Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note. But we did release collectively our edge device guidance as promised to help the UK make the safest place to live and work online..
In the high-level this week:
Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances - NCSC UK publishes with a little help from our friends - “Outlining the expectations for the minimum requirement for forensic visibility, to help network defenders secure organisational networks both before and after a compromise.” - guidance for product vendors - now lets have them implement it.
Security Considerations for Edge Devices - Canadian Centre for Cyber Security (CCCS) publishes with a little help from their friends - “This publication provides organizations with an overview of cyber security considerations and threats relating to edge devices. It also includes examples, recommendations and mitigations that IT professionals can take to reduce the risk of compromise.”
Mitigation Strategies for Edge Devices: Executive Guidance and Mitigation Strategies for Edge Devices: Practitioner Guidance - the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) publishes with a little help from their friends - “This publication offers a high-level summary of existing guidance for securing edge devices” and “This guide is designed for operational staff, cybersecurity staff and procurement staff.”
Secure sanitisation and disposal of storage media - NCSC UK updates - “How to ensure data cannot be recovered from electronic storage media.”
Network security fundamentals (How to design, use, and maintain secure networks.) - NCSC UK publishes for small & medium enterprises - “This guidance provides an introduction to the key topics to consider when designing, maintaining, or using networks that need to be secure and resilient. It will also help you apply the NCSC’s Cyber security design principles to networks.”
Common Challenges in Cybercrime - Europjust and Europol publish - “One important challenge is data management, which requires law enforcement agencies to deal with massive volumes of data, triggering a need for advanced analytic techniques and significant resources which are currently beyond the reach of many agencies. The report notes the ongoing impact of legal uncertainties following the invalidation of the Data Retention Directive, which continues to affect the availability of data for investigations.”
It is time to standardize principles and practices for software memory safety - Robert N. M. Watson guides - “we describe how developing standards for memory-safe systems may be able to help enable remedies by making potential benefit more clear (and hence facilitating clear signalling of demand) as well as permitting interventions”
Bill Gates vs Ren Zhengfei - New Statesman looks at - “The Microsoft and Huawei founders have competing visions of technological dominance. Which will endure?”
Reporting on/from China
Tencent-backed WeBank eyes Web3 expansion in Hong Kong - South China Morning Post reports - “WeBank Technology Services, launched this month, plans to be “deeply involved” in developing the city’s Web3 infrastructure, as it holds a “very open” attitude towards the industry, WeBank’s chief information officer Henry Ma said in an interview.”
China urges Japan to rethink planned hi-tech export bans - South China Morning Post reports - “Restrictions will affect 18 Chinese companies when they come into effect on February 9”
AI
Intolerable Risk Threshold Recommendations for Artificial Intelligence - UC Berkley Center For Long-term Cybersecurity publishes - “In our discussion, we include model harm arising from the risk categories of CBRN weapons, cyber attacks, model autonomy, persuasion and manipulation, deception, toxicity, discrimination and socioeconomic disruption.”
LLM Cyber Evaluations Don't Capture Real-World Risk - Cisco Systems asserts - “We propose a risk assessment framework for LLM cyber capabilities and apply it to a case study of language models used as cybersecurity assistants. Our evaluation of frontier models reveals high compliance rates but moderate accuracy on realistic cyber assistance tasks. However, our framework suggests that this particular use case presents only moderate risk due to limited operational advantages and impact potential”
The Dark Deep Side Of Deepseek: Fine-tuning Attacks Against The Safety Alignment Of Cot-enabled Models - Bristol University publishes - “Specifically, we explore how fine-tuning manipulates the model’s output, exacerbating the harmfulness of its responses while examining the interaction between the Chain of Thought reasoning and adversarial inputs. Through this study, we aim to shed light on the vulnerability of Chain of Thought enabled models to fine-tuning attacks and the implications for their safety and ethical deployment”
Deepseek writes textbook insecure code - Georgi Guninski notices - “This is a textbook example of XSS (Cross Site Scripting).”
Updating the Frontier Safety Framework - Deepmind publishes - “Key updates to the framework include:
Security Level recommendations for our Critical Capability Levels (CCLs), helping to identify where the strongest efforts to curb exfiltration risk are needed
Implementing a more consistent procedure for how we apply deployment mitigations
Outlining an industry leading approach to deceptive alignment risk”
Artificial Intelligence and Cybersecurity: Balancing Risks and Rewards - World Economic Forum opines - “By prioritizing cybersecurity and mitigating risks, organizations can safeguard their investments in AI and support responsible innovation. A secure approach to AI adoption not only strengthens resilience but also reinforces the value and reliability of these powerful technologies.”
The Commission publishes guidelines on AI system definition to facilitate the first AI Act’s rules application - European Commission publishes - “The guidelines on the AI system definition are not binding. They are designed to evolve over time and will be updated as necessary, in particular in light of practical experiences, new questions and use cases that arise. “
Commission publishes the Guidelines on prohibited artificial intelligence (AI) practices, as defined by the AI Act - European Commission publishes - “The guidelines provide legal explanations and practical examples to help stakeholders understand and comply with the AI Act's requirements. This initiative underscores the EU's commitment to fostering a safe and ethical AI landscape”
Decoupling America’s Artificial Intelligence Capabilities from China Act of 2025 - Senator Josh Hawley introduces - “PROHIBITION ON IMPORTATION.—On and after 23 the date that is 180 days after the date of the enactment of this Act, the importation into the United States of arti25 ficial intelligence or generative artificial intelligence technology or intellectual property developed or produced in 2 the People’s Republic of China is prohibited”
Copyright and Artificial Intelligence Part 2: Copyrightability - US Copyright Office publishes - “While recognizing that copyrightability is determined on a case-by-case basis, in this Part the Office sets out the legal principles that govern the analysis and assesses their application to AI-generated content.”
Deep-learning enabled generalized inverse design of multi-port radio-frequency and sub-terahertz passives and integrated circuits - Nature publishes - “Millimeter-wave and terahertz integrated circuits and chips are expected to serve as the backbone for future wireless networks and high resolution sensing. However, design of these integrated circuits and chips can be quite complex, requiring years of human expertise, careful tailoring of hand crafted circuit topologies and co-design with parameterized and pre-selected templates of electromagnetic structures.”
Principles for Artificial Intelligence (AI) and its application in healthcare - British Medical Association publishes - “The BMA advocates, as set out in the principles at the end of this paper, for AI in healthcare to prioritise safety, efficacy, ethics, and equity.”
Cyber proliferation
Israel/United States : Hack-for-hire broker Aviram Azari leaves prison and returns to Israel - Intelligence Online reports - “The private eye is known to have acted as a broker between Indian hack-for-hire firms and Western clients, and notably worked on the Wirecard case. His early release comes as his former partner, Amit Forlit, fights extradition from the United Kingdom to the United States.” - need to buy the article
WhatsApp says journalists and civil society members were targets of Israeli spyware - The Guardian reports - “Nearly 100 journalists and other members of civil society using WhatsApp, the popular messaging app owned by Meta, were targeted by spyware owned by Paragon Solutions, an Israeli maker of hacking software, the company alleged on Friday.”
Italian investigative journalist targeted on WhatsApp by Israeli spyware - The Guardian reports - “An Italian investigative journalist who is known for exposing young fascists within prime minister Giorgia Meloni’s far-right party was targeted with spyware made by Israel-based Paragon Solutions, according to a WhatsApp notification received by the journalist.”
Owner of spyware used in alleged WhatsApp breach ends contract with Italy - The Guardian reports - “A person familiar with the matter said Italy had breached the terms of Paragon’s contract with the government, which does not allow for journalists or members of civil society to be targeted with the spyware.”
The spyware professionals who stand to gain from Trump's return - Intelligence Online reports - “They include Mati Kochavi, among others.” - need to buy the article
NSO Transparency report (archive)- NSO publishes/asserts/spins - “Pegasus does not penetrate computer networks, desktop or laptop operating systems, or data networks. It can be installed only on smartphones and cannot be used to gather information more broadly.” - there is spin and then there is spin.
Bounty Hunting
Expat arrests in Abu Dhabi cyber sector - Intelligence Online reports - “several expats working in the Emirati cyber sector are currently in prison. The murky case involves national security, and the embassies concerned are remaining silent. The situation could have repercussions for Western companies that have worked with those detained.” - need to buy the article
Superseding Indictment Charges Chinese National in Relation to Alleged Plan to Steal Proprietary AI Technology - US Department of Justice announces -
Canadian National Charged With Stealing Approximately $65 Million in Cryptocurrency From Two DeFi Protocols - US Department of Justice announces - “Defendant Exploited Vulnerabilities in the KyberSwap and Indexed Finance Decentralized Finance Protocols to Steal from Investors”
35% Year-over-Year Decrease in Ransomware Payments, Less than Half of Recorded Incidents Resulted in Victim Payments - Chainalysis asserts - “In 2024, ransomware attackers received approximately $813.55 million in payments from victims, a 35% decrease from 2023’s record-setting year of $1.25 billion, and for the first time since 2022, ransomware revenues declined.”
BSI investigates open source software "Nextcloud" - BSI announces its assessment - “In most cases, cyber attacks can be traced back to errors in the program code of the affected applications.” .. “In addition to Nextcloud, the test also included the extensions " Two-Factor Admin Support ", " Two-Factor Email ", " Two-Factor TOTP Provider " and " Two-Factor Webauthn ".”
Reflection this week are the big push the 5EYES and others have done around edge network device and appliance security. From an NCSC perspective we see that needing artisanal forensic techniques to investigate intrusions is not tenable.
We now need device and appliance vendors to read, respond and implement what we have outlined in Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances.
We now also need customers to speak with one voice and stipulate that they do.
This co-ordinated move by supply and demand will lead to a step function change in cyber resilience for all…
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Friday…
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
GRU: Military Unit 54777
Lab52 publishes their analysis and assessment of this alleged GRU related unit.
In addition to conventional PSYOP, unit 54777 includes both SIGINT and cyberspace capabilities. Related to SIGINT, unit 54777 gathers and analyzes communications to produce intelligence that can be used in further disinformation and influence campaigns. In the cyber arena, this unit works complementing Cyberspace Operations not only with digital PSYOP: its activities include operating in support of other GRU cyber units, creating and disseminating fake versions of their cyberspace operations, as well as operating on the tactical level by conducting electronic warfare and psychological operations.
https://lab52.io/blog/gru-military-unit-54777/
Reporting on China
Nothing of note this week.
Reporting on North Korea
Lazarus Group Targets Organizations with Sophisticated LinkedIn Recruiting Scam
Ionut Alexandru BALTARIU, Andrei ANTON-AANEI and Alina BÎZGĂ walks through the end of end of this alleged North Korean campaign. Ensuring your resilience is able to minimise impact in a world where this level of social engineering is a normal aspect of state and criminal tradecraft is likely a proactive step..
After receiving the requested information, the criminal shares a repository containing the "minimum viable product" (MVP) of the project. He also includes a document with questions that can only be answered by executing the demo.
Further Variants of DPRK Malware Family Unearthed
Phil Stokes & Tom Hegel detail an evolution in this alleged North Korean malware family. Noteworthy for me was the fact that Apple rolled out signatures to their on-device engine.
Last week Apple pushed a signature update to its on-device malware tool XProtect to block several variants of what it called the macOS Ferret family: FROSTYFERRET_UI, FRIENDLYFERRET_SECD, and MULTI_FROSTYFERRET_CMDCODES.
This DPRK-attributed malware family was first described by researchers in December and further in early January and identified as part of the North Korean Contagious Interview campaign, in which threat actors lure targets to install malware through the job interview process.
Analysis of malicious HWP cases of 'APT37' group distributed through K messenger
Genians details an evolution in alleged North Korean tradecraft. Noteworthy due to several factors. The first is distribution mechanism, second is regional file format use and third is the attempt to evade endpoint detection.
Identity theft and Korean APT attack conducted through K Messenger group chat room
After initial spear phishing penetration is successful, it is necessary to detect 'lateral movement' through the terminal.
Analysis of APT37 Group's Relentless Attack Tactics Using HWP, LNK Malware
Increase in Variant Attacks to Evade Anti-Virus Detection and Utilize Commercial Cloud C2
USA -vs-Approx 942,462.845 USDT
Interesting legal move here by the US Government to try and get back digital assets gained through the IT workers programme allegedly by North Korea.
Plaintiff, the United States of America, by and through the United States Attorney for the District of Columbia and the Assistant Attorney General for the National Security Division, brings this verified complaint for forfeiture in a civil action in rem against approximately 942,462.845 USDT, hereinafter the “Defendant Property,” and alleges as follows:
https://storage.courtlistener.com/recap/gov.uscourts.dcd.276610/gov.uscourts.dcd.276610.1.0.pdf
Reporting on Iran
Unmasking: Technological Advancement and Evolution of MuddyWater in 2024
Israeli National Cyber Directorate provides a valuable and comprehensive breakdown of an alleged Iranian group. From phishing for initial access to lateral movement it is all in here. We have covered aspects here previously, but a comprehensive aggregation is valuable.
This report provides an in-depth analysis of the activities of the Iranian cyberattack group MuddyWater within the Israeli cyber domain, focusing on their tactics, techniques, and procedures (TTPs), tools, and primary attack targets.
https://www.gov.il/BlobFolder/reports/maddy_water_2024/en/ALERT_CERT_IL_W_1858.pdf
Reporting on Other Actors
Infrastructure Laundering: Cloudy Behavior Around FUNNULL CDN Renting IPs from Big Tech
SilentPush alleged at scale use of hyper-scaler infrastructure for a malicious content delivery network.
Our research team was surprised to find mainstream cloud providers, such as Amazon Web Services (AWS)* and Microsoft Azure, are often seen in large-scale use by threat actors. While providers are consistently banning specific IP addresses used by the FUNNULL content delivery network (CDN), the pace is unfortunately not fast enough to keep up with processes being used to acquire the IPs.
FUNNULL has rented over 1,200 IPs from Amazon, and nearly 200 IPs from Microsoft – nearly all have been taken down as of this writing, but new IPs are continually being acquired every few weeks.
There are indications of FUNNULL illicitly acquiring the IPs using stolen or fraudulent accounts. However, external visibility into this process is limited.
Silent Push’s research into the FUNNULL CDN’s activities has revealed a direct association with money laundering as a service hosted on shell websites, retail phishing schemes, and pig-butchering scams being kept online via infrastructure laundering.
https://www.silentpush.com/blog/infrastructure-laundering/
Recent cases of watering hole attacks
Shusei Tomonaga gives a two part Asia perspective on this technique. This diagram shows the blend of techniques which have been employed by alleged Chinese, North Korean and other threat actors.
https://blog.apnic.net/2025/01/31/recent-cases-of-watering-hole-attacks-part-1/
https://blog.apnic.net/2025/01/31/recent-cases-of-watering-hole-attacks-part-2/
Discovery
How we find and understand the latent compromises within our environments.
Living Off The Tunnels
An assembled avengers provide this valuable resource which aggregates understanding to allow detection teams to go hunting. It’s wabbit season…
Living Off The Tunnels a.k.a LOTTunnels Project is community driven project to document digital tunnels that can be abused by threat actors as well by insiders for data exfiltrations, persistence, shell access etc.
Large Number of Files Downloaded From OneDrive or SharePoint
Security Aura releases this KQL which will help detection teams to identify potential data theft.
These queries returns events where a large number of files would have been downloaded from OneDrive or SharePoint.
LevelDB WAL log - extracting ChatGPT conversations
Ilya Kobzar documents where to go to get data to help in certain investigations…
The WAL log is written to disk after ChatGPT application (i.e. associated process tree) is terminated, which may happen either at system shutdown/reboot or if the user exits the application. The exact location of the binary: “%UserProfile%\AppData\Local\Packages\OpenAI.ChatGPT-Desktop_2p2nqsd0c76g0\LocalCache\Roaming\ChatGPT\IndexedDB\https_chatgpt.com_0.indexeddb.leveldb\######.log” (“000003.log” in my case).
www.ilyakobzar.com/p/leveldb-wal-log-extracting-chatgpt
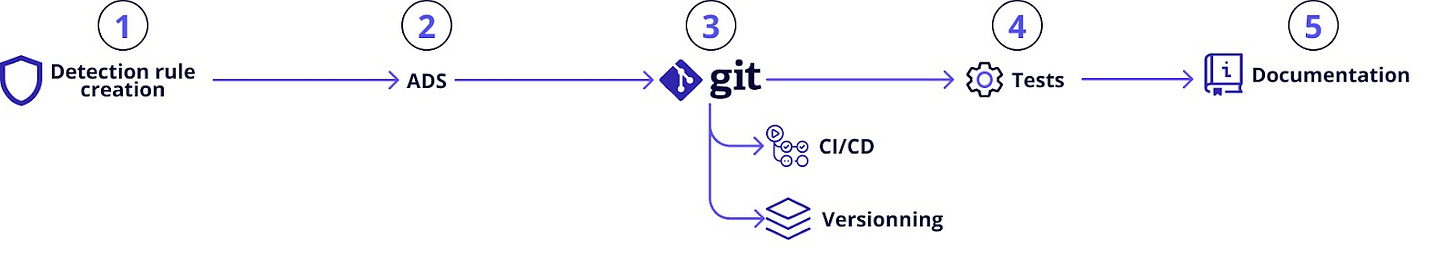
Detection engineering at scale: one step closer (part two)
Guillaume C and Erwan Chevalier provide some aspiration for many detection teams. This is how we win..
In this article, we will build upon the previous discussion of our detection approach and associated challenges by detailing the regular and automated actions implemented through our CI/CD pipelines.
https://blog.sekoia.io/detection-engineering-at-scale-one-step-closer-part-two/
Defence
How we proactively defend our environments.
Manage Dev Tunnels with Group Policies
Carolin Auribe shows how Microsoft have listened to the concerns given the misuse of this feature. If you do not need this capability you should consider this control (see above Living off the Tunnels).
We’ve heard from organizations that IT Administrators want to control certain aspects of Dev Tunnels to achieve consistency or compliance across their organization. In response to this feedback, we’re thrilled to announce that Dev Tunnels now supports this level of control with Group Policy Administrative Templates (ADMX/ADML files)!
Guidance and Strategies to Protect Network Edge Devices
Our friends at CISA pulls together the partners publications and co-sealing by NCSC UK, CCCS and ASD’s ACSC with co-sealing by NSA.
Security Considerations for Edge Devices, led by the Canadian Centre for Cyber Security (CCCS), a part of the Communications Security Establishment Canada, provides real-world edge device compromises, an overview of threats to these devices, mitigations for administrators to use to reduce risk of compromise, and recommendations for manufacturers to make their products secure by design.
Digital Forensics Monitoring Specifications for Products of Network Devices and Applications, led by the United Kingdom’s National Cyber Security Centre (NCSC-UK), highlights that necessary security logs, remote logging security and data collection features by default or that require no additional configuration enable network defenders to easily detect and investigate malicious activity following a cyber intrusion.
Mitigation Strategies for Edge Devices: Executive Guidance and Mitigation Strategies for Edge Devices: Practitioner Guidance, two separate guides led by the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), provide a summary of mitigation strategies and best practices on securing, hardening, and managing edge devices effectively, and technical details on seven mitigation strategies for operational, procurement and cybersecurity staff to implement to reduce risk to edge devices.
https://www.cisa.gov/resources-tools/resources/guidance-and-strategies-protect-network-edge-devices
Detecting High Risk Chrome Extensions with OSQuery
Sarah Zipkin gave us this in 2019 which is still relevant in 2025..
SELECT *
FROM chrome_extensions
WHERE chrome_extensions.uid IN (SELECT uid FROM users)
AND (permissions LIKE (‘%clipboardWrite%’)
OR permissions LIKE (‘%<all_urls>%’)
OR permissions LIKE (‘%tabs%’)
OR permissions LIKE (‘%cookies%’)
OR permissions like (‘%://*/%’))
https://medium.com/quiq-blog/detecting-high-risk-chrome-extensions-with-osquery-bca1a8856448
AiTM/ MFA phishing attacks in combination with “new” Microsoft protections (2025 edition)
Jeffery Appel shows how to leverage the features within the Microsoft eco-system to defend again AiTM and given these statistics I would encourage all organisations to read and deploy where appropriate.
Microsoft observed a 146% rise in adversary-in-the-middle (AiTM) attacks over the last year (2024), indicating that cybercriminals are continuing to find ways to compromise accounts that are protected by multifactor authentication (MFA).
Incident Writeups & Disclosures
How they got in and what they did.
Nothing overly of note this week
Vulnerability
Our attack surface.
Coordinated Vulnerability Disclosure
O-RAN alliance announces their coordinated vulnerability disclosure process..
O-RAN ALLIANCE (O-RAN) recognizes the value of a Coordinated Vulnerability Disclosure (CVD) process in improving the security of its specification and open source code based on O-RAN specifications.
AMD: Microcode Signature Verification Vulnerability
Google identifies a vulnerability which goes to the very heart of the root of trust. Where crypto vulnerabilities bite…
Google Security Team has identified a security vulnerability in some AMD Zen-based CPUs. This vulnerability allows an adversary with local administrator privileges (ring 0 from outside a VM) to load malicious microcode patches. We have demonstrated the ability to craft arbitrary malicious microcode patches on Zen 1 through Zen 4 CPUs. The vulnerability is that the CPU uses an insecure hash function in the signature validation for microcode updates. This vulnerability could be used by an adversary to compromise confidential computing workloads protected by the newest version of AMD Secure Encrypted Virtualization, SEV-SNP or to compromise Dynamic Root of Trust Measurement.
https://github.com/google/security-research/security/advisories/GHSA-4xq7-4mgh-gp6w
8 Million Requests Later, We Made The SolarWinds Supply Chain Attack Look Amateur
Benjamin Harris, Aliz Hammond and Pinaki Mondal bring their indomitable style to this vulnerability disclosure. NCSC UK helped with the disclosure process.
Highlights the complexity of distributed and SaaS like infrastructure when left dangling..
We've demonstrated an ability to compromise significantly sensitive networks, including governments, militaries, space agencies, cyber security companies, supply chains, software development systems and environments, and more.
Offense
Attack capability, techniques and trade-craft.
Happy Chinese New Year-D2 Release-A New Beginning
New C2 framework out of China..
This is a new beginning, D2 v0.1 bate. Good-looking and easy-to-use are the first principles of D2. I have basically reconstructed the UI. It should be the best-looking C2 on the market , no doubt about it. After more than 10 years of development, CobaltStrike still has many abandoned and basically unused functions, so D2 v0.1 is mainly streamlined .
Exploitation
What is being exploited..
CVE-2025-0411: Ukrainian Organizations Targeted in Zero-Day Campaign and Homoglyph Attacks
Peter Girnus details the timeline of this vulnerability..
September, 2024 the Trend Zero Day Initiative™ (ZDI) Threat Hunting team identified the exploitation of a 7-Zip zero-day vulnerability used in a SmokeLoader malware campaign targeting Ukrainian entities.
The vulnerability, CVE-2025-0411, was disclosed to 7-Zip creator Igor Pavlov, leading to the release of a patch in version 24.09 on November 30, 2024.
CVE-2025-0411 allows the bypassing of Windows Mark-of-the-Web protections by double archiving files, thus preventing necessary security checks and allowing the execution of malicious content.
The vulnerability was actively exploited by Russian cybercrime groups through spear-phishing campaigns, using homoglyph attacks to spoof document extensions and trick users and the Windows Operating System into executing malicious files.
The vulnerability was likely exploited as a cyberespionage campaign against Ukrainian government and civilian organizations as part of the ongoing Russo-Ukraine conflict.
We provide recommendations for organizations to proactively secure their systems. This includes updating 7-Zip to at least version 24.09, implementing strict email security measures, and conducting employee training on phishing (including homoglyph attacks).
https://www.trendmicro.com/en_us/research/25/a/cve-2025-0411-ukrainian-organizations-targeted.html
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
vminer
Thalium gives a hypervisor agnostic approach to VM introspection..
Vminer is a VMI (Virtual Machine Introspection) tool, which means that it can retrieve data from a virtual machine without the help of a guest tool. Because it does not need executing data on the host, it can also work with a memory dump.
Support multiple guest OS and architectures (see section below)
Independent of a specific backend (hypervisor, dump format, etc)
Automatic detection of kernel page directory and ASLR
Getting common OS information (running processes, memory areas, PIDs, etc)
Getting backtrace/callstack of processes
Automatic download of debug information (Windows guests only)
Software address translation on Windows guests
https://github.com/thalium/vminer
Lifting Binaries, Part 0: Devirtualizing VMProtect and Themida: It's Just Flattening?
Naci shows what one human and desire can achieve still in reverse engineering..
why I developed Mergen rather than focusing on the more technical aspects.
..
Commercial VM based obfuscators like VMProtect and Themida are considered as industry standards because of their black box implementation. Even though these solutions have been in this position for a long time and there are public projects that are able to deobfuscate a particular solution or a particular version of a solution, there are (or were) no public projects that can deobfuscate multiple versions or multiple solutions.
https://nac-l.github.io/2025/01/25/lifting_0.html
https://github.com/NaC-L/Mergen
Debugging SMM with JTAG: Part 2
Alan Sguigna walks through some very low level approaches which will open up various attack surfaces previously not explorable.
Being able to debug SMM with run-control is very powerful. Run-control means you can halt the target, set breakpoints, single-step through code, etc. But run-control stops the target at a moment in time, allows inspection of its state, and enables you to move forward in time to see what happens. But it doesn’t tell you what happened prior to the initial target halt.
Modern Intel CPUs have several very advanced inherent trace capabilities, including Last Branch Record (LBR), Intel Processor Trace (Intel PT), Architectural Event Trace (AET), and others. Within SMM, given that it has its own separate memory space, Intel PT and AET do not work. Trying to use them will crash the target, and you’ll have to power cycle it.
https://www.asset-intertech.com/resources/blog/2025/02/debugging-smm-with-jtag-part-2/
Investigating Kernel Mode Shadow Stacks on Windows
Connor McGarr walks through how shadow stacks work in practice in Windows. A really wonderful writeup..
Intel CET technically refers to multiple features, including both Indirect Branch Tracking (IBT) and Shadow-Stack. Windows does not implement IBT (and instead leverages the existing Control Flow Guard feature). Because of this, any references to Intel CET in this blog post really refer specifically to the shadow stack feature.
https://connormcgarr.github.io/km-shadow-stacks/
Reverse Engineering Call Of Duty Anti-Cheat
ssno reminds us that everything we do in cyber security that low-level games hackers/protectors did first..
Arxan is an obfuscation/protection tool that’s used on many Call of Duty games, most of which are anything past Black Ops 3. Which includes many features, that make cheaters/reverse engineers’ life a lot harder.
Runtime Executable Decryption
Executable Checksums
Jmp Obfuscation
Entrypoint Obfuscation
Pointer Encryption
https://ssno.cc/posts/reversing-tac-1-4-2025/
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Nothing of note this week
The Cyber Sessions by NHS England Transformation - podcast series
SoftBank Corp. and Quantinuum Announce Groundbreaking Partnership Toward Practical Application of Quantum Computing - “the hybrid approach that combines Central Processing Units (CPUs), Graphics Processing Units (GPUs), and Quantum Processing Units (QPUs) holds the potential to further extend the capabilities of AI.”
TikTok's recommendations skewed towards Republican content during the 2024 U.S. presidential race
Scaling Our Rate Limits to Prepare for a Billion Active Certificates - Let’s Encrypt
Artificial intelligence
Books
Events
Nothing of note this week
Video of the week (in German) - Kim's Cyber Army: How North Korea Infiltrates German Companies (English autogenerated translation available)
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.