CTO at NCSC Summary: week ending July 21st
What should transparency look like in our software and hardware eco-systems?
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note beyond the CrowdStrike update which caused global impact, but wasn’t a cyber incident. Organisations should follow CrowdStrike’s recovery advice and engage local IT services companies if they need help with remediation. At NCSC UK we released a note.
In the high-level this week:
Cyber Essentials 'Pathways': From experiment to proof of concept - NCSC engages - “We are encouraging large organisations to help us develop an alternative route to certification.”
Recent Cyber Attacks on US Infrastructure Underscore Vulnerability of Critical US Systems, November 2023–April 2024 (Released June) - US Office of the Director of National Intelligence analyses and assesses - “Iran-affiliated and pro-Russia cyber actors gained access to and in some cases have manipulated critical US industrial control systems (ICS) in the food and agriculture, healthcare, and water and wastewater sectors in late 2023 and 2024.”
Communications Security Establishment Annual Report 2023-2024 - CSE/Canadian Government releases - “In early 2023, CSE’s foreign intelligence allowed the Cyber Centre to respond to a cyber incident that could have caused serious damage to property and life. The intelligence discovered that a state-aligned actor had directed a cyber attack against Canadian CI to disrupt its operation and risk grave injury”
London Borough of Hackney reprimanded following cyber-attack - UK Information Commissioners Office reprimands - “Whilst nefarious actors may always exist, the council failed to effectively implement sufficient measures that could have better protected their systems and data from cyber-attacks.”
A summary of the Japanese government's public attribution of cyber attacks - Piyolog analyses:
The Japanese government has conducted seven public attributions from 2017 to July 2024. Of the seven cases, five were from China and two from North Korea.
There are various forms of announcements, such as foreign ministry spokesperson statements, warnings, and joint signatures, and the expressions used to describe the targets of announcements are often different, although it is unclear whether they are used intentionally. ("based," "with background," "background," "said to be a subordinate organization," etc.) The government organizations that issued these statements are the Ministry of Foreign Affairs, the National Police Agency, the Cabinet Secretariat's Cybersecurity Center, and the Financial Services Agency.
There has only been one case in which publication was made with content and timing unique to Japan. Initially, publication was made after the issuance of a statement by the relevant country, etc., but in 2023 and 2024, publications have been made jointly with the relevant countries.
Guard members, international partners train on cyber skills in Slovenia - US Army reports - “More than 140 National Guard members from six states are working alongside international partners in a cyber training exercise designed to expand interoperability along with tracking and elimination of cyber threats.”
DISA eyes ‘aggressive’ goal of automating 75 percent of cyber capabilities - Breaking Defence reports - “As DISA prepares for the looming threat of China, the agency set an ambitious goal of having 75 percent of its administrative-like cybersecurity capabilities completely automated by artificial intelligence, Brian Hermann, cybersecurity and analytics director at DISA [said]”
EuRepoC Cyber Conflict Briefing – May 2024 (released July) - European Repository Cyber Incidents reports - “In May 2024, EuRepoC documented 73 cyber operations, representing a 21.5% decrease compared to the previous month. This figure is four incidents higher than the overall average in recorded activity of 69 operations per month.”
Advancing Accountability in Cyberspace - Models, Mechanisms, and Multistakeholder Approaches Findings from a two-year research project on improving international cyber accountability and deterring malicious cyber behavior - Stimson Center researches -”We find that as with other domains, the unique attributes of cyberspace need not preclude it from oversight, guardrails, and accountability. With political will and an inclusive approach there is a whole menu of options, ranging from formal agreements and to less formal practices and incentive frameworks; all of which can drive accountability and promote responsible behavior in cyberspace.”
The geopolitics of technology standards: historical context for US, EU and Chinese approaches - International Affairs paper - “Our historical review shows that, while the three polities have different priorities and face distinct challenges, they all seem to converge towards a greater role for governments in standard-setting.”
The risks of a last-minute Cybercrime Treaty Protocol - Global Initiative opines - “Settling the primary scope of the convention is crucial before considering additional protocols. This approach would ensure a more stable and focused foundation for addressing cybercrime on an international scale. Moreover, the brief suggests that any future protocols should be evaluated for their potential added value and their alignment with the core objectives of the main convention. “
Reporting on/from China
Secretive China Agency Backtracks on Aggressive Policies After $1 Trillion Rout - Bloomberg reports - “The government is walking the highwire in balancing security and development,” said Angela Zhang, a China tech law expert and author of High Wire: How China Regulates Big Tech and Governs Its Economy. “To stimulate the economy and boost employment, Chinese regulators have lifted many restrictions and relaxed control. The CAC is no exception.”
CodeFuse-13B: Pre-trained multi-language code large model - Di Peng reports - “CodeFuse is Ant Group's self-developed code generation model, which can provide intelligent suggestions and real-time support to help developers automatically generate code, comments, test cases, etc., improving research and development efficiency. The CodeFuse project started in early 2023 and has currently released a series of 15 models, 4 data sets, and several related tool chains.”
Artificial intelligence
Introducing the Coalition for Secure AI, an OASIS Open Project - OASIS press-releases - a group established to try and likely try avoid or delay regulation - “To start, CoSAI will form three workstreams, with plans to add more over time:
Software supply chain security for AI systems: enhancing composition and provenance tracking to secure AI applications.
Preparing defenders for a changing cybersecurity landscape: addressing investments and integration challenges in AI and classical systems.
AI security governance: developing best practices and risk assessment frameworks for AI security.”
Generative AI in Cybersecurity - Assessing impact on current and future malicious software - Centre for Emerging Technology and Security explores - ”This CETaS Briefing Paper explores the potential of generative artificial intelligence (GenAI) in creating malicious software and is aimed at informing risk management and supporting the AI-cybersecurity evaluation community. The cybersecurity field is divided, with some fearing GenAI could lead to novel threats while others believe it merely automates existing malicious code.”
Fully autonomous GPT-4 AI agents use Zero Days to successfully hack systems - a futurists view
then some evidence from a company trying to achieve this in practice who had some success in CTF like environments - but as a reminder from last week Project Naptime: Evaluating Offensive Security Capabilities of Large Language Models - “there's a large difference between solving isolated CTF-style challenges without ambiguity (there's always a bug, you always reach it by providing command line input, etc.) and performing autonomous offensive security research.”
Goldman Sachs: AI Is Overhyped, Wildly Expensive, and Unreliable - 404 Media reports - “Despite these concerns and constraints, we still see room for the AI theme to run, either because AI starts to deliver on its promise, or because bubbles take a long time to burst,”
Universities Don’t Want AI Research to Leave Them Behind - Wall Street Journal reports - “Universities are in a race for relevance in the field of generative AI as private companies, loaded with talent and pricey chips, drive the conversation. Outspent by Silicon Valley, some are turning their research focus to less computing-power-intensive areas of artificial intelligence, even as they seek to build additional computing resources capable of powering bigger models.”
Japan's AI unicorn to use Samsung's 2-nm chip production tech - Nikkei Asia reports - “The founding members have been designing their own chip since 2016. The company aims to slash "unnecessary" capabilities from processor designs in order to increase efficiency compared with graphic processing units, or GPUs, the technology championed by Nvidia of the U.S. More efficiency means less energy consumption for the same amount of computing power.”
U.S. chip designer aims to bring down AI prices pushed up by Nvidia - Nikkei Asia reports - “Tenstorrent, founded in 2016, is preparing to sell its second-generation multipurpose AI chip at the end of this year. The company says that in some areas it boasts better energy and processing efficiency than Nvidia's AI GPUs. Its Galaxy systems are three times more efficient and 33% cheaper than Nvidia's DGX”
Cyber proliferation
Apple Issues New Spyware Attack Warning To iPhone Users - Forbes reports - “Apple detected that you are being targeted by a mercenary spyware attack that is trying to remotely compromise the iPhone associated with your Apple ID -xxx-,” Apple wrote in its new spyware alert."
Bounty Hunting
Rule of Law In Cyberspace: Philippines Indicts Two Cyber Thieves - DoJ Philippines
Hacker jailed for creating malware that targeted Braintree site - BBC reports - jailed for 21 months.
Treasury Sanctions Leader and Primary Member of the Cyber Army of Russia Reborn - US Department of the Treasury sanctions - “the United States designated Yuliya Vladimirovna Pankratova (Pankratova) and Denis Olegovich Degtyarenko (Degtyarenko), two members of the Russian hacktivist group Cyber Army of Russia Reborn (CARR) for their roles in cyber operations against U.S. critical infrastructure. These two individuals are the group’s leader and a primary hacker, respectively.”
Reflections this week are around transparency in software and hardware eco-systems. But first why does transparency matter?
Simply put information asymmetry exists between technology producers and consumers. This asymmetry leads to various adverse outcomes and especially so in cyber security.
By way of example when we think about SBOMs (Software Bill of Materials) today they deal with third party but not first party code. So whilst a vendor may patch all their vulnerable third party libraries you don’t have insight into the fact that the first party code may be written in a memory unsafe language and that the codebase is in part 20 years old and 80% not touched in a decade.
By way of another example when we think about HBOMs (Hardware Bill of Materials) today they at best go to component level. But what about sub component in say a system-on-chip which might actually be a package of multiple sub components with intellectual property from various companies?
The rabbit holes are indeed deep..
Anyway the reflection this week is what is the level of transparency we need and want for better security outcomes? Transparency might be around the technology itself (what it is comprised of, technologies used and code churn ratios/age etc.) but also vulnerabilities patched as well as security roadmaps etc.
It starts with BOMs but likely doesn’t end with BOMs…
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
UAC-0180 Targeted Cyber Attacks Against Defense Enterprises Using GLUEEGG / DROPCLUE / ATERA
The Government Computer Emergency Response Team of Ukraine CERT-UA releases this alert on an alleged Russia sourced operation. The tradecraft chain is long i.e. email → .zip → pdf → [download file] → 🦠
[We] received information regarding the distribution of e-mails among Ukrainian defense enterprises on the topic of the purchase of UAVs and an attachment in the form of a ZIP file containing a PDF document with a link.
If the link is followed, the file "adobe_acrobat_fonts_pack.exe" classified as GLUEEGG malware, developed using the Go programming language, will be downloaded to the victim's PC. The main purpose of GLUEEGG is to decrypt (XOR with a 128-byte key) and run the DROPCLUE loader, developed using the Lua programming language.
https://cert.gov.ua/article/6280099
Reporting on China
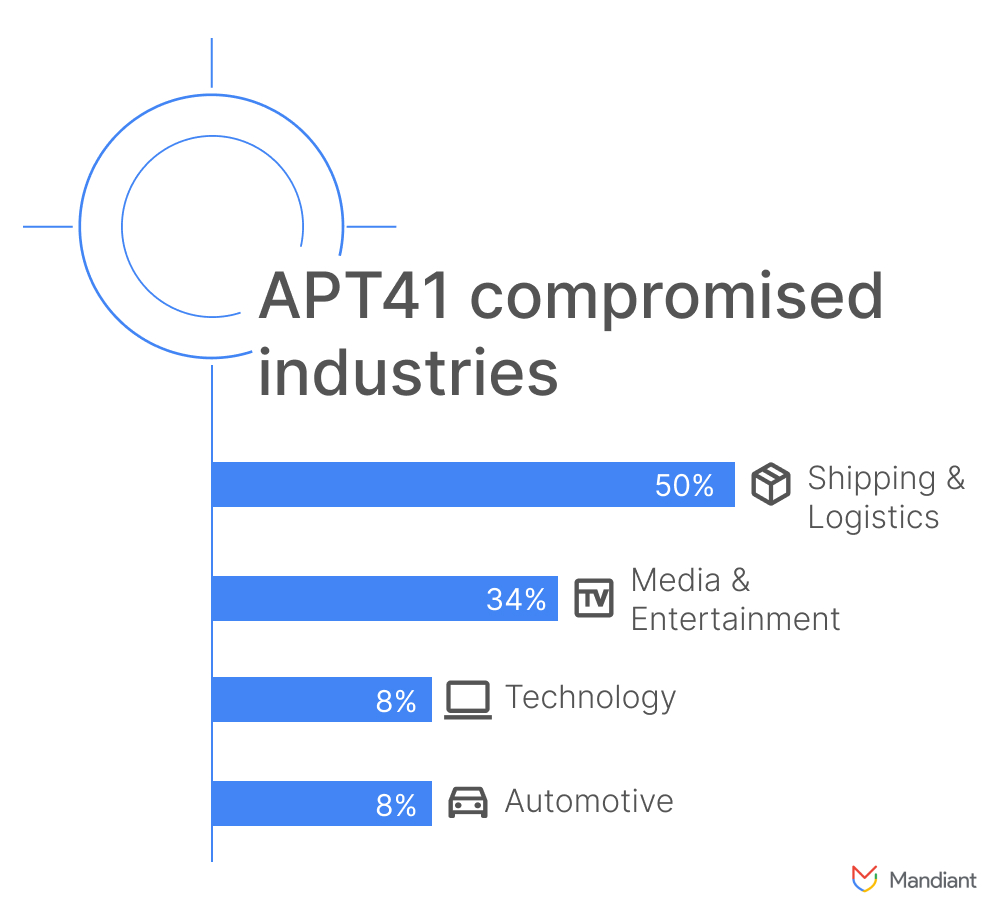
APT41 Has Arisen From the DUST
Mike Stokkel, Pierre Gerlings, Renato Fontana, Luis Rocha, Jared Wilson, Stephen Eckels and Jonathan Lepore detail this alleged Chinese operation. WebShells and droppers among other things. Note a degree of attempting to evade detection..
In collaboration with Google’s Threat Analysis Group (TAG), Mandiant has observed a sustained campaign by the advanced persistent threat group APT41 targeting and successfully compromising multiple organizations operating within the global shipping and logistics, media and entertainment, technology, and automotive sectors. The majority of organizations were operating in Italy, Spain, Taiwan, Thailand, Turkey, and the United Kingdom.
APT41 successfully infiltrated and maintained prolonged, unauthorized access to numerous victims' networks since 2023, enabling them to extract sensitive data over an extended period.
APT41 used a combination of ANTSWORD and BLUEBEAM web shells for the execution of DUSTPAN to execute BEACON backdoor for command-and-control communication. Later in the intrusion, APT41 leveraged DUSTTRAP, which would lead to hands-on keyboard activity. APT41 used publicly available tools SQLULDR2 for copying data from databases and PINEGROVE to exfiltrate data to Microsoft OneDrive.
https://cloud.google.com/blog/topics/threat-intelligence/apt41-arisen-from-dust/
The Return of Ghost Emperor’s Demodex
Dor Nizar details an alleged Chinese-nexus threat group which is noteworthy and complex.. noteworthy and complex..
In late 2023, Sygnia’s Incident Response team was engaged by a client whose network was compromised and was leveraged to penetrate one of its business partner’s network.
During the investigation, several servers, workstations, and users were found to be compromised by a threat actor who deployed various tools to communicate with a set of C2 servers.
One of these tools was identified as a variant of Demodex, a rootkit previously associated with the threat group known as GhostEmperor.
GhostEmperor is a sophisticated China-nexus threat group known to target mostly South-East Asian telecommunication and government entities, first disclosed by Kaspersky in a blog published in September 2021.
GhostEmperor employs a multi-stage malware to achieve stealth execution and persistence and utilizes several methods to impede analysis process.
Usually, once the threat group gains initial access to the victim’s network by using vulnerabilities such as ProxyLogon, a batch file is executed to initiate the infection chain.
In this blog we describe a new infection chain deployed by GhostEmperor, which includes several loading schemes and various obfuscation techniques utilized by the threat group.
https://www.sygnia.co/blog/ghost-emperor-demodex-rootkit/
Italian government agencies and companies in the target of a Chinese APT
TG Soft reports this alleged Chinese campaign which interestingly uses installations instructions in a Word document as the lure to get the user to deploy the remote access trojan. Social engineering++..
On June 24 and July 2, 2024, two targeted attacks on Italian companies and government entities were observed by a Chinese cyber actor exploiting a variant of the Rat 9002 in diskless mode. Other variants have over time been named as Rat 3102. These activities are associated with the APT17 group also known as "DeputyDog".
The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link.
Both campaigns invited the victim to install a Skype for Business package from a link of an Italian government-like domain to convey a variant of Rat 9002.
Rat 9002 and Rat 3102 are notoriously linked to APT17, a Chinese cyber-criminal group known for:
Operation Aurora (attributed to the Chinese government)
Operation Ephemeral Hydra
targeted attacks on companies and government entities
https://www.tgsoft.it/news/news_archivio.asp?id=1557&lang=eng
Reporting on North Korea
BeaverTail
Patrick Wardle documents a malicious macOS .dmg file which is trojanized meeting app. Allegedly an DPRK opereation which looks to involve social engineering in part to laydown on targets.
A new (now native) variant of the
DPRKmalware known asBeaverTail.Masquerading as
MiroTalk, this variant, (like the other non-native variants) steals information from victims machines as well as download and executes additional Python-based payloads such asInvisibleFerret.
https://objective-see.org/blog/blog_0x7A.html
Case related to employment applications.docx.lnk
Wezard4U details a .lnk file which leads to PowerShell which is allegedly North Korean in origination.
https://wezard4u.tistory.com/429233
Reporting on Iran
New BugSleep Backdoor Deployed in Recent MuddyWater Campaigns
CheckPoint details an alleged Iranian operation which resulted in a new implant. If nothing else it shows they continue to evolve and invest in an attempt to likely avoid detection.
MuddyWater, an Iranian threat group affiliated with the Ministry of Intelligence and Security (MOIS), has significantly increased its activities in Israel since the beginning of the Israel-Hamas war in October 2023. This parallels with activities against targets in Saudi Arabia, Turkey, Azerbaijan, India and Portugal.
The threat actors consistently use phishing campaigns sent from compromised organizational email accounts. The phishing campaigns typically lead to the deployment of legitimate Remote Management Tools (RMM) such as Atera Agent and Screen Connect.
Recently, Muddy Water campaigns also led to the deployment of a new, previously undocumented tailor-made backdoor we dubbed BugSleep, that is used to target organizations in Israel.
BugSleep is a backdoor designed to execute the threat actors’ commands and transfer files between the compromised machine and the C&C server. The backdoor is currently in development, with the threat actors continuously improving its functionality and addressing bugs.
https://research.checkpoint.com/2024/new-bugsleep-backdoor-deployed-in-recent-muddywater-campaigns/
Further related reporting
https://blog.sekoia.io/muddywater-replaces-atera-by-custom-muddyrot-implant-in-a-recent-campaign/
Reporting on Other Actors
TAG-100 Uses Open-Source Tools in Suspected Global Espionage Campaign, Compromising Two Asia-Pacific Intergovernmental Bodies
Recorded Future details an unattributed threat actor who is doing some wide targeting. Note they were quick off the mark on exploitation on an edge security device vulnerability.
TAG-100 has likely compromised organizations in at least ten countries in Africa, Asia, North America, South America, and Oceania and, following initial access, employed the open-source Go backdoors Pantegana and SparkRAT.
TAG-100 has also conducted probable reconnaissance and exploitation activity targeting the internet-facing appliances of additional organizations in at least fifteen countries in North America, Europe, and Asia.
Based on the identified TAG-100 targeted and victim hosts, it is likely that the group has exploited a range of internet-facing products, including Citrix NetScaler ADC and Gateway appliances, F5 BIG-IP, Zimbra Collaboration Suite, Microsoft Exchange, SonicWall, Cisco Adaptive Security Appliances (ASA), Palo Alto Networks GlobalProtect, and Fortinet FortiGate.
In the immediate aftermath of releasing a PoC exploit for Palo Alto Networks GlobalProtect firewall vulnerability CVE-2024-3400, TAG-100 conducted probable reconnaissance and attempted exploitation against dozens of US-based organizations running these devices.
The widespread targeting of internet-facing appliances is particularly attractive because it offers a foothold within the targeted network via products that often have limited visibility, logging capabilities, and support for traditional security solutions, reducing the risk of detection post-exploitation.
While Insikt Group cannot attribute TAG-100 activity based on current evidence, the group’s consistent targeting of intergovernmental, diplomatic, and religious organizations aligns with a suspected espionage motive. Additionally, several targets of this activity align with historical targeting from Chinese state-sponsored groups, including Asia-Pacific intergovernmental and diplomatic entities, religious organizations in the United States and Taiwan, and a political party that has supported an investigation into the treatment of the Uyghur people by the Chinese government. Despite this, TAG-100’s use of open-source tooling coupled with the group’s pattern of life, targeting, and broader tactics, techniques, and procedures (TTPs) provide some conflicting evidence, leading us to continue investigating potential attribution for this activity.
https://go.recordedfuture.com/hubfs/reports/cta-2024-0716.pdf
R0BL0CH0N TDS: A deep dive into the infrastructure of an affiliate marketing scam
Simon Vernin details an alleged criminal operation and underlying infrastructure used to distribute among other things malicious code. The scale of the impacted user base is of note here..
Affiliate marketing is a marketing strategy in which businesses reward affiliates for driving traffic or sales to their website. While being a legitimate and widely used marketing technique to boost traffic and sales for a product or service, affiliate marketing is also used in numerous malicious schemes promoting sweepstakes, home improvement services, casinos, or dating sites.
Hundreds of small affiliate networks promote primarily dubious affiliation offers that lead to well-known scams.
Affiliates are specialists in traffic generation and use their skills to distribute various types of content, ranging from legal advertising to direct malware distribution.
The World Watch team has identified a previously undocumented Traffic Distribution System (TDS) linked to affiliate marketing being used in scams that impacted around 110 million of Internet users. We have named it R0bl0ch0n TDS based on specific patterns in the URL redirections: "0/0/0".
This TDS infrastructure consists of numerous domains and dedicated servers protected behind Cloudflare. Even if the threat actor includes legitimate features such as unsubscribe and contact forms, steps are taken to hide the real entity behind these campaigns.
FIN7 Reboot | Cybercrime Gang Enhances Ops with New EDR Bypasses and Automated Attacks
Antonio Cocomazzi details an alleged criminal operation by an older group which is noteworthy due to the attempt to disable cyber security products.
New evidence shows FIN7 is using multiple pseudonyms to mask the group’s true identity and sustain its criminal operations in the underground market
FIN7’s campaigns demonstrate the group’s adoption of automated SQL injection attacks for exploiting public-facing applications
AvNeutralizer (aka AuKill), a highly specialized tool developed by FIN7 to tamper with security solutions, has been marketed in the criminal underground and used by multiple ransomware groups
SentinelLabs has discovered a new version of AvNeutralizer that utilizes a technique previously unseen in the wild to tamper with security solutions, leveraging the Windows built-in driver ProcLaunchMon.sys (TTD Monitor Driver)
Attribution efforts have expanded our understanding of the AvNeutralizer malware family. This research offers a broader perspective than previous research, enabling better evolution tracking and retrospective analysis
Fake Microsoft Teams for Mac delivers Atomic Stealer
Jérôme Segura highlights once more the risk posted by malvertising.. Noteworthy due to macOS targeting..
Based on our tracking, Microsoft Teams is once again a popular keyword threat actors are bidding on, and it is the first time we have seen it used by Atomic Stealer. Communication tools like Zoom, Webex or Slack have been historically coveted by criminals who package them as fake installers laced with malware.
This latest malvertising campaign was running for at least a few days and used advanced filtering techniques that made it harder to detect. Once we were able to reproduce a full malware delivery chain, we immediately reported the ad to Google.
Discovery
How we find and understand the latent compromises within our environments.
Detecting manually mapped [Windows] drivers
Samuel Tulach discusses how to detect manually mapped Windows driver in the anti-cheat context but will have value in the cyber defence/discovery context.
I am writing this article because there are still some people who believe they can just map their driver, swap some random pointer, and they are good to go. This is not true with practically any modern anticheat. As you could see in the example above, even I could, in a few hours, figure out how to (somewhat) reliably detect the presence of those drivers
https://tulach.cc/detecting-manually-mapped-drivers/
The Art of Malware C2 Scanning
This talk/slides by Takahiro Haruyama show how to reverse and emulate a protocol obfuscated by the compiler specifically for PlugX.
Rosetta: TLS traffic classification in diverse network environments
Interesting from China in this 2023 research from a Chinese university.
This article introduces an article from USENIX Security '23 "Rosetta: Enabling Robust TLS Encrypted Traffic Classification in Diverse Network Environments with TCP-Aware Traffic Augmentation" [1], which solves the problem of environmental changes when the existing deep learning model performs TLS encrypted traffic. The problem of model failure. It uses TCP-aware traffic enhancement mechanism and self-supervised learning to understand the implicit TCP semantics, thereby extracting robust features of TLS flows, and ultimately can achieve similar traffic classification effects in different network environments.
Original paper/slides/video
https://www.usenix.org/conference/usenixsecurity23/presentation/xie
Defence
How we proactively defend our environments.
Private Browsing 2.0
Apple’s approach to the future.
These are the protections and defenses added to Private Browsing in Safari 17.0:
Link Tracking Protection
Blocking network loads of known trackers, including CNAME-cloaked known trackers
Advanced Fingerprinting Protection
Extensions with website or history access are off by default
In addition, we added these protections and defenses in all browsing modes:
Capped lifetime of cookies set in responses from cloaked third-party IP addresses
Partitioned SessionStorage
Partitioned blob URLs (starting in Safari 17.2)
We also expanded Web AdAttributionKit (formerly Private Click Measurement) as a replacement for tracking parameters in URL to help developers understand the performance of their marketing campaigns even under Private Browsing.
https://webkit.org/blog/15697/private-browsing-2-0/
Attacking Connection Tracking Frameworks as used by Virtual Private Networks
Benjamin Mixon-Baca, Jeffrey Knockel, Diwen Xue, Tarun Ayyagari, Deepak Kapur, Roya Ensafi and Jedidiah R. Crandall show their work from the Privacy Enhancing Technologies Symposium. Noteworthy that commercial VPNs may not actually help..
In this paper, we examine the connection tracking frameworks used in common operating systems, identifying a novel exploit primitive that we refer to as the port shadow. We use the port shadow to build four attacks against VPNs that allow an attacker to intercept and redirect encrypted traffic, de-anonymize a VPN peer, or even portscan a VPN peer behind the VPN server. We build a formal model of modern connection tracking frameworks and identify that the root cause of the port shadow lies in five shared, limited resources. Through bounded model checking, we propose and verify six mitigations in terms of enforcing process isolation
https://petsymposium.org/popets/2024/popets-2024-0070.pdf
Securing The Chink in Kerberos’ Armor, FAST! Understanding The Need For Kerberos Armoring
A practical guide on how to secure Kerberos but also shows how it isn’t default and has some various requirements.
To use Kerberos Armoring, all domain controllers in the domain must be running Windows Server 2012 or higher, the Domain Functional Level (DFL) needs to be Windows Server 2012 or higher, and client devices need to run Windows 8 or higher. Keep in mind that implementing Kerberos Armoring should be done methodically and with a plan:
Ensure that Kerberos Armoring is enabled for clients first. This should also usually done in groups so that that further testing can be done (incase something breaks). This change needs to be applied to all clients before being configured on Domain Controllers.
Once Armoring is supported on domain clients, configure Kerberos Armoring on Domain Controllers. It is good practice to initially configure Domain Controllers to “Supported”. This will allow for armoring to be used when available, but not fail authentication if armoring is not available.
Clients that authenticate to Domain Controllers without using Kerberos Armoring will trigger Event ID: 4771 - Kerberos Pre-Authentication Failed. This log will include Failure Code: 0x19 - "Additional pre-authentication required." This indicates that the KDC required Kerberos armoring (FAST), but the client did not use it or did not support it.
Kerberos Armoring can be easily deployed using Group Policy.
Unauthenticated SSRF on Havoc C2 teamserver via spoofed demon agent
Evan Ikeda gives the world a capability which is not legal to use for most in practice..
I was able to discover a vulnerability in which unauthenticated attackers could create a TCP socket on the teamserver with an arbitrary IP/port, and read and write traffic through the socket. By exploiting this vulnerability, attackers could leak the origin IP of a teamserver behind public redirectors (attribution), abuse vulnerable teamservers as a redirector (misattribution) and route traffic through any listening socks proxies on the teamserver.
https://blog.chebuya.com/posts/server-side-request-forgery-on-havoc-c2/
Incident Writeups & Disclosures
How they got in and what they did.
A Squarespace Retrospective, or How to Coordinate an Industry-Wide Incident Response
Samczsun, Tayvano and Andrew Mohawk details an interesting impact where a migration apparently between companies led to increased exposure which was seized upon by threat actors.
Over the course of several days, an unknown threat actor exploited a vulnerability in Squarespace to take over accounts which controlled domains that had been recently migrated as part of the Squarespace acquisition of Google Domains. Using this access, the threat actor was able to redirect users to phishing sites, intercept emails, and hijack control of Google Workspace (formerly GSuite) tenants to read email and add devices.
Vulnerability
Our attack surface.
SonicWall SMA100 Stored XSS to RCE
There are pre-auth stored XSS and post-auth remote command injection vulnerabilities in SonicWall SMA100. These vulnerabilities allow unauthenticated attackers to execute arbitrary command when an authenticated user is exposed to the stored XSS.
The vulnerabilities were silently patched without any CVE assignment. The whole feature named Classic mode, where stored XSS vulnerability exists, was removed, and a new user input filtering code was added against command injection vulnerability.
https://ssd-disclosure.com/ssd-advisory-sonicwall-sma100-stored-xss-to-rce/
Cisco Smart Software Manager On-Prem Password Change Vulnerability
A vulnerability in the authentication system of Cisco Smart Software Manager On-Prem (SSM On-Prem) could allow an unauthenticated, remote attacker to change the password of any user, including administrative users.
Cisco Secure Email Gateway Arbitrary File Write Vulnerability
A vulnerability in the content scanning and message filtering features of Cisco Secure Email Gateway could allow an unauthenticated, remote attacker to overwrite arbitrary files on the underlying operating system.
Linux Kernel: Vulnerability in the eBPF verifier register limit tracking
A bug in the verifier’s register limit tracking was found .. that allows an attacker to trick the eBPF verifier into thinking a register has a value different from the one it takes when executing the program.
Using this bug, an LPE exploit was written allowing the attacker to gain an arbitrary kernel memory R/W primitive that can then be used to gain a full system compromise.
https://github.com/google/security-research/security/advisories/GHSA-hfqc-63c7-rj9f
Offense
Attack capability, techniques and trade-craft.
PwnedBoot
Samuel Tulach details a capability which we an expect to be patched, but interesting..
The Windows bootloader (
winload.efi) does not check the code signature or integrity of themcupdate_<platform>.dllfile when starting the system if the 'Disable Driver Signature Enforcement' option is selected. The file is loaded very early in the boot stage, and its entry point is executed from within the bootloader before a call toExitBootServices(), which means that you can just restore the context and return back to the firmware. The plot twist is thatmcupdate_<platform>.dllit not inside a valid memory mapping in the firmware context, so this project just remaps itself over the bootloader.
https://github.com/SamuelTulach/PwnedBoot
Process Injection is Dead. Long Live IHxHelpPaneServer
Michael Zhmailo provides code to a capability which may trip up some endpoint solutions.
POC to execute arbitrary code on behalf of another user.
As a COM object for testing I propose to take an object that implements the IHxHelpPaneServer interface, it was discovered by James Forshaw in 2016. This interface is useful because it provides an Execute method that allows arbitrary files to be executed on the system. Accordingly, by calling this method from another session, we can execute files on behalf of another user.
https://cicada-8.medium.com/process-injection-is-dead-long-live-ihxhelppaneserver-af8f20431b5d
https://github.com/CICADA8-Research/IHxExec
Attacking Primary Refresh Tokens using their MacOS implementation
Olaf Hartong and Dirk-jan Mollema show once more than attacks will often understand a system in totality better than those that built in and in doing so hit paydirt.
This research led to uncover an undocumented API that allows to request a deviceless PRT via a newer version of the protocol. This API also allows a workflow that enables us to recant a device claim or generate a new PRT without one based on an SSO-flow.
With this new token we can then register our own device in AAD and thereby bypass most conditional access policies.
https://troopers.de/troopers24/talks/3vlccy/
Exploitation
What is being exploited.
Nothing this week of note..
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Learning Program Behavioral Models from Synthesized Input-Output Pairs
Tural Mammadov, Dietrich Klakow, Alexander Koller and Andreas Zeller show the way of the future which will have numerous cyber security benefits when harnessed.
We introduce Modelizer - a novel framework that, given a black-box program, learns a model from its input/output behavior using neural machine translation.
The resulting model mocks the original program: Given an input, the model predicts the output that would have been produced by the program. However, the model is also reversible - that is, the model can predict the input that would have produced a given output. Finally, the model is _differentiable_ and can be efficiently restricted to predict only a certain aspect of the program behavior.
Modelizer uses grammars to synthesize inputs and to parse the resulting outputs, allowing it to learn sequence-to-sequence associations between token streams. Other than input and output grammars, Modelizer only requires the ability to execute the program.
https://arxiv.org/abs/2407.08597
Look Ma, No Input Samples! Mining Input Grammars from Code with Symbolic Parsing
Leon Bettscheider and Andreas Zeller provide a capability that when implemented will no doubt revolutionize parts of fuzzing as it doesn’t rely on underlying input corpus and will undoubtably find new code paths.
Generating test inputs at the system level (“fuzzing”) is most effective if one has a complete specification (such as a grammar) of the input language. In the absence of a specification, all known fuzzing approaches rely on a set of input samples to infer input properties and guide test generation. If the set of inputs is incomplete, however, so will be the resulting test cases; if one has _no+ input samples, meaningful test generation so far has been hard to impossible. In this paper, we introduce a means to determine the input language of a program from the program code alone, opening several new possibilities for comprehensive testing of a wide range of programs. Our symbolic parsing approach first transforms the program such that (1) calls to parsing functions are abstracted into parsing corresponding symbolic nonterminals, and (2) loops and recursions are limited such that the transformed parser then has a finite set of paths. Symbolic testing then associates each path with a sequence of symbolic nonterminals and terminals, which form a grammar. First grammars extracted from nontrivial C subjects by our prototype show very high recall and precision, enabling new levels of effectiveness, efficiency, and applicability in test generators.
https://dl.acm.org/doi/10.1145/3663529.3663790
Barevisor
Satoshi Tanda does a wonderful thing in helping those who want to learn hypervisors from first principles with this easy to understand implementation.
A bare minimum hypervisor on AMD and Intel processors for learners.
https://github.com/tandasat/barevisor
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Innovate UK Global Business Innovation Programme in Australia & Singapore - Cyber Security - “Innovate UK is inviting ambitious companies to participate in one of two Global Business Innovation Programmes on Cyber security, which aim to help UK businesses to grow and scale on a global stage through building R&D and innovation collaborations and partnerships. Innovate UK is offering two Global Business Innovation Programmes on Cyber security, one focused on Singapore and the other on Australia.”
The Cynical Genius Illusion: Exploring and Debunking Lay Beliefs About Cynicism and Competence - from 2018 but worth a read
Artificial intelligence
Books
Events
SANS CyberThreat 2024 CFP - closes August 7th for the event in the UK on the 9th and 10th of December
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.