Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week more edge device compromises. A reminder to all vendors and their customers (to drive market demand) we have published Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances. The evidence base is stark on why this is now required..
In the high-level this week:
CyberFirst Girls triumph in national cyber competition at iconic Jodrell Bank - NCSC announces
Hillcrest School and Sixth Form Centre took home the crown of 'Top Scoring State Newcomer', winning a £4,000 prize.
More than 14,500 girls from across the UK's four regions registered to take part in the 2024/25 competition which aims to inspire more girls to pursue cyber and technology in their education and future careers.
National Security Strategy (Joint Committee) - UK Parliament hears - oral evidence on Ransomware and Offensive Cyber
Public Accounts Committee - UK Parliament hears - Government cyber resilience
UK Cyber security sectoral analysis 2025 - Department for Science, Innovation and Technology and Feryal Clark MP publish - “This year’s analysis demonstrates exceptional performance, with the sector’s contribution to our economy reaching new heights – generating £13.2 billion in revenue and £7.8 billion in Gross Value Added.”
UK AI and software cyber security market analysis - Department for Science, Innovation and Technology and Feryal Clark MP publish - “The research explores three market segments in detail:
Cyber security for AI: Providers specialising in securing AI systems and applications.
Specialist software security providers: Firms with clear specialisation in software security provision.
Wider software security provision: firms which offer support for software security as part of a broader offering.”
Cyber Security Newsletter - March 2025 - Department for Science, Innovation and Technology publishes - Cyber Explorers Cup registration is till open for example “11-14 across the UK in an educational and interactive cyber security contest. Top performing teams can win a tech voucher worth up to £2,000 for their school.”
Performance Review of Digital Spend: Enabling Strategic Investment and Innovation - HM Treasury, Department for Science Innovation and Technology and Government Digital Service publish - “Risk reduction in technical debt and cybersecurity: Departments should establish a tech and cyber risk appetite which reflects the broader risk to the government and public from the department's activities. Investment plans will address legacy systems and technical debt, prioritising appropriate risk reduction over shortterm savings, with clear metrics to track improvement.”
New threat assessment: The cyber threat to the telecommunications sector in Denmark - Danish Center for Cybersikkerheds publishes - ”The threat level is being raised as there have been several attempts at cyber espionage against the European telecommunications sector in the past few years. The Danish Agency for Community Security assesses that the activity is an expression of increased interest in the telecommunications sector in Europe by state hackers, which increases the threat to the Danish telecommunications sector.”
Federal Contractor Cybersecurity Vulnerability Reduction Act of 2025 - Congress passes onto Senate it goes - “Not later than 180 days after the date on which the recommended contract language developed pursuant to subsection (a) is received, the Federal Acquisition Regulation Council shall review the recommended contract language and update the FAR as necessary to incorporate requirements for covered contractors to receive information about a potential security vulnerability relating to an information system owned or controlled by a contractor, in performance of the contract.”
Top 10 Information Security Threats for 2025 - Information-technology promotion agency Japan publishes - Ransomware and supply chains the top two.
Strings Attached: Talking about Russia's agenda for laws in cyberspace - Bytes and Borscht analyses - “Russia's longstanding proposals for "information security" agreements may sound cooperative, but they conceal a Trojan horse - a push to legitimize censorship, silence dissent, and bind others to rules it won’t follow.”
Data, waves and wind to be counted in the economy - BBC reports - “This update aims to capture areas that have grown since then, such as the cost of using up natural resources and the value of data.”
Data is an asset and there will be increasingly a want to trade it for collective benefit.
Cyber Threat Overview 2024 - ANSSI publishes - "ANSSI estimates that attackers associated with the cybercriminal ecosystem and reputedly linked to China and Russia are three of the main threats facing both critical information systems and the national ecosystem as a whole."
The future European security architecture: Dilemmas for EU strategic autonomy - European Union publishes - “complementarity between NATO and EU, whereby NATO should be in the lead for collective defence, and the EU should be in the lead for crisis management, measures against cyber-threats and fighting disinformation.”
The DPO cannot be the legal representative of a company - Italian Government judges - “It is quite evident that the role of DPO is therefore completely incompatible with that of legal representative of the company to which [they are] appointed”
Reporting on/from China
US communications regulator to create council to counter China technology threat - The Times reports - “The Federal Communications Commission is creating a national security council to bolster US defences against Chinese cyber attacks and help it stay ahead of China in critical technologies, such as artificial intelligence.”
Companies providing vulnerabilities to China’s MSS has ballooned to 324, up from 151 in 2023 - Dakota Cary updates - originally he reports “CNNVD’s team of technical support units grew from just fifteen companies in 2016 to 151 companies in 2023”
Is a light-speed chip unveiled by China-led team the future of ultra-fast processing? - South China Morning Post reports - “A new 100 gigahertz chip that harnesses light – not electricity – to synchronise processors could unlock the future of high-speed AI computing, next-generation communications and remote sensing, according to an international group of scientists led by China’s Peking University.”
Data-Centric Authoritarianism: How China’s Development of Frontier Technologies Could Globalize Repression - National Endowment for Democracy asserts - looks at four technologies which they assert “whose development could fortify Beijing’s tech-enabled authoritarian governance model” - the four are:
AI surveillance applications
Neuro- and immersive technologies
Quantum technologies
Digital currencies
Hong Kong Needs to Catch Up With Singapore in Web3, Animoca CEO Says - Caixin Global reports - “Apart from developing digital assets, Animoca is focused on building its metaverse business and investing in Web3 companies, with gaming firms taking up around 30% of its investment portfolio of more than 540 firms as of December.”
Alibaba’s New Model Adds Fuel to China’s AI Race - Time reports - “Chinese tech giant Alibaba released its latest AI reasoning model, QwQ-32B, resulting in an 8% spike in the company’s Hong Kong-listed shares. While less capable than America’s leading AI systems, such as OpenAI’s o3 or Anthropic’s Claude 3.7 Sonnet, the model reportedly performs about as well as its Chinese competitor DeepSeek’s model”
Chinese views of ‘Global Britain’: evidence from the government, media, and scholars - Beijing Foreign Studies University publishes - “First, the Chinese government completely rejects the UK’s roles as a faithful ally and a force for good, overlooks the roles of a Commonwealth leader and a European partner, and supports its roles as a global trading state and a great power. Second, while Chinese media and scholars share the government’s rejection of the faithful ally and force for good roles, they somewhat disagree with the government over the rest of these roles.”
AI
Fundamental Limitations in Defending LLM Finetuning APIs - UK AI Security Institute and University of Oxford - “In this work, we show that defences of fine-tuning APIs that seek to detect individual harmful training or inference samples (‘pointwise’ detection) are fundamentally limited in their ability to prevent fine-tuning attacks”
Pitfalls of Evidence-Based AI Policy - MIT and Mila publish - “Here, we argue that if the goal is evidence-based AI policy, the first regulatory objective must be to actively facilitate the process of identifying, studying, and deliberating about AI risks. We discuss a set of 15 regulatory goals to facilitate this and show that Brazil, Canada, China, the EU, South Korea, the UK, and the USA all have substantial opportunities to adopt further evidence-seeking policies.”
Superintelligent Agents Pose Catastrophic Risks: Can Scientist AI Offer a Safer Path? - Universit´e de Montr´eal, University of California, Imperial College London and McGill University publish - “This system is designed to explain the world from observations, as opposed to taking actions in it to imitate or please humans. It comprises a world model that generates theories to explain data and a question-answering inference machine. Both components operate with an explicit notion of uncertainty to mitigate the risks of overconfident predictions.” - humans might learn thing here..
EU and UK approaches to AI: Latest developments - European Union think tanks - “The EU has adopted a comprehensive risk-based regulatory framework, whereas the UK has a more light-touch regulatory approach. So far, the UK has not adopted a horizontal law on AI, but the current government has indicated that it plans to regulate the most powerful AI models.”
QwQ-32B: Embracing the Power of Reinforcement Learning - Qwen Team announce - “Our research explores the scalability of Reinforcement Learning (RL) and its impact on enhancing the intelligence of large language models. We are excited to introduce QwQ-32B, a model with 32 billion parameters that achieves performance comparable to DeepSeek-R1, which boasts 671 billion parameters (with 37 billion activated).” - noteworthy as it is another Chinese release - be interesting to see when this release is clocked.
Updated EU AI model contractual clauses - European Commission publishes - “key updates:
a full version for high-risk AI, aligned with the EU AI Act adopted on 13 June 2024;
a light version, customisable to specific needs for non-high-risk AI;
a commentary, providing guidance on how to use, customise and apply the clauses in practice.”
Cyber proliferation
Number of Italian spyware victims likely far higher than previously stated, researchers say - EurActiv reports - "Public reporting has provided a certain number of individuals in Italy that were notified by WhatsApp, but I submit to you that that number is almost certainly very low compared to the total number of Paragon cases," John Scott-Railton, a senior researcher at Citizen Lab, a human rights organisation that has investigated spyware abuses since 2012, said during an event in the European Parliament in Strasbourg today.
Bounty Hunting
Texas Man Convicted of Sabotaging his Employer’s Computer Systems and Deleting Data - Department of Justice announces - “The “kill switch” code — which Lu named “IsDLEnabledinAD”, abbreviating “Is Davis Lu enabled in Active Directory” — was automatically activated upon his termination on Sept. 9, 2019, and impacted thousands of company users globally”
Dual Russian And Israeli National Extradited To The United States For His Role In The LockBit Ransomware Conspiracy - Department of Justice announces - “Rostislav Panev’s extradition to the District of New Jersey makes it clear: if you are a member of the LockBit ransomware conspiracy, the United States will find you and bring you to justice,”
Uber Chief Security Officer conviction upheld - Ninth Circuit judges - “The panel affirmed Joseph Sullivan’s jury conviction for obstruction of justice and misprision of a felony arising from his efforts, while the Chief Security Officer for Uber Technologies, to cover up a major data breach even as Uber underwent investigation by the Federal Trade Commission into the company’s data security practices.”
Cyber insurance rates plunge globally as competition heats up: Marsh - Intelligence Insurer reports - “Cyber insurance rates fell 7% globally in the fourth quarter of 2024, with declines in every region, driven by fierce competition and stronger cybersecurity, Marsh has revealed.” - potential leading indicator of good news..
Reflections this week are Cortical Labs continues to inch closer in bringing synthetic biology to computing en mass. It blows my mind (no pun intended) that they are nearly at the point where you can deploy real code on/to interact with synthetic neurons in an almost commodity fashion.
Some of these elements are going to present a different set of cyber security challenges than we are used to which is going to be fascinating for all the reasons we would appreciate.
Not getting this via email? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Friday…
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Nothing of note this week
Reporting on China
Ghost in the Router: China-Nexus Espionage Actor UNC3886 Targets Juniper Routers
Lukasz Lamparski, Punsaen Boonyakarn, Shawn Chew, Frank Tse, Jakub Jozwiak, Mathew Potaczek, Logeswaran Nadarajan, Nick Harbour and Mustafa Nasser detail a campaign which further shines a light on telemetry quality and ability to do forensic investigations on such devices.
In mid 2024, Mandiant discovered threat actors deployed custom backdoors on Juniper Networks’ Junos OS routers. Mandiant attributed these backdoors to the China-nexus espionage group, UNC3886. Mandiant uncovered several TINYSHELL-based backdoors operating on Juniper Networks’ Junos OS routers. The backdoors had varying custom capabilities, including active and passive backdoor functions, as well as an embedded script that disables logging mechanisms on the target device.
related:
In July 2024, the Juniper Cybersecurity R&D team received a report from the field regarding a potential malware infection of a set of MX Series routers. The team launched a project – codenamed RedPenguin – with the following goals: 1) confirm that the routers were impacted by malicious software implants; 2) understand the malware designs and implementations; 3) assess how the malware was able to run on Junos OS routers, which are protected with the veriexec runtime integrity subsystem; 4) formulate recommendations to minimize the malware risk.
iSoon C2 from indictment
Department of Justice reveals aspects of the infrastructure alleged used by this threat actor to allow teams to go hunting through their historic datasets.
Domains (Namecheap, hosted at Choopa/Vultr):
ecoatmosphere[.]org
newyorker[.]cloud
outlook.newyorker[.]cloud
heidrickjobs[.]com
maddmail[.]site
asiaic[.]org
IPs:
40.82.48[.]85
45.77.132[.]157
149.28.66[.]186
140.82.48[.]85
149.248.57[.]11
95.179.202[.]21
45.61.136[.]31
104.168.135[.]87
https://www.justice.gov/opa/media/1391896/dl
Beijing Leveraging Freelance Hackers and Information Security Companies to Compromise Computer Networks Worldwide
FBI attributes.
FBI is releasing this Public Service Announcement to highlight that the Chinese government is using formal and informal connections with freelance hackers and information security (InfoSec) companies to compromise computer networks worldwide.
China's InfoSec ecosystem flourishes because China's government agencies, including its primary intelligence service the Ministry of State Security (MSS) and its domestic police agency the Ministry of Public Security (MPS), weaponize InfoSec companies by tasking companies that advertise legitimate cybersecurity services to also use their expertise to gain unauthorized access to victim networks to collect for China's intelligence services. This ecosystem of InfoSec companies and freelance hackers enables and encourages indiscriminate global cyber activity, while providing the Chinese government with a layer of plausible deniability.
https://www.ic3.gov/PSA/2025/PSA250305
VOLTZITE a threat group that overlaps with Volt Typhoon
Dragos released no IoCs or material technical details, this is broadly a marketing case study. But the fact there was allegedly such an intrusion is noteworthy..
Reporting on North Korea
New Spyware by North Korean APT37
Lookout details this new implant by an alleged North Korean threat actor. Noteworthy is the fact it managed to circumvent Google Play detections..
KoSpy is a new Android spyware attributed to the North Korean group APT37. It masquerades as utility apps and targets Korean and English speaking users.
The spyware was first observed in March 2022 and remains active with new samples still publicly hosted. It uses a two-stage C2 infrastructure that retrieves initial configurations from a Firebase cloud database.
KoSpy can collect extensive data, such as SMS messages, call logs, location, files, audio, and screenshots via dynamically loaded plugins.
The spyware has Korean language support with samples distributed across Google Play and third-party app stores such as Apkpure.
There is evidence of infrastructure being shared with APT43, which is another notorious North Korean state-sponsored group also known as Kimsuky.
Lazarus Strikes npm Again with New Wave of Malicious Packages
Kirill Boychenko details a further surge of activity here by an alleged North Korean threat actor. Provides further evidence that the software development eco-system is seen as a credible access vector for threat actors if there was any doubt!
In this campaign, Socket researchers uncovered BeaverTail malware embedded within seemingly benign packages —
is-buffer-validator,yoojae-validator,event-handle-package,array-empty-validator,react-event-dependency, andauth-validator— each closely mirroring tactics previously documented in Lazarus (Contagious Interview) operations.
https://socket.dev/blog/lazarus-strikes-npm-again-with-a-new-wave-of-malicious-packages
Hundreds of thousands of rubles for your secrets: Squid Werewolf cyberspies disguise themselves as recruiters
BI Zone russian reporting on an alleged North Korean threat actor applying similar tradecraft they have applied in other countries i.e. the fake recruiter.
In December 2024, BI.ZONE Threat Intelligence experts discovered an interesting phishing campaign, the victim of which was offered to consider a vacancy in an industrial organization. Detailed analysis showed that the Squid Werewolf cluster of activity (APT37, Ricochet Chollima, ScarCruft, Reaper Group) was behind the cyberattack.
Targeted phishing emails with trending topics allow attackers to quickly gain access to information in the systems of key employees of organizations.
Attackers are increasingly using Microsoft Word documents and Microsoft Excel spreadsheets, preferring archives with executable files, scripts or shortcuts.
Clusters involved in espionage are becoming more sophisticated in their methods and tools. To protect themselves, companies are advised to use advanced activity detection tools, such as EDR.
Reporting on Iran
Nothing of note this week
Reporting on Other Actors
Infostealer Campaign against ISPs
Rod Soto released this is in late February which I missed which is interesting due to the regional and sector targeting.
[We] identified a campaign targeting ISP infrastructure providers on the West Coast of the United States and the country of China. This mass exploitation campaign originates from Eastern Europe and uses simple tools that abuse victim’s computer processing power to install cryptomining payloads and binaries with diverse functions such as:
Credential Abuse. Main vector and initial access is driven by using well known weak credentials (Brute Force)
Data exfiltration via Command and Control (C2) servers.
Ability to deploy additional crimeware
Ability to self-terminate to avoid detection
Persistence and Entrenchment and disabling Remote Access
Pivot attacks to targeted CIDRs
https://www.splunk.com/en_us/blog/security/infostealer-campaign-against-isps.html
Blind Eagle: …And Justice for All
CheckPoint this actor continues to target Colombia interestingly, the relentless is notable.
Check Point Research discovered a series of ongoing campaigns targeting Colombian institutions and government entities since November 2024. The campaigns are linked to Blind Eagle, also known as APT-C-36, and deliver malicious
.urlfiles, which cause a similar effect to the CVE-2024-43451 vulnerability.CVE-2024-43451 exposes a user’s NTLMv2 hash, which can allow an attacker to authenticate as the user via pass-the-hash or relay attacks. This vulnerability can be triggered just by right-clicking, deleting, or dragging the file. While the Blind Eagle malicious file does not exploit this vulnerability, it triggers a WebDAV request in the same uncommon ways, notifying the attacker that the file was downloaded. Finally, when the user clicks on the file, it downloads the next-stage payload via another WebDAV request and executes the malware.
Microsoft patched the original vulnerability on November 12, 2024. Just six days later, Blind Eagle included this
.urlvariant in its attack arsenal and campaigns.The monitored campaigns targeted Colombian judicial institutions and other government or private organizations, with high infection rates. More than 1,600 victims were affected during one of these campaigns which took place around December 19, 2024. This infection rate is significant considering Blind Eagle’s targeted APT approach.
The malware is often delivered using legitimate file-sharing platforms such as Google Drive and Dropbox. However, in recent campaigns, Blind Eagle has also distributed its payloads through Bitbucket and GitHub.
The group utilizes malware and tools which are well-known within underground crime communities, a trend that continues with recent discoveries. To protect its malware, Blind Eagle leverages the Packer-as-a-Service HeartCrypt, which employs a .NET RAT that appears to be a variant of PureCrypter. The final stage payload is Remcos RAT.
Blind Eagle has long been suspected to originate from South America. We identified the group’s operating timezone as UTC-5, which aligns with several South American countries.
Operation fail (OPFail) revealed phishing campaigns in early March 2024 in which the group impersonated Colombian banks. These campaigns were highly successful, resulting in the collection of over 8,000 entries of Personally Identifiable Information (PII).
https://research.checkpoint.com/2025/blind-eagle-and-justice-for-all/
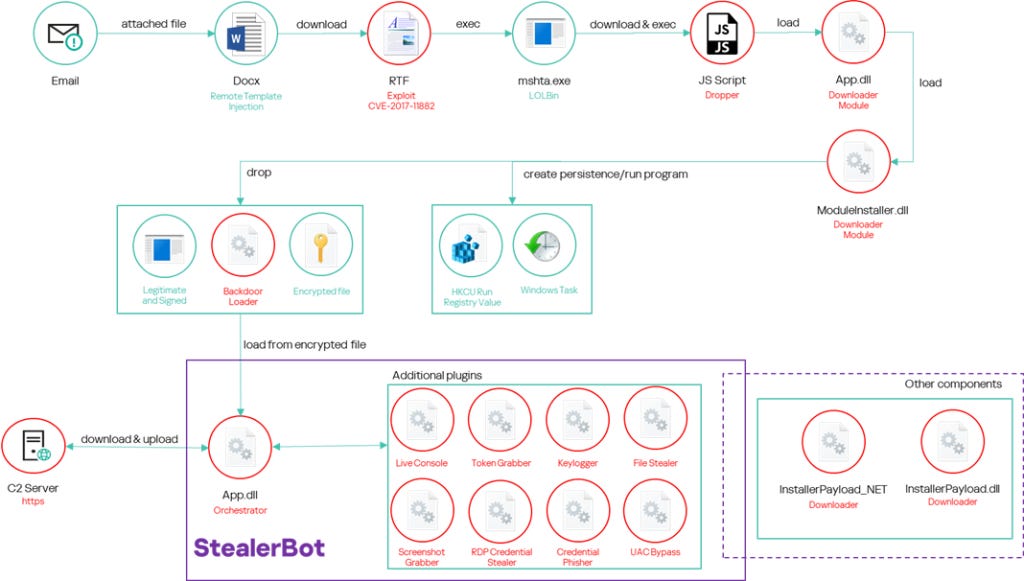
SideWinder targets the maritime and nuclear sectors with an updated toolset
Giampaolo Dedola and Vasily Berdnikov detail a campaign which gives a lesson in n-day exploitation.. eight year old n-days..
The attacker sends spear-phishing emails with a DOCX file attached. The document uses the remote template injection technique to download an RTF file stored on a remote server controlled by the attacker. The file exploits a known vulnerability (CVE-2017-11882) to run a malicious shellcode and initiate a multi-level infection process that leads to the installation of malware we have named “Backdoor Loader”. This acts as a loader for “StealerBot”, a private post-exploitation toolkit used exclusively by SideWinder.
https://securelist.com/sidewinder-apt-updates-its-toolset-and-targets-nuclear-sector/115847/
Discovery
How we find and understand the latent compromises within our environments.
100 Days of KQL
Aura shows they are no puny god..
cscript.exe or wscript.exe Launched with Script Engine Parameter
Potential Terminal Server or TermService Tampering via RDPWrap
Potential Discovery via PowerShell Test-Connection and Test-NetConnection
vql LolRMM
Matt Green does what he does best here..
This artifact hunts for Remote Monitoring and Management (RMM) tools using the LolRMM project. The goal is to detect installed or running instances.
Detectraptor generates a Regex csv that is pulled locally to the Velociraptor server via the tools management capability.
NOTE: This artifact may not detect RMMs that are not installed, renamed or using custom DNS.
https://github.com/mgreen27/DetectRaptor/blob/master/vql/LolRMM.yaml
UEFI Bootkit Hunting
Takahiro Haruyama delivers a wonderful presentation on hunting strategy here for low-level implant capabilities whilst showing the resultant value..
Not Lost in Translation: Rosetta 2 Artifacts in macOS Intrusions
Joshua Goddard
Rosetta 2 is Apple's translation technology for running x86-64 binaries on Apple Silicon (ARM64) macOS systems.
Rosetta 2 translation creates a cache of Ahead-Of-Time (AOT) files that can serve as valuable forensic artifacts.
Mandiant has observed sophisticated threat actors leveraging x86-64 compiled macOS malware, likely due to broader compatibility and relaxed execution policies compared to ARM64 binaries.
Analysis of AOT files, combined with FSEvents and Unified Logs (with a custom profile), can assist in investigating macOS intrusions.
https://cloud.google.com/blog/topics/threat-intelligence/rosetta2-artifacts-macos-intrusions/
New XCSSET malware adds new obfuscation, persistence techniques to infect Xcode projects
Microsoft Threat Intelligence details an evolving macOS implant and gives a couple of hunting tips..
This sub-module establishes persistence through two different methods, zshrc and Dock, which will be discussed in the following sections. It first creates a folder named com.apple.finder in the ~/Library/Caches/ directory.
Defence
How we proactively defend our environments.
Stopping Cybercriminals from Abusing Cobalt Strike
Bob Erdman and Pieter Ceelen detail the progress in trying to prevent the misuse of the latest versions of this product. Interesting that legal mechanisms have been deployed here..
Over the past two years, the number of unauthorized copies of Cobalt Strike observed in the wild has decreased by 80%, drastically reducing availability to cybercriminals.
..
Additionally, we are continuing to send takedown notices to hosting providers, raising awareness of the illicit use of unauthorized copies. We actively track these activities to the point of origin, identifying root causes to prevent reoccurrence. We concurrently issue notices on a persistent basis until these illegal versions are removed from web properties. Compliant web properties are also passively monitored in case of reappearance
https://www.cobaltstrike.com/blog/update-stopping-cybercriminals-from-abusing-cobalt-strike
Incident Writeups & Disclosures
How they got in and what they did.
Nothing of note this week
Vulnerability
Our attack surface.
CVE-2025-27607: Python JSON Logger
Interesting vulnerability due to a dependency which was unclaimed due to being deleted by the owned that could have been very painful if exploited..
Python JSON Logger is a JSON Formatter for Python Logging. Between 30 December 2024 and 4 March 2025 Python JSON Logger was vulnerable to RCE through a missing dependency. This occurred because msgspec-python313-pre was deleted by the owner leaving the name open to being claimed by a third party. If the package was claimed, it would allow them RCE on any Python JSON Logger user who installed the development dependencies on Python 3.13 (e.g. pip install python-json-logger[dev]). This issue has been resolved with 3.3.0.
https://nvd.nist.gov/vuln/detail/CVE-2025-27607
Offense
Attack capability, techniques and trade-craft.
Beyond the Hook: A Technical Deep Dive into Modern Phishing Methodologies
Alexandre Nesic details the contemporary techniques..
Browser-in-the-Browser
Fake CAPTCHA
Attacker-in-The-Middle
Frameless Browser-in-the-Browser
noVNC
https://blog.quarkslab.com/technical-dive-into-modern-phishing.html
Panix: Five new persistence techniques on Linux
Ruben Groenewoud introduces five new techniques to test your detection tradecraft against..
D-Bus Persistence
Leverage D-Bus to create an overly permissive D-Bus Method that allows for root-privilege reverse shell backdoors.
Initramfs Persistence
Modify the boot process by injecting custom payloads into the initramfs, ensuring your persistence mechanism is active before the operating system loads.
GRUB Persistence
Embed backdoor functionality in the bootloader configuration to execute your payload at system startup.
Polkit Persistence
Modify the system authentication process using Polkit rules or PKLA files, providing a stealthy backdoor to maintain control.
Network-Manager Persistence
Utilize Network-Manager’s dispatcher capabilities to trigger payload execution during network change events.
https://github.com/Aegrah/PANIX/releases/tag/panix-v2.1.0
RunAs-Stealer
A collection of techniques which whilst applied to RunAs could be applied elsewhere. Good test case for detection engineering..
RunAs Utility Credential Stealer implementing 3 techniques : Hooking CreateProcessWithLogonW, Smart Keylogging, Remote Debugging
https://github.com/DarkSpaceSecurity/RunAs-Stealer
Kerberoasting w/o the TGS-REQ
Rasta Mouse provides an edge to this techniques which detection coverage is worth validating..
Strategies to detect kerberoasting include looking for spikes in TGS-REQs from a single source, or TGS-REQs for 'honeypot' SPNs. A careless attacker can get caught quite easily. Another method of obtaining TGS-REPs could be to listen for them on the wire. However, in this short post, I'll show how an attacker can use service tickets that have already been requested legitimately by a user.
https://rastamouse.me/kerberoasting-without-tgs-reqs/
Using RDP without leaving traces: the MSTSC public mode
Marc-Andre Moreau
Have you ever wondered what the "/public" command-line option in MSTSC actually does? It enables "public mode" in the RDP client, a feature somewhat similar to "incognito mode" in web browsers. This is a feature meant to be used on a "public" or "shared" computer, where users might want to prevent credentials, session details, and cached images from being stored locally.
For forensic analysts, the traces left behind by a malicious attacker using MSTSC on a compromised system can be a gold mine of information.
https://blog.devolutions.net/2025/03/using-rdp-without-leaving-traces-the-mstsc-public-mode/
RedExt — Offensive Chrome extension framework
ShadowByte provides capability which is a unique take and which will be interesting to see if it is adopted.
a Chrome extension that acts as a beacon and C2 framework to be able to explore and understand the potential of using Chrome extension from an offensive perspective.
It combines a Manifest V3 Chrome extension with a Flask-based C2 server to provide comprehensive browser data collection and analysis capabilities through a modern dark-themed dashboard.
https://github.com/Darkrain2009/RedExt
Exploitation
What is being exploited..
Ballista – New IoT Botnet Targeting Thousands of TP-Link Archer Routers
Matan Mittelman and Ofek Vardi detail an n-day being exploited at scale..
As part of its initial access vector, the Ballista botnet exploits CVE-2023-1389. This vulnerability in the TP-Link Archer router’s web management interface (T1190) stems from the lack of sanitization of user input in the country form of the /cgi-bin/luci;stok=/locale endpoint, resulting in unauthenticated command execution with root privileges.
Long Live The Vo1d Botnet: New Variant Hits 1.6 Million TV Globally
Alex.Turing, Acey9, Wang Hao and heziqian show the scale of some bot nets..
Samples & Infrastructure: 89 new samples captured, a lot of infrastructure, including 2 Reporter, 4 Downloaders, 21 C2 domains, 258 DGA seeds, and over 100,000 DGA domains.
Daily active IPs: ~800,000, peaking at 1,590,299 on January 14, 2025.
https://blog.xlab.qianxin.com/long-live-the-vo1d_botnet/
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
BluetoothTools - 29 undocumented commands in the ESP32
Antonio Vázquez Blanco and Miguel Tarascó Acuña detail undocumented commands in this Bluetooth implementation that will aid capability development..
.. widely reported as a backdoor, more an engineeringdoor.
https://www.documentcloud.org/documents/25554812-2025-rootedcon-bluetoothtools/
Unraveling Time: A Deep Dive into TTD Instruction Emulation Bugs
Dhanesh Kizhakkinan and Nino Isakovic remind us the challenges of emulation..
TTD relies heavily on accurate CPU instruction emulation to faithfully replay program executions. However, subtle inaccuracies within this emulation process can lead to significant security and reliability issues, potentially masking vulnerabilities or misleading critical investigations—particularly incident response and malware analysis—potentially causing analysts to overlook threats or draw incorrect conclusions.
https://cloud.google.com/blog/topics/threat-intelligence/ttd-instruction-emulation-bugs
Zen and the Art of Microcode Hacking
Josh Eads, Tavis Ormandy, Matteo Rizzo, Kristoffer Janke and Eduardo Vela Nava when AES-CMAC with a fixed key specified in a NIST document bites..
We noticed that the key from an old Zen 1 CPU was the example key of the NIST SP 800-38B publication (Appendix D.1 2b7e1516 28aed2a6 abf71588 09cf4f3c) and was reused until at least Zen 4 CPUs. Using this key we could break the two usages of AES-CMAC: the RSA public key and the microcode patch contents. We were able to forge new public keys which generated the same hash as the authentic AMD key. Additionally, we calculated collisions for signatures, and were able to generate a microcode patch that shares the same signature as another message that was legitimately signed.
https://bughunters.google.com/blog/5424842357473280/zen-and-the-art-of-microcode-hacking
cradle
Yigit Colakoglu, Razvan Dinu, D. Popovici and Calin-Marian Diacicov provide an amazing open source project for all. Also a real bootstrap for boutique cyber threat intelligence companies..
CRADLE is an open-source web application designed to empower Cyber Threat Intelligence (CTI) analysts. The platform streamlines threat analysis workflows through collaborative note-taking, visual relationship mapping, and comprehensive report generation.
Key Features:
Collaborative Investigation: Shared workspace for team-based threat analysis
Entity Relationship Visualization: Graphical representation of connections between threat actors and artifacts
Report Generation: Exportable intelligence reports in multiple formats
Modular Architecture: Easily extensible design for future enhancements
https://github.com/prodaft/cradle/
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Democratising Data Integration. Standardising Communication Protocols for Interoperable Data Processing and Analytics Tools in Strategic Information Environments - “This report provides analysis and practical recommendations for establishing unified data standards, securing communication frameworks, and enabling multinational collaboration. It offers a clear pathway for NATO allies and partners to build resilient, cost-effective, and responsive data ecosystems that support sustained operational readiness and adaptability in an evolving information environment.”
Artificial intelligence
Books
Events
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.