decompiler designed to help researchers analyze and decode IPA files.
https://github.com/LaurieWired/Malimite
Decrypting Full Disk Encryption with Dissect
Guus Beckers gives a walkthrough on how to apply Dissect..
One of the most popular requests has been the capability to use Dissect in combination with common disk encryption methods like Microsoft’s BitLocker or its Linux equivalent LUKS. Internally at Fox-IT we were able to already use these capabilities. With the release of Dissect version 3.17 these capabilities are now also available to the community at large.
Of course, a blog post is not complete without a demo. In this scenario a data acquisition has been performed against a disk protected with BitLocker.
https://blog.fox-it.com/2024/12/11/decrypting-full-disk-encryption-with-dissect/
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Nothing this week
Project MUSE - Interregional Investment Networks and Innovation Growth: The “Buzz-and-pipeline” Perspective - “This article studies the impact of cross-border capital flows on innovation from a regional perspective rather than a national one, integrating the “buzz-and-pipeline” model into the study of interregional investment networks and innovation.”
The PQC Migration Handbook - Revised and Extended Second Edition
CCS '24: Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security
Artificial intelligence
Nothing this week
Books
Events
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.