CTO at NCSC Summary: week ending February 4th
We all look like heroes when initiatives started 6 or so years ago converge with the threat..
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week the Ivanti clean-up continues, including this CISA directive for US agencies to pull the devices and restore to an assured state before they are able to redeploy 👏.
In the high-level this week:
UK Cyber security academic startup accelerator programme 2024-25: phase 1
Individuals based in a UK academic institution can apply for a share of up to £800,000 to join the cyber security academic startup accelerator programme (CyberASAP).
Standards for Software Liability: Focus on the Product for Liability, Focus on the Process for Safe Harbor - The conclusion is that all of these fields would face the same question: How buggy is too buggy?
FTC Order Will Require Blackbaud to Delete Unnecessary Data, Boost Safeguards to Settle Charges its Lax Security Practices Led to Data Breach - “Blackbaud’s shoddy security and data retention practices allowed a hacker to obtain sensitive personal data about millions of consumers,” said Samuel Levine, Director of the FTC’s Bureau of Consumer Protection
INTERPOL-led operation targets growing cyber threats - Some 1,300 suspicious IP addresses or URLs have been identified as part of a global INTERPOL operation targeting phishing, malware and ransomware attacks
Position Paper on Quantum Key Distribution - by France, Germany, the Netherlands and Sweden - Due to current and inherent limitations, QKD can however currently only be used in practice in some niche use cases. For the vast majority of use cases where classical key agreement schemes are currently used it is not possible to use QKD in practice. Furthermore, QKD is not yet sufficiently mature from a security perspective
The UK Product Security and Telecommunications Infrastructure (Product Security) regime - comes into effect on 29 April 2024.
Palm Coast Man Arrested For Wire Fraud And Aggravated Identity Theft Charges -According to the indictment, between August 2022 and March 2023, Urban committed wire fraud and aggravated identity theft, which resulted in at least $800,000 being stolen from at least five different victims.
Implementing Regulation on the adoption of a European Common Criteria-based cybersecurity certification scheme - This Regulation specifies the roles, rules and obligations, as well as the structure of the European Common Criteria-based cybersecurity certification scheme in accordance with the European cybersecurity certification framework set out in Regulation (EU) 2019/881.
US Critical Infrastructure Protection: Agencies Need to Enhance Oversight of Ransomware Practices and Assess Federal Support - US Government Accountability Office in action.
ENISA Single Programme Document - 2024 to 2026 - Outlines their strategy.
ENISA Security Assessments - Evaluations & Certifications - State of Play 2018-2022 (published Jan 2024) - the report focuses on the evolution of the number of assessed ICT solutions and assessment bodies in the past 5 years. It takes into account the various ways to assess cybersecurity of ICT solutions such as standards, national, and private, certification schemes and methodologies.
”How a Group of Israel-Linked Hackers Has Pushed the Limits of Cyberwar” - by Wired “From repeatedly crippling thousands of gas stations to setting a steel mill on fire, Predatory Sparrow’s offensive hacking has now targeted Iranians with some of history's most aggressive cyberattacks.”
Engineering Personal Data Protection in EU Data Spaces - attempts to contextualise the main design principles regarding protection of personal data and demonstrate how to engineer personal data protection through two use cases of an envisioned EU data space in the pharmaceutical domain.
UN Cybercrime Convention must not become a tool to undermine international human rights standards - Signatories stress that the Convention should only move forward if it pursues a specific goal of combating cybercrime without endangering the human rights and fundamental freedoms of those it seeks to protect, nor undermining efforts to improve cybersecurity for an open internet.
UAE sued in $2.8bn US lawsuit over 'dark PR' disinformation op - The lawsuit filed by the trader Hazim Nada in the District of Columbia alleges that starting in 2017 the UAE paid a Swiss private intelligence firm, Alp Services, to "seriously damage" his reputation and business in a sweeping smear campaign.
Defending Democracy
[US] Cyber chiefs confident 2024 election will be ‘most secure’ in history - NSA boss sees no indication of cyberattacks planned amid concerns about foreign interference.
2nd EEAS Report on Foreign Information Manipulation and Interference Threats - This Second EEAS Report on Foreign Information Manipulation and Interference (FIMI) threats sheds light on the current threat landscape, based on 750 investigated FIMI incidents. It raises questions about effective countermeasures and sets out a comprehensive response framework, helping all stakeholders in cooperating more effectively in fighting information manipulation.
Safer Internet Lab publications - various papers which have applicability as we think about what to do.
Reporting on/from China
China hacking threatens US infrastructure, FBI director warns, as Volt Typhoon botnet foiled - The FBI director, Chris Wray, told the House select committee “China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities, if or when China decides the time has come to strike,”
Reuters - US disabled Chinese hacking network targeting critical infrastructure, sources say
Secure by Design Alert: Security Design Improvements for SOHO Device Manufacturers - CISA and the FBI created this guidance based upon recent and ongoing activity targeting small office/home office (SOHO) routers by malicious cyber actors—particularly the People’s Republic of China (PRC)-sponsored Volt Typhoon group.
China Telecom Central Intelligent Computing Center is put into operation in Wuhan, supporting the deployment of large models with trillions of parameters - providing 5000PFLOPS of intelligent computing power
Fintech giant Ant Group sets up AI unit led by former Google researcher - NextEvo will be in charge of Ant’s own LLM, Bailing, as well as AI algorithms and engineering, natural language processing (NLP) and AI-generated content operations, sources said.
2024 CSRankings Global Computer Security Academic Institutions and Personnel Analysis - In the field of computer security, judging from the four major conferences published around the world from 2014 to 2024,
Artificial intelligence
North Korea’s Artificial Intelligence Research: Trends and Potential Civilian and Military Applications - The study indicates that North Korean scientists opted for RL for wargaming purposes since they view the running speed of RL as faster than that of other methods. While the specifics of the agent and environment are not explained, information related to the rewards provides insight into what North Korea aims to achieve with this simulation.
US CDAO Launches First DOD AI Bias Bounty Focused on Unknown Risks in LLMs - The exercises are conducted to generate novel approaches to algorithmically auditing and red teaming AI models, facilitating experimentation with addressing identified risks, and ensuring the systems are unbiased, given their particular deployment context.
China Morning Post - US wants cloud firms to report foreign users building AI applications - The US Commerce Department starts process requiring American cloud firms to disclose when a foreign user trains an artificial intelligence model
Explainable Artificial Intelligence for Bias Identification and Mitigation in Demographic Models
Cyber proliferation
Dozens in Jordan targeted by authorities using NSO spyware, report finds -Guardian says “Findings suggest Jordan is relying on cyberweapon to quash dissent and its use is ‘staggeringly widespread’”
Five billion people being tracked by Patternz surveillance tool - The commercial surveillance tool Patternz is collecting data from billions of users without permission. This is according to the report “Europe’s hidden security crisis” by the Irish Council for Civil Liberties (ICCL).
The reflections this week are around the CISA Security by Design alert for SOHO routers mentioned above The team at NCSC highlighted this morning that from April 2025, any SOHO router provided or managed by a ISP in the UK will be legally required to have these properties which is 🔥. We all look like heroes when initiatives started 6 or so years ago converge with the threat..
Think someone else would benefit? Share:
All attribution is by others and not the UK Government, please see the legal text at the end.
Have a lovely Friday
Ollie
Cyber threat intelligence
Who is doing what to whom and how.
Reporting on Russia
Microsoft, HPE hacks by Russia are just the tip of the iceberg
Joseph Menn reporting on this keep an on the SEC disclosure tracker.
Microsoft said late Thursday that it had found more victims and was in the process of notifying them. A spokesperson declined to say how many. But three experts in and out of government said that the attack was deeper and broader than the disclosures to date reveal.
Two said that more than 10 companies, and perhaps far more, are expected to come forward. The experts asked not to be named so as to maintain relations with the victims.
Pawn Storm Uses Brute Force and Stealth Again
Feike Hacquebord and Fernando Merces detail these alleged Russian credential collection campaigns used by this threat actor which every organisation should read, understand and respond to.
Since at least 2019, it has employed brute-force attacks (first from dedicated servers and then with additional anonymization layers such as commercial VPN services), Tor, and infrastructure that is very likely being shared with more standard cybercriminal use. Recently, Pawn Storm has been using more advanced and stealthy methods that are both loud and aggressive, which makes it difficult to determine what is happening in the victim’s network post-compromise.
https://www.trendmicro.com/en_us/research/24/a/pawn-storm-uses-brute-force-and-stealth.html
Compromised routers are still leveraged as malicious infrastructure to target government organizations in Europe and Caucasus
Some reporting which creates a potential/alleged overlap - more compromised routers!
We identified additional malicious files and infrastructure which we believe with high confidence are part of the same campaign. The campaign targeted government organisations in Ukraine and Poland at least (and possibly in Azerbaijan as well), started on 2023-12-13 at the latest, and abused legitimate Ubiquity network devices as infrastructure. We could not reliably link the described campaign with APT28 in particular.
The general sophistication and stealth level of the described toolset and associated activities are quite low, but are a perfect fit to continuously put pressure on Ukraine's (and supporters') cyberdefence capabilities, while keeping the investment level reasonable, as well as enabling basic intelligence collection (technical reconnaissance, credentials collection).
https://harfanglab.io/en/insidethelab/compromised-routers-infrastructure-target-europe-caucasus/
The Bear and The Shell: New Campaign Against Russian Opposition
The attack analyzed employed a NASA-themed lure to deceive the victim to execute an open-source multiplatform reverse shell named as HTTP-Shell. During the investigation, [our] researchers found many other artifacts related to attacks having the same TTPs and conducted in the same days, discovering that the first note about this malicious campaign was made public by the Netherlands-based investigative journalism group Bellingcat on X social network.
https://blog.cluster25.duskrise.com/2024/01/30/russian-apt-opposition
Scaly Wolf uses White Snake stealer against Russian industry
Russia having its own malware issues..
Stealers remain one of the most popular types of malware distributed by attackers. However, many of them now have additional functionality, which allows them to be effectively used for targeted and complex attacks.
The malware-as-a-service model allows attackers not to waste time developing malware and immediately receive a finished product. Moreover, commercial malware, like legitimate malware, is often publicly available in the form of “hacked” versions.
Despite the ban of many malware developers from distributing it in Russia and the CIS, attackers find ways to modify it and sometimes use it in these regions. This once again emphasizes the importance of monitoring shadow resources in order to identify such malware before it is used against Russian organizations.
Reporting on China
Stately Taurus Targets Myanmar Amidst Concerns over Military Junta’s Handling of Rebel Attacks
Alleged Chinese activity in response to regional issues using basic phishing capabilities which have been used by numerous threat actors. Should not present a challenge for mature organisations to protect against, individuals likely at greater risk.
The first campaign observed took place on November 9th 2023 and came under our attention after a malicious archive was submitted to VirusTotal with the name Analysis of the third meeting of NDSC.zip.
The malware sample involves an Optical Disc Image (ISO) containing LNK shortcuts, extended with a similar but slightly deviating methodology as described in campaign #1.
https://csirt-cti.net/2024/01/23/stately-taurus-targets-myanmar/
Unveiling TeleBoyi: Chinese APT Group Targeting Critical Infrastructure Worldwide
Yi-Chin Chuang and Yu-Tung Chang gave this presentation in Japan which alleges an enduring campaign across a variety of sectors.
https://jsac.jpcert.or.jp/archive/2024/pdf/JSAC2024_1_8_yi-chin_yu-tung_en.pdf
UNC5221: Unreported and Undetected WIREFIRE Web Shell Variant
Further web shell discovered around this alleged Chinese campaign against Ivanti devices.
[We] discovered an additional variation of a Python web shell currently tracked as WIREFIRE (by Mandiant) and GIFTEDVISITOR (by Volexity) with similar capabilities, hidden in a different file. This discrepancy is presumably attributed to the threat actor’s intent to circumvent detection mechanisms and to avoid detections by public YARA rules known.
https://quointelligence.eu/2024/01/unc5221-unreported-and-undetected-wirefire-web-shell-variant/
Reporting on Volt Typhoon’s “JDY” Botnet Administration Via Tor Sparks Questions
Interesting analysis by the DCSO team here which may provide the CTI community a thread to follow.
Based on the ExoneraTor results and the Tor network consensus data analyzed, the possibility that 67.205.139[.]175 was not used by Volt Typhoon as a Tor exit relay to obfuscate the origin of connections to the C2 server located at 45.63.60[.]39 appears to emerge.
Unmasking HiddenFace
Dominik Breitenbacher provides an analysis of this alleged Chinese group and a previously unknown impact. Also shared insights into their victimology..
MirrorFace’s most complex backdoor yet - we found that besides LODEINFO, the group's go-to backdoor, MirrorFace also deployed a yet unknown backdoor that we named HiddenFace.
https://jsac.jpcert.or.jp/archive/2024/pdf/JSAC2024_2_8_Breitenbacher_en.pdf
Cutting Edge, Part 2: Investigating Ivanti Connect Secure VPN Zero-Day Exploitation
Matt Lin, Robert Wallace, John Wolfram, Dimiter Andonov and Tyler Mclellan provide further insights of techniques and implants stemming from the investigations. Of note is the risk that this is a now a pile in situation where various groups and adopting similar techniques highlighting the attribution challenge.
we detail additional tactics, techniques, and procedures (TTPs) employed by UNC5221 and other threat groups during post-exploitation activity across our incident response engagements. We also detail new malware families and variants to previously identified malware families being used by UNC5221. We acknowledge the possibility that one or more related groups may be associated with the activity described in this blog post. It is likely that additional groups beyond UNC5221 have adopted one or more of these tools.
https://www.mandiant.com/resources/blog/investigating-ivanti-zero-day-exploitation
Reporting on North Korea
Analysis of attack activities of APT-C-26 (Lazarus) group using weaponized open source PDF readers
Chinese reporting on alleged North Korean activity showing a creativity on their persistence mechanism. That is get the malicious version of the PDF reader down on targets and then trigger by sending them malicious PDFs.
[We] discovered that the APT-C-26 organization weaponized the open source project SumatraPDF and turned it into an attack tool by implanting malicious code. Specifically, these malicious codes are triggered when SumatraPDF processes PDF documents specially designed by attackers. These codes activate the malicious payload in memory and establish a connection with the remote control server (C2), thereby downloading a backdoor program to steal sensitive user information.
Reporting on Iran
Iran International Reveals Tehran-Based Cyber Group Targeting Israeli Hospital
Alleged Iranian campaign going after a Hospital, interesting that mainstream media is now piling into Cyber Threat Intelligence attribution.
The cyber group “Black Shadow” (“Saye-ye Siah” in Persian), which targeted Ziv Medical Center in the northern Israeli city of Safed in November is in fact a tech company which works under the registered name of “Raahkarha-ye Fanavari-e Etela’at-e Jahatpardaz.”
According to Iran International’s investigative journalist Mojtaba Pourmohsen, the two operational offices of the “Black Shadow” cyber group are located in Tehran.
The website of the company states that a group of “faithful and committed youth” has launched it in line with “The Second Step of the Revolution.”
https://www.iranintl.com/en/202401267648
Reporting on Other Actors
Threat Intelligence of Abused Public Post-Exploitation Frameworks
Masafumi Takeda and Tomoya Furukawa gives a sense of the level of misuse of tooling in offensive campaigns.
https://jsac.jpcert.or.jp/archive/2024/pdf/JSAC2024_1_9_takeda_furukawa_en.pdf
Kasseika Ransomware Deploys BYOVD Attacks Abuses PsExec and Exploits Martini Driver
Emmanuel Panopio, Christian Jason Geollegue, Julius Keith Estrellado, Christian Alpuerto, Shawn Austin Santos, Emmanuel Roll, Rhio Manaog, Gerald Fernandez, Don Ovid Ladores, Raighen Sanchez, Raymart Yambot, Francesca Villasanta, and Sophia Nilette Robles show it now takes more people than in a Football team to understand some threats. Initial access is phishing but the post exploitation tradecraft shows a degree of sophistication is what you need to know..
In the Kasseika ransomware case that we investigated, we observed that it used targeted phishing techniques for initial access, as well as to gather credentials from one of the employees of its target company
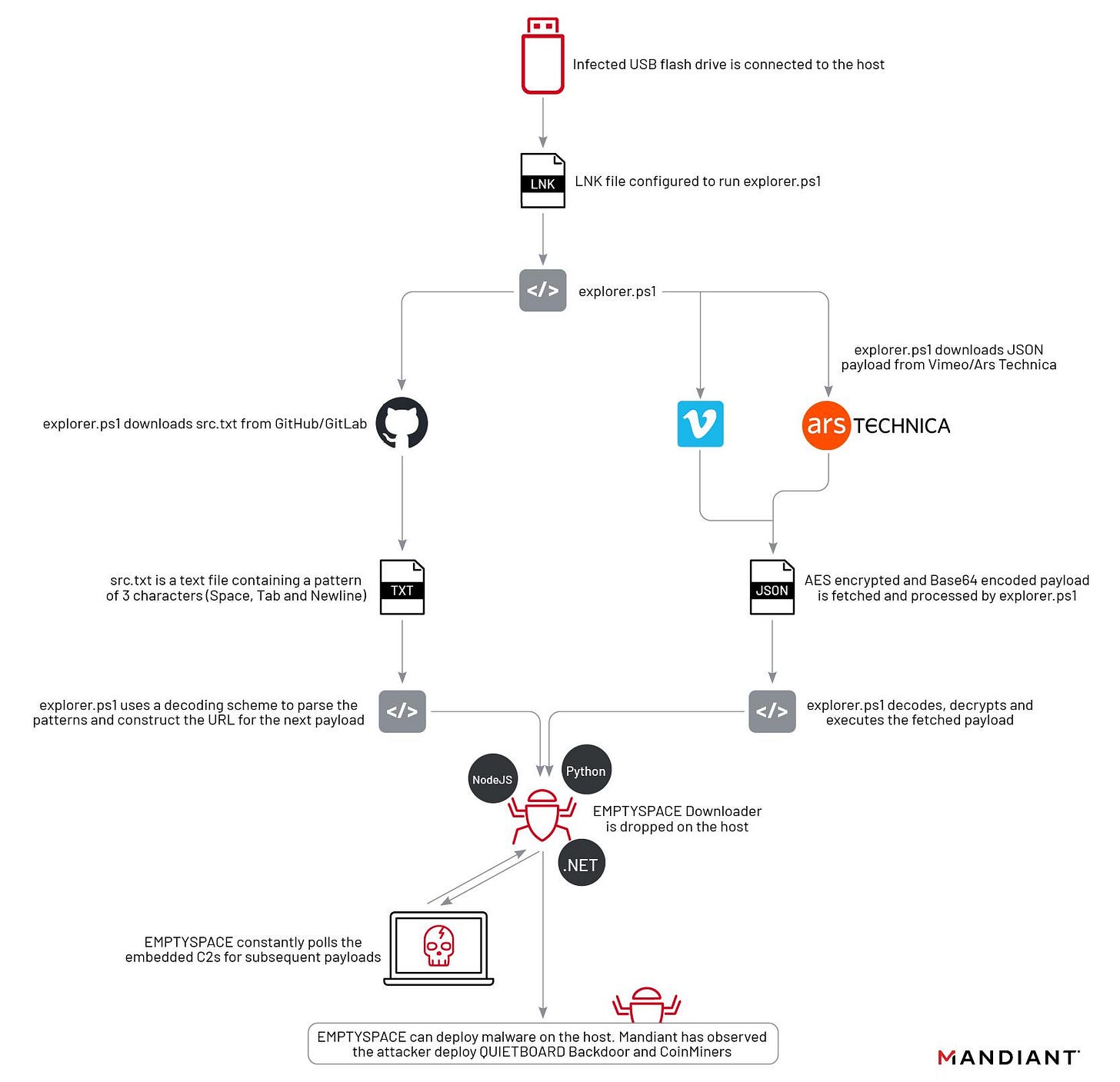
Evolution of UNC4990: Uncovering USB Malware's Hidden Depths
Diana Ion, Jae Young Kim, Muhammad Umair, Panagiotis Antoniou and Yash Gupta highlight the technical complexity of some criminal campaigns.
Despite relying on the age-old tactic of weaponizing USB drives, UNC4990 continues to evolve their tools, tactics and procedures (TTPs). The actor has moved from using seemingly benign encoded text files to hosting payloads on popular websites such as Ars Technica, GitHub, GitLab, and Vimeo.
The legitimate services abused by UNC4990 (including Ars Technica, GitHub, GitLab, and Vimeo) didn’t involve exploiting any known or unknown vulnerabilities in these sites, nor did any of these organizations have anything misconfigured to allow for this abuse. Additionally, the content hosted on these services posed no direct risk for the everyday users of these services, as the content hosted in isolation was completely benign. Anyone who may have inadvertently clicked or viewed this content in the past was not at risk of being compromised.
https://www.mandiant.com/resources/blog/unc4990-evolution-usb-malware
Hundreds of network operators’ credentials found circulating in the Dark Web
Not going to lie, this is of concern..
[We] conducted a thorough scan of the Dark Web and identified over 1,572 compromised customers of RIPE, Asia-Pacific Network Information Centre (APNIC), the African Network Information Centre (AFRINIC), and the Latin America and Caribbean Network Information Center (LACNIC), resulting from infostealer infections.
The curious case of DangerDev@protonmail.me
What a modern criminal cloud actor looks like
They know their way around AWS they go beyond the basic EC2 abuse and have skills to setup (more advanced) persistence methods;
Uses a combination of automation scripts and hands-on keyboard activity. For example the testing and enumeration of AWS access keys was definitely automated as we kept seeing the original access keys being used to make calls on set times. However they also performed lots of activity through the management console;
Some OPSEC was observed, as an example the TA didn’t use the GetCallerIdentity command. Which is commonly observed in attacks as it’s basically a whoami for AWS environments. Additionally we didn’t see many failed API calls, which is often an indicator for a less skilled TA trying every possible action;
Financially motivated, ultimately their goal seemed to be to perform (spear)phishing for financial gain through PayPal lures and cryptocurrency phishing;
The TA was mostly using Indonesian based IP addresses outside of commercial VPN solutions.
https://www.invictus-ir.com/news/the-curious-case-of-dangerdev-protonmail-me
Discovery
How we find and understand the latent compromises within our environments.
Defending against the Attack of the Clone[d website]s!
https://blog.thinkst.com/2024/01/defending-against-the-attack-of-the-cloned-websites.html
SOAPHound and Sigma Detections
SOAPHound — tool to collect Active Directory data via ADWS
https://medium.com/falconforce/soaphound-tool-to-collect-active-directory-data-via-adws-165aca78288c
Detections
https://github.com/tsale/Sigma_rules/blob/main/windows_exploitation/ADWS_abuse.yml
https://github.com/tsale/Sigma_rules/blob/main/windows_exploitation/SOAPHound.yml
Defence
How we proactively defend our environments.
Unleashing the power of cloud with containerisation
Guidance from the UK’s National Cyber Security Centre
Today we are releasing security guidance on using containerisation, so it felt like the perfect opportunity to discuss how to get the most from it, and how it fits into using a cloud platform.
https://www.ncsc.gov.uk/blog-post/unleashing-the-power-of-cloud-with-containerisation
Incident Writeups & Disclosures
How they got in and what they did.
23andMe
This is quite some time for an attack to occur over without a response.
a threat actor orchestrated a credential stuffing attack during the period from May 2023 through September 2023
https://oag.ca.gov/system/files/CA%20AG%20-%20CA%20Notification%20Letters.pdf
Cloudflare Thanksgiving 2023 security incident
Interesting writeup which shows the value that zero-trust can bring.
We want to emphasize to our customers that no Cloudflare customer data or systems were impacted by this event. Because of our access controls, firewall rules, and use of hard security keys enforced using our own Zero Trust tools, the threat actor’s ability to move laterally was limited. No services were implicated, and no changes were made to our global network systems or configuration.
From November 14 to 17, a threat actor did reconnaissance and then accessed our internal wiki (which uses Atlassian Confluence) and our bug database (Atlassian Jira). On November 20 and 21, we saw additional access indicating they may have come back to test access to ensure they had connectivity.
https://blog.cloudflare.com/thanksgiving-2023-security-incident
Vulnerability
Our attack surface.
CVE-2023-40547
Critical bug that exists in every Linux boot loader signed in the past decade
When retrieving files via HTTP or related protocols, shim attempts to allocate a buffer to store the received data. Unfortunately, this means getting the size from an HTTP header, which can be manipulated to specify a size that's smaller than the received data. In this case, the code accidentally uses the header for the allocation but the protocol metadata to copy it from the rx buffer, resulting in an out-of-bounds write,
https://github.com/rhboot/shim/commit/0226b56513b2b8bd5fd281bce77c40c9bf07c66d
Missing signs: how several brands forgot to secure a key piece of Android
Tom Hebb shows key management and code signing etc. still remain a challenge for some vendors.
We recently discovered that Android devices from multiple major brands sign APEX modules—updatable units of highly-privileged OS code—using private keys from Android’s public source repository. Anyone can forge an APEX update for such a device to gain near-total control over it. Rather than negligence by any particular manufacturer (OEM), we believe that unsafe defaults, poor documentation, and incomplete CTS coverage in the Android Open Source Project (AOSP) were the main causes of this issue.
https://rtx.meta.security/exploitation/2024/01/30/Android-vendors-APEX-test-keys.html
Offense
Attack capability, techniques and trade-craft.
How to grant admin consent to an API programmatically
Sahil Malik shows how it can be done to solve a development challenge, but as AppRoleAssignment.ReadWrite.All MS Graph app role bypasses the consent process by design it is pretty powerful.
https://winsmarts.com/how-to-grant-admin-consent-to-an-api-programmatically-e32f4a100e9d
Teams Breaker
A phishing kit for Teams that defensive functions will want to understand.
Bypass techniques work across
Group chat
Meeting chat
Other chats
https://github.com/ASOT-LABS/TeamsBreaker
Modern implant design: position independent malware development
A sign of things to come..
Modern in the sense of being easy to write, easy to maintain, flexible and modular. These modern implants add support for global variables, raw strings and compile time hashing to position independent code which is known to have such limitations as not being able to use global variables and literal strings (besides crafting stack strings).
https://5pider.net/blog/2024/01/27/modern-shellcode-implant-design/
electroniz3r: Take over macOS Electron apps' TCC permissions
This is 6 months old by Wojciech Reguła but important as this is how some macOS tradecraft will occur.
https://github.com/r3ggi/electroniz3r
ThievingFox
Expect use in 3..2..
ThievingFox is a collection of post-exploitation tools to gather credentials from various password managers and windows utilities. Each module leverages a specific method of injecting into the target process, and then hooks internals functions to gather crendentials.
https://github.com/Slowerzs/ThievingFox/
https://blog.slowerzs.net/posts/thievingfox/
Exploitation
What is being exploited.
Actively Exploited Vulnerability in Hitron DVRs: Fixed, Patches Available
Yes, embedded systems keep on being the gift..
As part of the InfectedSlurs discovery, [we]T uncovered vulnerabilities in multiple Hitron DVR device models that are actively exploited in the wild. Hitron devices are manufactured in South Korea by Hitron Systems.
The vulnerability allows an authenticated attacker to achieve OS command injection with a payload delivered via a POST request to the management interface. In its current configuration, it is utilizing device default credentials in the captured payloads.
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
WinDbg Time Travelling Debugging API has arrived
Will be interesting to see how this API / functionality gets leveraged for both offensive research and detection tradecraft.
This interface allows a TTD recording client to interact and interfere with the recorder in order to control and enhance the recording.
The C Bounded Model Checker: Criminally Underused
Philip Zucker makes a strong case here for this powerful capability..
I thought CBMC might be defunct, since it’s main webpage does not show recent development, but actually the github repo is very active. It appears Amazon is investing in it’s usage with a number of significant C projects having CBMC based specs ad verification.
CBMC however runs all possible executions, discovering an erroring value the uninitialized variable could take on.
https://www.philipzucker.com/cbmc_tut/
Beyond Control: Exploring Novel File System Objects for Data-Only Attacks on Linux Systems
Jinmeng Zhou, Jiayi Hu, Ziyue Pan, Jiaxun Zhu, Guoren Li, Wenbo Shen, Yulei Sui, and Zhiyun Qian demonstrate the quality of research coming out of academia.. and a Chinese university at that. The cat and mouse game of counter measures inches on once more..
We make two contributions in this paper: (1) discover critical non-control objects in the file subsystem and (2) analyze their exploitability. This work represents the first study, with minimal domain knowledge, to semi-automatically discover and evaluate exploitable non-control data within the file subsystem of the Linux kernel. Our solution utilizes a custom analysis and testing framework that statically and dynamically identifies promising candidate objects. Furthermore, we categorize these discovered objects into types that are suitable for various exploit strategies, including a novel strategy necessary to overcome the defense that isolates many of these objects. These objects have the advantage of being exploitable without requiring KASLR, thus making the exploits simpler and more reliable. We use 18 real-world CVEs to evaluate the exploitability of the file system objects using various exploit strategies. We develop 10 end-to-end exploits using a subset of CVEs against the kernel with all state-of-the-art mitigations enabled.
https://arxiv.org/abs/2401.17618?s=09
ProcMemScan
Daem0nc0re releases a tool which will be of use to those of you working in the low-level Windows eco-system.
This tool is written for inspecting undebuggable process. Following functionalities are implemented
https://github.com/daem0nc0re/TangledWinExec/tree/main/ProcMemScan
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
The Scourge of Ransomware Victim Insights on Harms to Individuals, Organisations and Society
On Conducting Ethically Sound Psychological Science in the Metaverse
Instrumenting OpenCTI with a Capability for Attack Attribution Support
Artificial intelligence
Risk Taxonomy, Mitigation, and Assessment Benchmarks of Large Language Model Systems
Robust Prompt Optimization for Defending Language Models Against Jailbreaking Attacks
A Framework for Fuzz Target Generation and Evaluation - This framework generates fuzz targets for real-world
C/C++projects with various Large Language Models (LLM) and benchmarks them via theOSS-FuzzplatformA reading list for large models safety, security, and privacy.
Code Generation with AlphaCodium: From Prompt Engineering to Flow Engineering
Navigating AI Challenges in Cybersecurity: Strategies for Industrial and IoT Protection
Books
Nothing this week
Events
Nothing this week
Video of the week - Intelligence Delivered: A Conversation with General Paul Nakasone
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.







As a complete Luddite, I’m always impressed with the names that are created for these hacking groups