CTO at NCSC Summary: week ending March 9th
We know more about what’s in our sausages than in our software. That’s not sustainable.
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note..
In the high-level this week:
ACD 2.0: Insights from the external attack surface management trials - UK National Cyber Security Centre publishes based on 900 days of experimentation as part of Active Cyber Defence 2.0
Users gain significant cyber security benefits from a range of EASM features, not just from specific risks and issues data. Notably, features providing improved visibility of digital footprint allowed defenders to commission work to protect or decommission assets previously unknown to security teams.
Automated discovery provides valuable visibility of an organisation's digital footprint, which is essential for effective cyber defence.
Cyber Threats to Canada's Democratic Process: 2025 Update - Canadian Centre for Cyber Security publishes - “In the last two years, hostile actors have increasingly used generative AI to target global elections, including in Europe, Asia, and in the Americas. While TDP 2023 counted only one case of generative AI being used to target an election between 2021 and 2023, we observed 102 reported cases of generative AI being used to interfere with or influence 41 elections, or 27% of elections, held between 2023 and 2024.”
President Donald J. Trump Establishes the Strategic Bitcoin Reserve and U.S. Digital Asset Stockpile - The White House announces - “The Strategic Bitcoin Reserve will be capitalized with bitcoin owned by the Department of Treasury that was forfeited as part of criminal or civil asset forfeiture proceedings. Other agencies will evaluate their legal authority to transfer any bitcoin owned by those agencies to the Strategic Bitcoin Reserve.”
Cyberattack detected at Polish space agency, minister says - Reuters reports - “The agency confirmed to news agency PAP that a cybersecurity incident had occurred. The situation is being analysed, and in order to secure data, the POLSA network was immediately disconnected from the Internet, it told PAP.”
Global Compendium on Responsible Cyber Behaviour - RUSI publishes - “The case studies illuminate how responsibility is articulated and operationalised through institutional development, legal and regulatory frameworks, cooperative agreements, and responses to major cyber incidents.”
Digital Corporate Autonomy: Geo-Economics and Corporate Agency in Conflict and Competition - EU Cyber Direct reviews - “Our analysis reveals a broad spectrum of government-corporate interaction and a high level of digital corporate autonomy set against the contexts of war – the height of statecraft – and hegemonic rivalry. We conclude that digital corporate autonomy underlines the importance of scholarly attention to corporate agency and behaviour.”
ENISA Threat Landscape: Finance Sector - ENISA publishes - “Social engineering campaigns, including phishing, smishing and vishing, were prevalent tactics used by cybercrime threat actors. These incidents aimed to steal sensitive information and commit financial fraud, affecting individuals (38%) and credit institutions (36%). The result was financial loss, large-scale financial crimes, and data exposure.”
ENISA NIS360 2024 - ENISA publishes - “The NIS360 is a new ENISA product that assesses the maturity and criticality of sectors of high criticality under the NIS2 Directive, providing both a comparative overview and a more in-depth analysis of each sector.”
Deterring the Abuse of U.S. IaaS Products: Recommendations for a Consortium Approach - Institute for Security and Technology suggests - “The proposed rule also suggested an IaaS provider’s participation in a “consortium to develop and maintain privacy-preserving data sharing and analytics to enable improved detection and mitigation of malicious cyber-enabled activities” would be a factor in granting such an exemption request. This report therefore examines the proposed rule’s inclusion of the “consortium” concept; provides recommendations for how an ADP Consortium could be shaped to best accomplish the government’s overall objective of deterring abuse, including beyond the proposed rule’s focus on data sharing and analytics;”
On the trail of money from Russian advertisements. The path from the Russian Ministry of Defense to personal data collected from Romania - Snoop digs - “An online advertising network with Russian roots is fueling extremist propaganda and financial fraud, using Romania as a ground for data collection and manipulation of public opinion. Behind seemingly harmless advertisements, money and information circulate to structures close to the Kremlin, in a sophisticated mechanism of influence and disinformation.”
Reporting on/from China
Witness Testimony: " End the Typhoons: How to Deter Beijing’s Cyber Actions and Enhance America’s Lackluster Cyber Defenses” - The Select Committee on the CCP hears - “The PRC is conducting a comprehensive cyber campaign against the United States, and our current defenses are not keeping pace. Chinese state hackers prepositioned malware within our power grids, pipelines, water treatment plants, and other critical infrastructure. “”
US congressional panel urges Americans to ditch China-made routers - Reuters reports - “A U.S. congressional committee on Wednesday urged Americans to remove Chinese-made wireless routers from their homes, including those made by TP-Link, calling them a security threat that opened the door for China to hack U.S. critical infrastructure.”
Singapore charges three with fraud that media link to Nvidia chips - Reuters reports - “Broadcaster Channel News Asia said it understood the cases were linked to the alleged movement of Nvidia chips from Singapore to be used by DeepSeek, without identifying its source.”
China Abruptly Replaces Tech Czar Behind AI and Chip Push - Bloomberg reports - “Jin Zhuanglong, a 60-year-old aerospace expert, is no longer listed as party secretary of the Ministry of Industries and Information Technology, after he disappeared from public view last December fueling speculation about his position.”
China opens up its vast telecoms sector to 13 foreign companies - South China Morning Post reports - “The companies included in the first batch of approvals are mainly Chinese affiliates of major overseas telecoms groups, such as German giants Deutsche Telekom and Siemens.”
Taking a RISC: Hong Kong puts weight behind China’s open-source chips bet - South China Morning Post reports - “Last month, a team from the Chinese Academy of Sciences (CAS), a top government research organisation, announced that it would deliver its RISC-V-based XiangShan CPU this year. The team said earlier this month it had adapted XiangShan to support DeepSeek-R1, the popular open-source reasoning large language model developed by Hangzhou-based AI start-up DeepSeek.”
Hong Kong to launch 2 AI forums aimed at bridging China and the world amid US tech war - South China Morning Post reports - “The government-owned Hong Kong Investment Corporation (HKIC), which manages HK$62 billion (US$8 billion) of funds, plans to debut a conference for young emerging artificial intelligence (AI) scientists, as the city strives to become a bridge between China and the world amid growing Sino-US technology rivalry.”
China puts brakes on US stock listings for homegrown companies - Financial Times reports - “China’s securities regulator has clamped down on small companies’ listings on New York stock exchanges after many of them became vehicles for price-rigging, causing heavy losses for US investors.”
China Quant Says Funds Must Adopt AI to Survive After DeepSeek - Bloomberg reports - “In three years, quants that don’t use AI will inevitably be eliminated,” said Feng Ji, chief executive officer of Baiont Quant, which uses machine learning to do trading with no human intervention. “DeepSeek is a final call to those who still don’t believe in the power of AI.”
AI
National AI Cybersecurity Readiness Metric - Global Cyber Security Capability Centre metricises - “The National AI Cybersecurity Readiness Metric is a newly developed tool to help countries manage AI risks and opportunities.”
Multi-Agent Risks from Advanced AI - Co-operative AI Foundation publishes - “The rapid development of advanced AI agents and the imminent deployment of many instances of these agents will give rise to multi-agent systems of unprecedented complexity. These systems pose novel and under-explored risks. In this report, we provide a structured taxonomy of these risks by identifying three key failure modes (miscoordination, conflict, and collusion) based on agents’ incentives, as well as seven key risk factors (information asymmetries, network effects, selection pressures, destabilising dynamics, commitment problems, emergent agency, and multi-agent security) that can underpin them”
Build Allied AI or Risk Fighting Alone - Centre for New American Security opines - “In future high-speed conflicts, the United States and allied militaries will need to share large volumes of data parsed by AI to identify targets and help connect one military’s sensors to another’s shooters, which may be autonomous uncrewed platforms carrying out strike missions. But this more efficient vision of future warfare will not be possible if the United States and its allies fail to align their military AI investments, strategies, and employment.”
Cyber proliferation
Three executives of the NSO Group charged for their responsibility in the Pegasus espionage case - Iridia announces - “The Provincial Court has ruled in favour of Irídia and ordered the indictment of three NSO Group executives. They will be investigated for the alleged crime of discovery and disclosure of secrets. This follows the judge’s refusal to charge them, limiting the investigation to production and commercialisation companies.”
Troubled ex-spyware fund braces for €125mn hit from soured Romanian deal - Financial Times reports - “The troubled private equity fund behind a controversial investment in Israeli spyware company NSO Group is bracing for a fresh €125mn hit from a separate deal involving a Romanian betting company.”
Bounty Hunting
10 Chinese Nationals Charged With Large-Scale Hacking Of U.S. And International Victims On Behalf Of The Chinese Government - US Department of Justice announces - “Eight Defendants Were Employees of i-Soon, a Chinese Company Hacking at the Direction of the Chinese Government, and Two Defendants are Chinese Officials Who Directed the Hacks”
Justice Department Charges 12 Chinese Contract Hackers and Law Enforcement Officers in Global Computer Intrusion Campaigns - US Department of Justice announces - “Chinese Law Enforcement and Intelligence Services Leveraged China’s Reckless and Indiscriminate Hacker-for-Hire Ecosystem, Including the ‘APT 27’ Group, to Suppress Free Speech and Dissent Globally and to Steal Data from Numerous Organizations Worldwide,”
Sanctions on China-Based Hacker and Data Broker - US Department of State announces - “The Department of Justice today unsealed indictments charging Zhou Shuai and Yin Kecheng, eight employees of i-Soon, a Chinese technology company, and two officers of China’s Ministry of Public Security (MPS) with a variety of hacking-related offenses. Further, the Diplomatic Security Service’s Rewards for Justice Program (RFJ) is offering up to $10 million for information on i-Soon, its employees, and the MPS officers engaged in malicious cyber activities highlighted in the Department of Justice’s indictments.”
The role of alternative risk transfer solutions in the future of cyber insurance - Reinsurance Business reports - “A recent report from the Geneva Association (GA) highlighted how maintaining the pace of growth seen across the cyber insurance market will require additional capital to manage ever-more complex cyber risks. The report explored the potential of alternative risk transfer (ART) solutions, including insurance-linked securities (ILS), such as cyber catastrophe bonds, to facilitate broader distribution of these risks to financial markets.”
Reflections this week continue around the simmer we are in with regards to AI application in cyber attack and defence.
Be it the AI HTTP Analyzer (It examines HTTP requests and responses for potential security vulnerabilities such as SQL injection, XSS, CSRF, and other threats.), Turul which is a C2 framework which has MalwareGAN (transforms programs with MalwareGAN by inserting carefully selected redundant code at OST compilation time -to subvert clustering detections), Baby Naptime (a vulnerability analysis tool that uses Large Language Models (LLMs) to discover and exploit native vulnerabilities) and AI large model code audit-Java vulnerability mining (from China which found real remote code execution vulnerabilities)..
As I said at an internal conference this week - these tools are work aid improvements as IDA was with is graph view and xref abilities compared to objdump etc. Disruption is here, so get on board...
Finally it was lovely to meet a number of self described readers in Barcelona at Mobile World Congress this week. Thank you to the Alex Leadbeater and Samantha Knight from the GSMA for the platform. Patrick Donegan summarised my pithy contributions to one of the panels which applies more broadly:
1) We suffer from optimism bias. We believe we are doing a good job - that we are keeping up with the threat landscape. That is not true.
2) Telecommunications operators are being penetrated by default passwords and poor configurations.
3) We know more about what’s in our sausages than in our software. That’s not sustainable.
The sausages line appears to have resonated...
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Exposing Russian EFF Impersonators: The Inside Story on Stealc & Pyramid C2
Hunt.io details an alleged Russian criminal campaign
A threat group impersonating the Electronic Frontier Foundation (EFF) is targeting Albion Online players through decoy documents designed to lend credibility while malware executes in the background.
Albion Online is a multiplayer online role-playing game (MMORPG) with a player-driven economy. While real-money transactions are against the game's terms of service and can result in permanent bans, third-party markets exist where in-game assets apre exchanged for money, making player accounts a lucrative target.
Players on the game's forum have reported receiving messages from other members directing them to phishing websites, with the EFF's name used as a pretext to discuss the security of in-game goods tied to their accounts.
https://hunt.io/blog/russian-speaking-actors-impersonate-etf-distribute-stealc-pyramid-c2
Reporting on China
Silk Typhoon targeting IT supply chain
Microsoft Threat Intelligence details this shift in tactics by this alleged Chinese threat. This provides further evidence we do really need find a way to get a grip on supply chain practicalities.
[We] identified a shift in tactics by Silk Typhoon, a Chinese espionage group, now targeting common IT solutions like remote management tools and cloud applications to gain initial access. While they haven’t been observed directly targeting Microsoft cloud services, they do exploit unpatched applications that allow them to elevate their access in targeted organizations and conduct further malicious activities. After successfully compromising a victim, Silk Typhoon uses the stolen keys and credentials to infiltrate customer networks where they can then abuse a variety of deployed applications, including Microsoft services and others, to achieve their espionage objectives.
https://www.microsoft.com/en-us/security/blog/2025/03/05/silk-typhoon-targeting-it-supply-chain/
Where is i-SOON Now?
Natto Thoughts is back showing that with access to the right data from China you can understand..
Although information about the leaks cannot be found within China, information about the company’s activities and fortunes remains publicly available. The Natto Team cross-checked several Chinese business registration databases and discovered that, as of March 4, 2025, Shanghai i-SOON and its three related companies – Sichuan i-SOON, Sichuan Daitabosi, and Taizhou i-SOON – are still registered as being in business operation. The current total number of employees from the four i-SOON companies is 104 (see chart below) which is close to a 33 percent decrease from the 160 employees recorded in 2022.
nattothoughts.substack.com/p/where-is-i-soon-now
Reporting on North Korea
Likely DPRK Network Backstops on GitHub, Targets Companies Globally
Nisos details an alleged North Korean campaign which hits all the notes of recent reporting. This highlights that developers are akin to the supply chain challenge more broadly.
Personas claim to have experience in three areas: developing web and mobile applications, knowledge of multiple programming languages, and an understanding of blockchain technology.
Personas have accounts on employment and people information websites, IT industry-specific freelance contracting platforms, software development tools and platforms, and common messaging applications, but they typically lack social media accounts, suggesting that the personas are created solely for the purpose of acquiring employment.
Profile photos are digitally manipulated. Often the DPRK-affiliated IT worker’s face is pasted on top of a stock photo to show the individual working with colleagues.
Personas within the network use similar email addresses.
Email addresses often include the same numbers, such as 116, and the word “dev”.
https://nisos.com/research/dprk-github-employment-fraud/
Kimsuky Group's Watering Hole Attack, Beware of Malicious File Distribution Disguised as Unification Field Education Support
알약4 details a campaign allegedly by North Korea which shows how sub population targeting works..
This attack involves uploading a malicious application document file to a notice board created to recruit students for a unification education program, and users who visit the site to apply for the education program download and execute the application file, thereby becoming infected with the malicious file.
https://blog-alyac-co-kr.translate.goog/5534?_x_tr_sl=auto&_x_tr_tl=en&_x_tr_hl=en&_x_tr_pto=wapp
Reporting on Iran
Call It What You Want: Threat Actor Delivers Highly Targeted Multistage Polyglot Malware
Joshua Miller and Kyle Cucci detail an alleged Iranian campaign which is an interesting operation due to the targeting. It also shows a degree of sophistication even if the initial access tradecraft on show was rather basic..
[We] identified a highly targeted email-based campaign targeting fewer than five Proofpoint customers in the United Arab Emirates with a distinct interest in aviation and satellite communications organizations, along with critical transportation infrastructure.
The malicious messages were sent from a compromised entity in a trusted business relationship with the targets, and used lures customized to every target.
This campaign led to the newly discovered backdoor dubbed Sosano by Proofpoint, which leveraged numerous techniques to obfuscate the malware and its payload, likely indicating an adversary with significant development capabilities with an interest in protecting their payloads from easy analysis.
The campaign used polyglot files to obfuscate payload content, a technique that is relatively uncommon for espionage-motivated actors in Proofpoint telemetry and speaks to the desire of the operator to remain undetected.
Proofpoint tracks this new threat cluster as UNK_CraftyCamel.
Reporting on Other Actors
Malvertising campaign leads to info stealers hosted on GitHub
Microsoft Threat Intelligence detail a campaign which is notable due to its scale. Also it provides further evidence not all is right in the advertising eco-system.
In early December 2024, Microsoft Threat Intelligence detected a large-scale malvertising campaign that impacted nearly one million devices globally in an opportunistic attack to steal information. The attack originated from illegal streaming websites embedded with malvertising redirectors, leading to an intermediary website where the user was then redirected to GitHub and two other platforms. The campaign impacted a wide range of organizations and industries, including both consumer and enterprise devices, highlighting the indiscriminate nature of the attack.
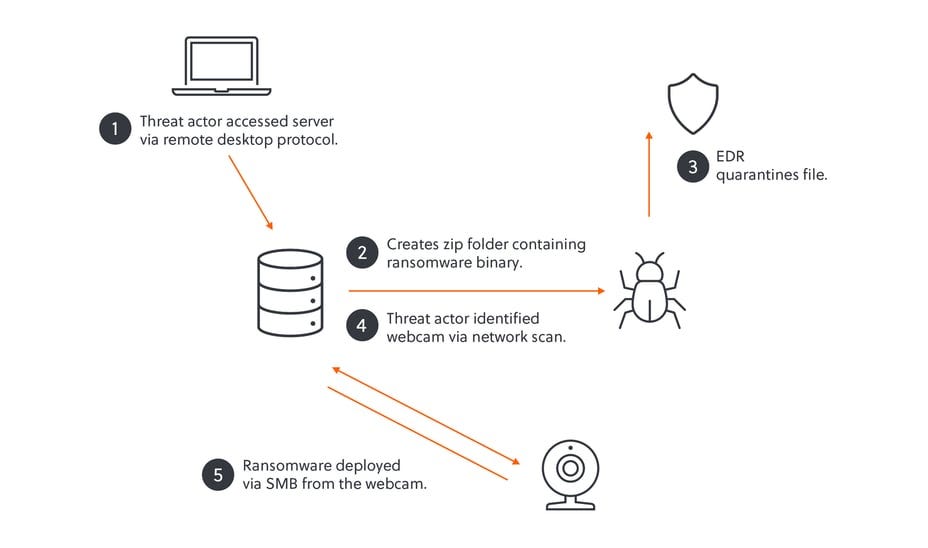
Akira deploys ransomware via webcam
Gavin Hull, Cameron Trivella and Jon Seland show why network monitoring and being able to isolate devices is important as part of the response process.
After identifying the webcam as a suitable target, the threat actor began deploying their Linux-based ransomware with little delay. As the device was not being monitored, the victim organisation's security team were unaware of the increase in malicious Server Message Block (SMB) traffic from the webcam to the impacted server, which otherwise may have alerted them. Akira was subsequently able to encrypt files across the victim’s network
https://www.s-rminform.com/latest-thinking/camera-off-akira-deploys-ransomware-via-webcam
Discovery
How we find and understand the latent compromises within our environments.
100 Days of KQL
Aura shows they have a heart like Tony Stark with more detections this week:
Detecting Hotkey- Based Keyloggers Using an Undocumented Kernel Data Structure
Asuka Nakajima
After discovering that ETW cannot directly monitor calls to the RegisterHotKey API, we started exploring detection methods that don't rely on ETW. During our investigation, we wondered, "Isn't the information for registered hotkeys stored somewhere? And if so, could that data be used for detection?" Based on that hypothesis, we quickly found a hash table labeled gphkHashTable within NtUserRegisterHotKey
https://www.elastic.co/security-labs/detecting-hotkey-based-keyloggers
Enhanced detection of obfuscated HTTPS tunnel traffic using heterogeneous information network
Mengyan Liu, Gaopeng Gou, Gang Xiong, Junzheng Shi, Zhong Guan, Hanwen Miao and Yang Li put a novel twist on a detection problem but translating to a graph node classification one.. or applied machine learning for the win!
In this paper, we propose HINT, a novel method that transforms HTTPS tunnel traffic detection into a graph node classification problem. Specifically, we construct a heterogeneous information graph to model the connections between clients and the VPN services. To enrich the graph’s semantics, we incorporate distinctive characteristics that are challenging to disguise and encapsulate them into specialized fingerprint nodes. Then we apply a hierarchical attention mechanism to automatically discern the significance of different nodes. Experimental results and extended analysis reveal that by integrating host topology, service statistics, and client traffic features, HINT maintains robust classification power when traffic shaping and padding techniques are employed.
https://www.sciencedirect.com/science/article/abs/pii/S1389128624008077
Uncovering .NET Malware Obfuscated by Encryption and Virtualization
Lee Wei Yeong details a rather invested in bit of code here..
Adversaries use the following techniques to deliver popular malware families like Agent Tesla, XWorm and FormBook/XLoader:
Code virtualization
Staged payload delivery
Dynamic code loading to introduce new code at runtime
Advanced Encryption Standard (AES) encryption
Creating multi-stage payloads that are self-contained within the original sample
https://unit42.paloaltonetworks.com/malware-obfuscation-techniques/
Defence
How we proactively defend our environments.
Everything Old Is New Again: Hardening the Trust Boundary of VBS Enclaves
Josh Watson details a set of considerations for around what the trust boundaries are in CVS enclaves. Some real trip hazards detailed here which due their low level nature which inevitably mean some VBS enclave code won’t implement them..
Since support for third-party enclaves was announced last year, it is important that we highlight this new threat model and its design patterns for the broader developer community. In this blog post, we will present some recommendations that you can follow to help harden your enclave against common vulnerabilities.
…
Never trust VTL0
Validate pointers are in VTL0
Capture VTL0 structures in VTL1 before checks
Avoid reentrancy if possible
Keep secrets in the enclave
Incident Writeups & Disclosures
How they got in and what they did.
Rubrik
How they got is in not disclosed..
The Rubrik Information Security Team recently discovered anomalous activity on a server that contained log files. We promptly took the server offline to mitigate the risk. An investigation supported by a third party forensic partner has confirmed that the incident was isolated to this one server and we found no evidence of unauthorized access to any data we secure on behalf of our customers, or our internal code.
Through our investigation we discovered that an unauthorized actor accessed a small number of log files, most of which contained non-sensitive information. One file contained some limited access information. Out of an abundance of caution, we have rotated keys to mitigate any residual risk, even though we found no evidence that access information was misused.
We would like to reiterate that after a detailed analysis with the third party partner, we have found no evidence of unauthorized access to any data we secure on behalf of our customers or our internal code.
https://www.rubrik.com/blog/company/25/rubrik-information-security-team-update
Vulnerability
Our attack surface.
how to gain code execution on millions of people and hundreds of popular apps
Kibty shows how a little bit of research can lead to a low hanging fruit supply chain compromise that would get you a foothold in millions of places..
i could push auto updates to all applications using todesktop, such as:
clickup (https://clickup.com)
cursor (https://cursor.com) (update: cursor has now switched off of todesktop to their own build system)
linear (https://linear.app)
notion calendar (https://calendar.notion.so)
https://kibty.town/blog/todesktop/
MitM attack against OpenSSH's VerifyHostKeyDNS-enabled client
Unclear how common this configuration is so I asked Copilot..
The
VerifyHostKeyDNSconfiguration in OpenSSH is not extremely common but is used by those who prioritize enhanced security through DNS-based SSH host key verification. This option allows the SSH client to verify the server’s host key using DNS records (SSHFP) if DNSSEC is enabled, adding an extra layer of security
The vulnerability is oof..
The OpenSSH client is vulnerable to an active machine-in-the-middle attack if the VerifyHostKeyDNS option is enabled (it is disabled by default): when a vulnerable client connects to a server, an active machine-in-the-middle can impersonate the server by completely bypassing the client's checks of the server's identity.
https://seclists.org/fulldisclosure/2025/Feb/18
VMSA-2025-0004: a critical VMware Security Advisory (VMSA)
Nightmare fuel..
This is a situation where an attacker who has already compromised a virtual machine’s guest OS and gained privileged access (administrator or root) could move into the hypervisor itself.
Multiple vulnerabilities affecting Draytek routers
Faradaysec detail various vulnerabilities but this has to be the next ‘return 4’
Affected Vigor routers generate WAN login second-factor authentication codes in a predictable way. The codes can be calculated by knowing the time elapsed since boot, allowing an attacker to bypass this security measure. For example, an attacker can force a reboot by exploiting other vulnerabilities like CVE-2024-41338.
CVE-2025-25182: Stroom authentication bypass
A vulnerability in a GCHQ library.. thank you Liad Eliyahu and Miggo Security for the disclosure..
Before the token in the X-Amzn-Oidc-Data header is verified, the signer and kid fields are extracted from the token's header (Line 478).
The region is then extracted from the signer without any verification, the kid isn't being sanitized either.
The region and kid are being used to construct the URL to fetch the public key.
Offense
Attack capability, techniques and trade-craft.
The Cat Flap - How to really Purrsist in AWS Accounts
Dr. Michael "rootcat" Gschwender details a technique to be aware of..
You gain initial access to an AWS account. Somehow.
You check if you have permission to access/create/change AWS roles.
You create or edit the AWSControlTowerExecution role, by allowing it to be accessed with an external AWS account that you control.
You leave the initial access behind and now have a sneaky Backdoor with admin permissions.
https://rootcat.de/blog/thecatflap
Abusing IDispatch for Trapped COM Object Access & Injecting into PPL Processes
Mohamed Fakroud details a techniques which we can expected to be leveraged in the AV/EDR disablement space..
This PoC demonstrates how the technique can bypass Protected Process Light (PPL) protection, highlighting the significant real-world implications of this vulnerability. It provides a powerful means of accessing critical protected processes, such as LSASS with LSA protection or a protected AV/EDR.
Exploitation
What is being exploited..
Nothing of note this week
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Baby Naptime
Faizan Ahmad (AI for Security at Meta) replicates and releases this
A very simple and basic open source implementation inspired by Google's Project Naptime - a vulnerability analysis tool that uses Large Language Models (LLMs) to discover and exploit native vulnerabilities.
https://github.com/faizann24/baby-naptime
Analysis at Scale with x64dbg Automate
Dariush Houle (Darbonzo) releases something which will have wide value..
thoughts and features behind x64dbg Automate, my automation solution for x64dbg. I designed this project with the goal of building on x64dbg’s command execution engine and plugin API to provide an expressive, modern, and easy to use Python client library. I use this project in a wide variety of malware analysis, reverse engineering, and vulnerability hunting tasks.
https://x64dbg.com/blog/2025/03/04/analysis-at-scale-with-x64dbg-automate.html
3FS
Deepseek released this, there will no doubt value in certain cyber defence use cases where a disaggregated architecture is useful due to volumes.
A high-performance distributed file system designed to address the challenges of AI training and inference workloads
https://github.com/deepseek-ai/3FS
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Cybersecurity Framework Profile for Semiconductor Manufacturing - initial public draft for comment.
Digital corporate autonomy: geo-economics and corporate agency in conflict and competition
Software Liability
Artificial intelligence
Books
Nothing of note this week
Events
NDSS 2025 papers - was held in San Diego, California, from 24th to 28th February 2025.
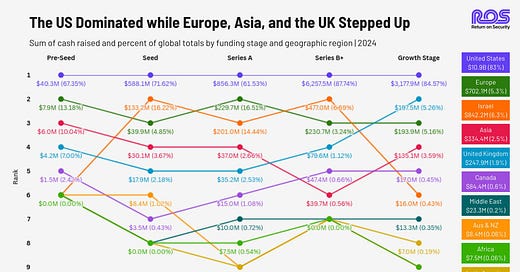
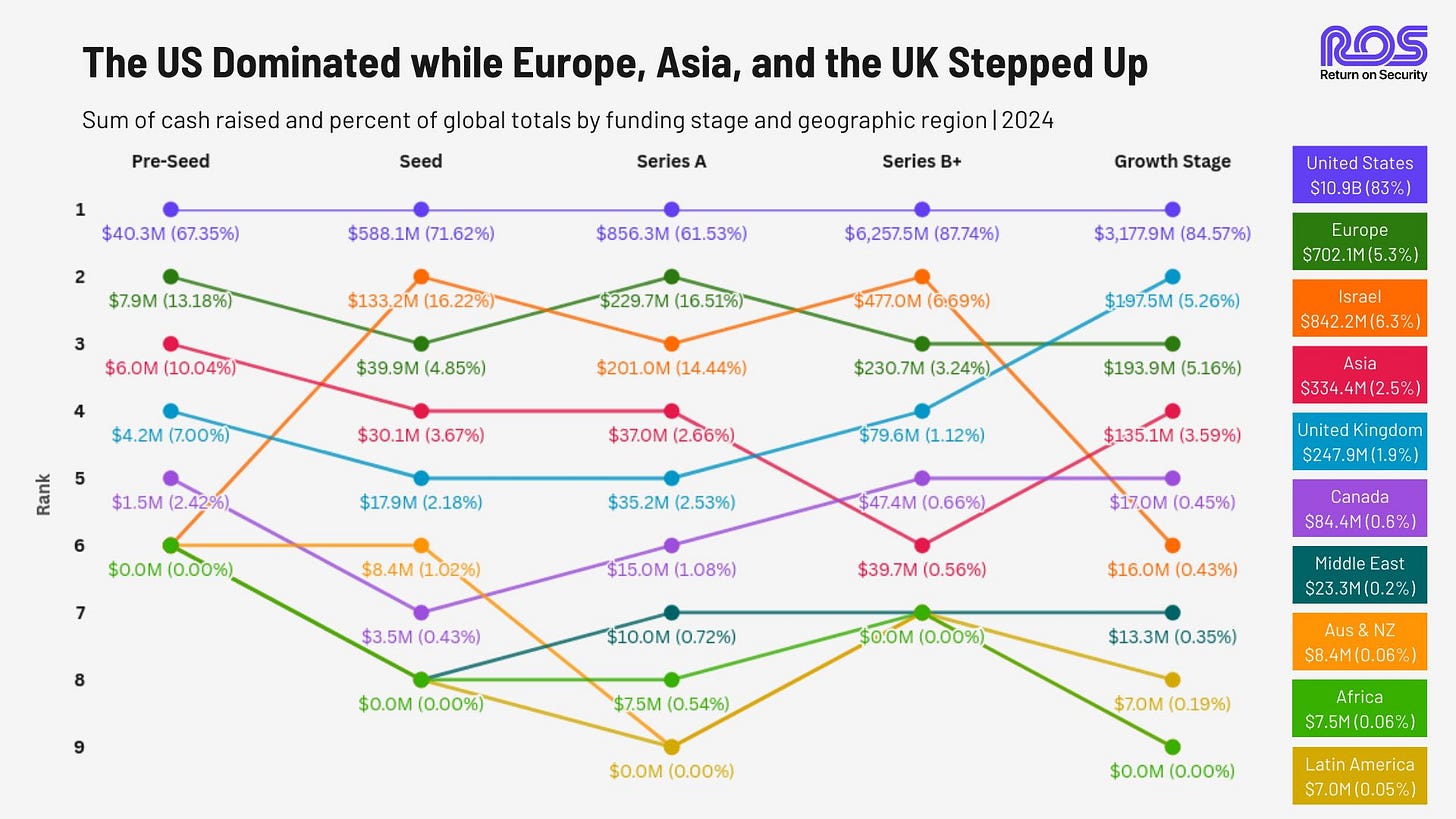
Finally graph of the week The Global Cybersecurity Funding Map - UK growth stage companies looking good!
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.