CTO at NCSC Summary: week ending March 2nd
Third-party risk—including ransomware attacks and vendor-related outages—accounted for 31% of all cyber insurance claims in 2024.
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note other than what looks like a thematic of telecommunications targeting in some of the reporting.
In the high-level this week:
India expands collaboration with UK in key areas of telecom, AI, and other emerging technologies - The Tribune reports - “Establishment of a Joint Centres of Excellence focusing on telecom cybersecurity, AI in telecom, and digital twins.”
Drones as a new cyber threat - How companies can protect themselves - German Federal Office for Information Security publishes - “The BSI is analyzing key threats that can be posed by drone payloads: They range from espionage and surveillance using optical or thermal imaging cameras to targeted hacker attacks on radio communications ( e.g. Wi-Fi , cell phones) and IT systems.”
Commission launches new cybersecurity blueprint to enhance EU cyber crisis coordination - European Union publishes - “The proposed blueprint updates the comprehensive EU framework for Cybersecurity Crisis Management and maps the relevant EU actors, outlining their roles throughout the entire crisis lifecycle. This includes preparedness and shared situational awareness to anticipate cyber incidents, and the necessary detection capabilities to identify them, including the response and recovery tools needed to mitigate, deter and contain those incidents”
ASIO Director-General's Annual Threat Assessment 2025 - ASIO publishes - “Cyber units from at least one nation state routinely try to explore and exploit Australia’s critical infrastructure networks, almost certainly mapping systems so they can lay down malware or maintain access in the future.”
Belgian intelligence loses private data to Chinese hackers - Brussels Times reports - “For nearly two years, a cyber-espionage operation linked to China's intelligence services exploited a vulnerability in an American cybersecurity firm's software, intercepting approximately 10% of all incoming and outgoing emails from Belgium’s State Security Service (VSSE), an investigation by Le Soir has revealed.”
Colombia’s National Position on the Application Of International
Law In Cyberspace - Colombia publishes - “In this context, States need to further develop their legal views on how sovereignty applies in the cyber context, particularly in instances involving multiple jurisdictions at play and where the territorial component is absent or complex.”
Securing tomorrow's software: the need for memory safety standards - Google asserts - “Looking forward, we're also seeing exciting and promising developments in hardware. Technologies like ARM's Memory Tagging Extension (MTE) and the Capability Hardware Enhanced RISC Instructions (CHERI) architecture offer a complementary defense, particularly for existing code.”
Reporting on/from China
A Policymaker’s Guide to China’s Technology Security Strategy - Information Technology & Innovation Foundation publishes - “China’s technology security policy has three prongs: 1) preserving and strengthening competitive advantages; 2) addressing sectors and endowments that are falling behind; and 3) gaining a pioneering edge in emerging technologies.”
China taps tech talent to boost AI data centre boom - Financial Times reports - “It shows how China is increasingly pooling resources from the private and state sectors — combining local government spending power with start-up tech talent — as part of a push to accelerate its network of AI computing infrastructure.”
Tech war: ex-Apple engineer returns to China to teach about semiconductors at alma mater - South China Morning Post reports - “A Chinese engineer who worked on semiconductors at Apple has returned home to teach at his alma mater in Wuhan, capital of central Hubei province, joining a wave of scientists and other tech talent to leave the United States.”
Chinese GPU Manufacturers Push Out Support For Running DeepSeek’s AI Models On Local Systems, Intensifying the AI Race - Wccf Tech publishes - “In addition, Baidu, the famous Chinese tech company, has built its in-house AI cluster featuring the Kunlun Core P800 AI chips. According to MyDrivers, the Core P800 performs 20-50% better than similar mainstream GPUs, supports 8-bit inference, and has significantly low deployment and maintenance costs.”
OpenAI Uncovers Evidence of A.I.-Powered Chinese Surveillance Tool - New York Times reports - “The company’s researchers said they had identified this new campaign, which they called Peer Review, because someone working on the tool used OpenAI’s technologies to debug some of the computer code that underpins it.”
AI
AI forecasting retrospective: you're (probably) over-confident - Nicholas Carlini asserts - “This overconfidence is consistent across all questions, and it really highlights a growing worry I have: almost everyone (even people who read my website!) appears overconfident about where things are going”
OCCULT: Evaluating Large Language Models for Offensive Cyber Operation Capabilities - The MITRE Corporation reports - “We detail OCCULT, a lightweight operational evaluation framework that allows cyber security experts to contribute to rigorous and repeatable measurement of the plausible cyber security risks associated with any given large language model (LLM) or AI employed for OCO. We also prototype and evaluate three very different OCO benchmarks for LLMs that demonstrate our approach and serve as examples for building benchmarks under the OCCULT framework.”
US Open-Source AI Governance Balancing Ideological and Geopolitical Considerations with China Competition - Center for AI Policy publishes - “DeepSeek’s December 2024 and January 2025 models demonstrated novel algorithmic innovations and impressive performance.”
Network architecture for global AI policy - Brookings comments - “Development of AI standards in global standards bodies is a key aspect of AI governance where broadening access for governments, industry, and civil society, especially in low- and middle-income countries, is needed to strengthen the legitimacy of these standards and ensure that the resulting standards respond to differing AI needs.”
Cyber proliferation
Italian priest close to pope told he was target of surveillance tool used by a government - The Guardian reports - “An Italian priest who has a close relationship with Pope Francis and was previously in telephone contact with him was notified he had been a target of a sophisticated surveillance tool used by a government, a revelation that will increase pressure on Giorgia Meloni’s government after other similar cases.”
Cellebrite suspends Serbia as customer after claims police used firm’s tech to plant spyware - Tech Crunch reports -”Cellebrite announced on Tuesday that it stopped Serbia from using its technology following allegations that Serbian police and intelligence used Cellebrite’s technology to unlock the phones of a journalist and an activist, and then plant spyware.”
Meta seeks to ban NSO Group from platforms after WhatsApp hack - Daily Journal reports - “Meta demands a permanent ban on NSO Group from its platforms, alleging the Israeli firm's Pegasus spyware hacked 1,400 WhatsApp users, sparking a heated legal battle.”
Cellebrite zero-day exploit used to target phone of Serbian student activist - Amnesty International Security Lab identifies - “These most recent findings show the ongoing harms from the continued misuse of Cellebrite’s advanced mobile phone extraction tools, even after widely published evidence of abuses. Since the exploits identified in this research target core Linux kernel USB drivers, the vulnerability is not limited to a particular device or vendor and could impact over a billion Android devices.”
Bounty Hunting
Disrupting a Global Cybercrime Network Abusing Generative AI - Microsoft litigates - “The individuals named are: (1) Arian Yadegarnia aka “Fiz” of Iran, (2) Alan Krysiak aka “Drago” of United Kingdom, (3) Ricky Yuen aka “cg-dot” of Hong Kong, China, and (4) Phát Phùng Tấn aka “Asakuri” of Vietnam. These actors are at the center of a global cybercrime network Microsoft tracks as Storm-2139.”
North Korea Responsible for $1.5 Billion Bybit Hack - FBI attributes - “The Federal Bureau of Investigation (FBI) is releasing this PSA (Public Service Announcement) to advise the Democratic People's Republic of Korea (North Korea) was responsible for the theft of approximately $1.5 billion USD in virtual assets from cryptocurrency exchange, Bybit, on or about February 21, 2025.”
Third-party risk emerges as key driver of cyber insurance claims & losses in 2024 - Reinsurance News reports - “Third-party risk—including ransomware attacks and vendor-related outages—accounted for 31% of all cyber insurance claims in 2024. Even more notably, third-party risk led to incurred losses for the first time ever, making up 23% of all incurred claims in 2024, compared to zero in 2023.”
Reflections this week are based on The state of AI (or Tensor-pwn) which highlights some of the soft underbelly of AI enabling frameworks. This in addition to another vulnerability discussed later.
If you are not technical take away is that common components widely in use have some security vulnerabilities that when combined to iterative approaches to development and integration mean there will a long tail of deployed vulnerability.
The vulnerabilities? Everything from code execution from untrusted models to falling back to clear-text from TLS connections on error..
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Targeted activity UAC-0212 against developers and suppliers of automation and process control solutions
CERT Ukraine details this alleged Russian operation which uses a mixture of n-days against a sector supporting freight and logistics. Nothing overly of note beyond the fact it happening the sector..
However, starting in the second half of 2024, new tactics, techniques, and procedures were observed, including sending the victim a PDF document with a link, visiting which, in combination with the exploitation of the CVE-2024-38213 vulnerability, resulted in the download of an LNK file (extension "pdf.lnk") to the computer, the launch of which resulted in the execution of a PowerShell command that ensured the download and display of the decoy document, as well as the download, persistence (the "Run" branch), and launch of EXE/DLL files.
Based on the results of a study of a number of related campaigns that took place between July 2024 and February 2025, the group carried out targeted attacks against supplier companies from Serbia, the Czech Republic, and Ukraine (note that the geography of the attack objects is much wider ). At the same time, during August 2024 alone, no less than twelve Ukrainian logistics companies specializing in freight transportation by road, air, and sea (including dangerous and perishable goods) were targeted .
https://cert.gov.ua/article/6282517
Ghostwriter | New Campaign Targets Ukrainian Government and Belarusian Opposition
Tom Hegel details an alleged Belarussian campaign which is interesting for its clustering around the use of Google’s infrastructure for the campaign.
SentinelLABS has observed a campaign targeting opposition activists in Belarus as well as Ukrainian military and government organizations.
The campaign has been in preparation since July-August 2024 and entered the active phase in November-December 2024.
Recent malware samples and command-and-control (C2) infrastructure activity indicate that the operation remains active in recent days.
…
SentinelLABS analyzed an attack that started with a Google Drive shared document landing in the target’s inbox. The email originated from an account using the name “Vladimir Nikiforech” (
vladimir.nikiforeach@gmail[.]com). The email link pointed to a downloadable RAR archive, which according to the internal timestamps was created on 2025-01-14 00:47:54, containing a malicious Excel workbook (ebb30fd99c2e6cbae392c337df5876759e53730d) with the file nameполитзаключенные(по судам минска).xls(“Political prisoners (across courts of Minsk).xls”).
Reporting on China
Chinese APT Target Royal Thai Police in Malware Campaign
Cado Security Labs details an alleged Chinese campaign which feels like an old penetration tester is driving with the use of ftp.exe. A technique I remember using back at the turn of the century..
The initial file is a rar archive named ด่วนมาก เชิญเข้าร่วมโครงการความร่วมมือฝึกอบรมหลักสูตร FBI.rar (English: Very urgent, please join the cooperation project to train the FBI course.rar). While the initial access is unknown, it is highly likely to have been delivered via phishing email. Inside the rar file is a LNK (shortcut) file ด่วนมาก เชิญเข้าร่วมโครงการความร่วมมือฝึกอบรมหลักสูตร FBI.docx.lnk, disguised PDF file and folder named $Recycle.bin.
The shortcut file executes ftp.exe (File Transfer Protocol), which then processes the commands inside the disguised PDF file as a FTP script. FTP scripts are automated scripts that execute a sequence of FTP commands.
https://www.cadosecurity.com/blog/chinese-apt-target-royal-thai-police-in-malware-campaign
Squidoor: Suspected Chinese Threat Actor’s Backdoor Targets Global Organizations
Lior Rochberger and Tom Fakterman detail an alleged Chinese campaign which is of note use the sectors being targeted in both Southeast Asia and South America i.e. telecommunications. Note the initial access is through Internet exposed infrastructure.
This article reviews a cluster of malicious activity that we identify as CL-STA-0049. Since at least March 2023, a suspected Chinese threat actor has targeted governments, defense, telecommunication, education and aviation sectors in Southeast Asia and South America.
The threat actor behind this activity cluster used a recently discovered sophisticated backdoor we named Squidoor (aka FinalDraft), which targets both Windows and Linux systems.
…
To gain access to networks, the threat actor behind CL-STA-0049 primarily attempted to exploit various vulnerabilities in Internet Information Services (IIS) servers.
https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/
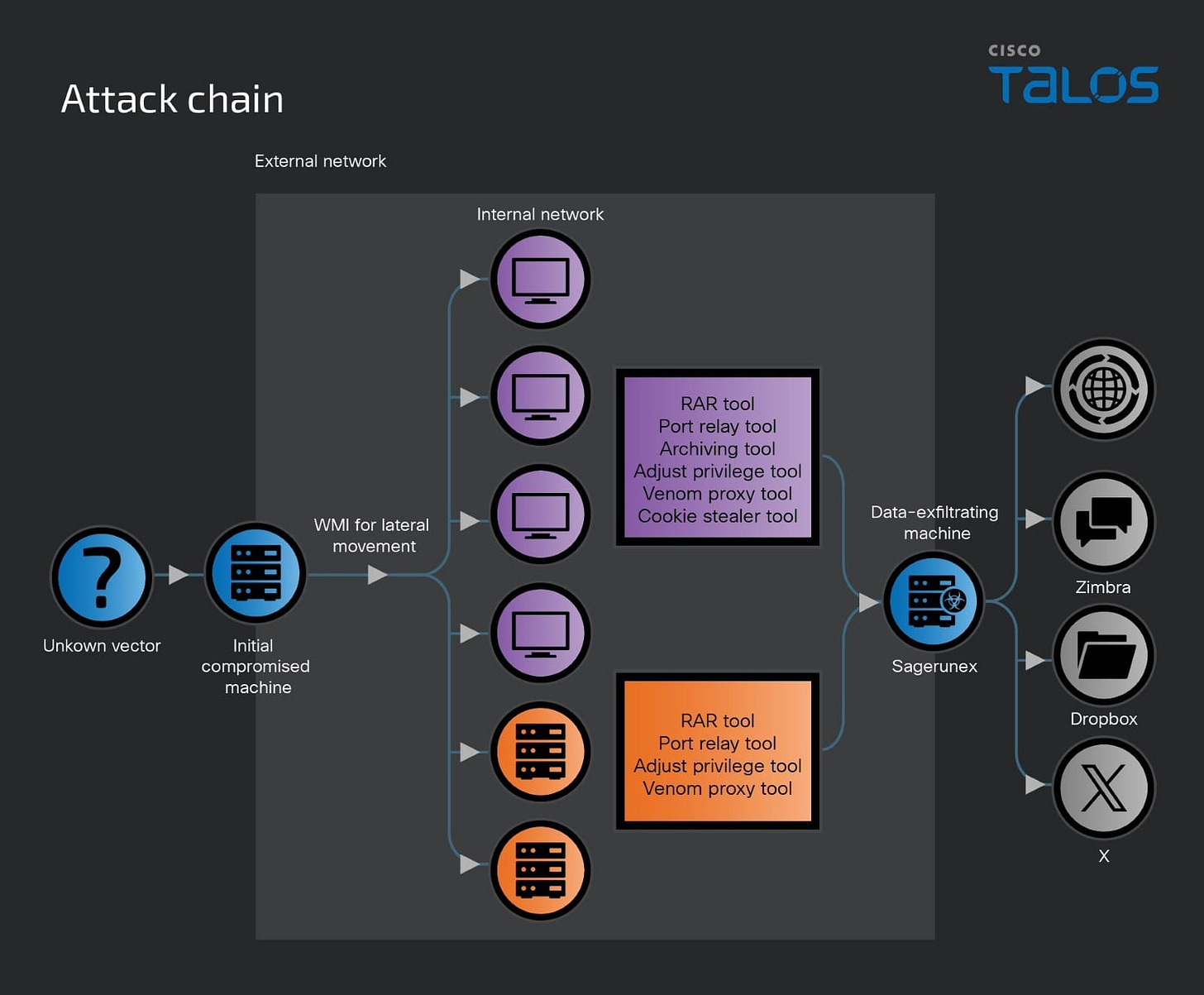
Lotus Blossom espionage group targets multiple industries with different versions of Sagerunex and hacking tools
Joey Chen details this alleged Chinese campaign. Noteworthy for the sectors being targeted i.e. telecommunications.
Cisco Talos discovered multiple cyber espionage campaigns that target government, manufacturing, telecommunications and media, delivering Sagerunex and other hacking tools for post-compromise activities.
Talos attributes these attacks to the threat actor known as Lotus Blossom. Lotus Blossom has actively conducted cyber espionage operations since at least 2012 and continues to operate today.
Based on our examination of the tactics, techniques, and procedures (TTPs) utilized in these campaigns, alongside the deployment of Sagerunex, a backdoor family used exclusively by Lotus Blossom, we attribute these campaigns to the Lotus Blossom group with high confidence.
We also observed Lotus Blossom gain persistence using specific commands to install their Sagerunex backdoor within the system registry and configuring it to run as a service on infected endpoints.
Lotus Blossom has also developed new variants of Sagerunex that not only use traditional command and control (C2) servers but also use legitimate, third-party cloud services such as Dropbox, Twitter, and the Zimbra open-source webmail as C2 tunnels.
https://blog.talosintelligence.com/lotus-blossom-espionage-group/
Reporting on North Korea
The Bybit Incident: When Research Meets Reality
Dikla Barda, Roman Ziakin and Oded Vanunu detail the alleged North Korean campaign which initially got away with $1.5 billion this week or about 15 F35s. I also suspect we aren’t at the bottom of the barrel for digital asset thefts by nation states.
In one of the largest thefts in digital asset history, hackers gained unauthorized access to a multisig Ethereum wallet and stole $1.5 billion worth of digital assets, primarily consisting of Ethereum tokens.
The recent incident with Bybit marks a new phase in attack methods, featuring advanced techniques for manipulating user interfaces. Rather than just targeting protocol flaws, the attackers used sophisticated infrastructure compromise to manipulate the UI that signers interacted with.
This past July, Check Point’s Threat Intelligence Blockchain system identified and published a concerning new findings where attackers manipulating legitimate transactions through the Safe Protocol’s execTransaction function.
The recent hack highlights that multisig cold wallets are not secure if signers can be deceived, emphasizing the growing sophistication of supply chain and user interface manipulation attacks.
The Bybit hack challenges previous beliefs about crypto security, showing that despite strong smart contracts and multisig protections, the human-interface layer remains vulnerable. This incident highlights how UI manipulation can compromise even the most secure wallets.
https://research.checkpoint.com/2025/the-bybit-incident-when-research-meets-reality/
Technical Analysis of the Bybit Hot Wallet Exploit by th13vn blog.verichains.io/p/technical-analysis-of-the-bybit-hot
Reporting on Other Actors
Silent Killers: Unmasking a Large-Scale Legacy Driver Exploitation Campaign
CPR detail a rather large campaign which is noteworthy for its use drivers, the scale of variants and the level of evasion on show..
CPR uncovered a large-scale ongoing campaign involving thousands of first-stage malicious samples used to deploy an EDR/AV killer module in its initial stage. This module was first detected and recorded in June 2024. It was observed leveraging and exploiting more than 2,500 distinct variants of the legacy version 2.0.2 of the known vulnerable driver Truesight.sys, which is the RogueKiller Antirootkit Driver and part of Adlice’s product suite. This driver has a known vulnerability in versions below 3.4.0.
The attackers exploited the legacy version 2.0.2 of the Truesight driver to take advantage of a Windows policy loophole (Exception in Driver Signing Policy), allowing the driver to be loaded on the latest versions of Windows OS. Notably, the attackers specifically selected the 2.0.2 version because it retains the vulnerable code while also bypassing the latest Microsoft Vulnerable Driver Blocklist and common detection mechanisms, such as those introduced by the LOLDrivers project, none of which detect this version.
To further evade detection, the attackers deliberately generated multiple variants (with different hashes) of the 2.0.2 driver by modifying specific PE parts while keeping the signature valid. We detected over 2,500 validly signed variants of this driver.
The attackers leveraged infrastructure in a public cloud’s China region to host payloads and operate their C2 servers. Around 75% of the victims are located in China, while the remainder come from other parts of Asia (e.g., Singapore, Taiwan).
The initial-stage samples act as downloaders/loaders and often disguise themselves as well-known applications. They are typically distributed via phishing methods, including deceptive websites and phishing channels in messaging apps. Along with the EDR/AV killer module, they are designed to prepare the infected machine to deliver final-stage payloads, such as Gh0st RAT variants.
CPR reported this issue to MSRC, leading to an updated version of the Microsoft Vulnerable Driver Blocklist (available since December 17, 2024), effectively preventing all variants of the legacy driver exploited in this campaign.
https://research.checkpoint.com/2025/large-scale-exploitation-of-legacy-driver/
Auto-Color: An Emerging and Evasive Linux Backdoor
Alex Armstrong details a new Linux implant which feels like a Phrack article in the wild.
Using benign-looking file names for operating
Hiding remote command and control (C2) connections using an advanced technique similar to the one used by the Symbiote malware family
Deploying proprietary encryption algorithms to hide communication and configuration information
https://unit42.paloaltonetworks.com/new-linux-backdoor-auto-color/
Malicious browser extensions impacting at least 3.2 million users
GitLab Threat Intelligence details a campaign which is interesting because of the potential access to the extensions via their original developers. Noteworthy for the software supply chain for a whole host of reasons.
We identified a cluster of at least 16 malicious Chrome extensions used to inject code into browsers to facilitate advertising and search engine optimization fraud. The extensions span diverse functionality including screen capture, ad blocking and emoji keyboards and impact at least 3.2 million users.
We assess that the threat actor acquired access to at least some of the extensions from their original developers, rather than through a compromise. The threat actor has been trojanizing extensions since at least July 2024.
The threat actor uses a complex multistage attack to degrade the security of users’ browsers and then inject content, traversing browser security boundaries and hiding malicious code outside of extensions. We have only been able to partly reproduce the threat actor’s attack chain.
The threat actor may also be associated with phishing kit development or distribution. The malicious extensions present a risk of sensitive information leakage or initial access.
Discovery
How we find and understand the latent compromises within our environments.
100 Days of KQL
Aura dons their cape for another week:
Tracking Trusted Office Documents: A Key to Investigating Macro-Based Malware
Dean provides a technique which will potentially help find latent compromises which used this technique. The start of the breadcrumb trail..
Microsoft Office maintains a TrustRecords registry key that logs this information. This key provides a long-term record of what documents were trusted, where they were stored, and when the user enabled macros or editing.
OneDrive Microsoft.FileUsageSync.db
Brian Maloney provides a forensics artefact which might be useful. I have seen compromises which start with implants coming down via OneDrive (when the O365 account was compromised).
I recently started to look into the Microsoft.FileUsageSync.db. The database can be found in
%localappdata%\Microsoft\OneDrive\ListSync\Business<1-9>\settings. It is not documented in OneDrive Evolution because it only appears in OneDrive for Business. OneDrive Evolution's data is collected from personal only. It's not known what version this database first appeared in. Just like Microsoft.ListSync.db, this database is used by Microsoft.SharePoint.exe but is not related to the Offline Mode for web feature that I am aware of
https://malwaremaloney.blogspot.com/2025/02/onedrive-microsoftfileusagesyncdb.html
Registration Data Access Protocol (RDAP)
ICANN document this which will be useful.
The Registration Data Access Protocol (RDAP) enables users to access current registration data and was created as an eventual replacement for the WHOIS protocol. RDAP was developed by the technical community in the Internet Engineering Task Force (IETF).
RDAP is a protocol that delivers registration data like WHOIS, but its implementation will change and standardize data access and query response formats. RDAP has several advantages over the WHOIS protocol, including support for internationalization, secure access to data, and the ability to provide differentiated access to registration data.
Defence
How we proactively defend our environments.
From log analysis to rule creation: How AWS Network Firewall automates domain-based security for outbound traffic
Mary Kay Sondecker, Jason Goode, Jesse Lepich, and Michael Leighty details a specific AWS technique which will be of use to some.
AWS Network Firewall automated domain lists improve visibility into network traffic patterns and simplify outbound traffic control management. This feature provides analytics for HTTP and HTTPS network traffic, helping organizations understand domain usage patterns. It also automates firewall log analysis to create rules based on your network traffic. By combining increased visibility with automation, this feature enhances your security awareness and helps to improve the effectiveness of your firewall rules.
Incident Writeups & Disclosures
How they got in and what they did.
Confluence Exploit Leads to LockBit Ransomware
The DFIR Report detail the end to end compromise..
The intrusion began with the exploitation of CVE-2023-22527 on an exposed Windows Confluence server, ultimately leading to the deployment of LockBit ransomware across the environment.
The threat actor leveraged various tools, including Mimikatz, Metasploit, and AnyDesk.
The threat actor leveraged RDP for lateral movement, deploying LockBit ransomware through multiple methods, including copying files over SMB shares for remote execution and automated distribution via PDQ Deploy.
Sensitive data was exfiltrated using Rclone, transferring files to MEGA.io cloud storage.
The intrusion had a rapid Time to Ransom (TTR) of around just two hours.
https://thedfirreport.com/2025/02/24/confluence-exploit-leads-to-lockbit-ransomware/
Vulnerability
Our attack surface.
Smoltalk: RCE in open source agents
Josh Merrill evidences that AI infrastructure has vulnerabilities.. news at 11.
I discovered a vulnerability in its [smolagents] implementation, allowing an attacker to escape the interpreter and execute commands on the underlying machine. Here we will take a walk through the analysis of the exploit and discuss the implication this has as a microcosm to AI agent security.
https://securityintelligence.com/x-force/smoltalk-rce-in-open-source-agents/
CVE-2025-27090: SSRF on Sliver C2 teamserver via spoofed implant callback
Chebuya details a vulnerability that few will be able to use legally, but those than can will have impact..
I was able to discover a vulnerability in which attackers could open a TCP connection on the teamserver to an arbitrary IP/port, and read and write traffic through the socket (a powerful form of SSRF). The consequences of exploiting this vulnerability could be anything from leaking teamserver IPs behind redirectors to moving laterally from the teamserver to other services.
https://blog.chebuya.com/posts/server-side-request-forgery-on-sliver-c2/
Offense
Attack capability, techniques and trade-craft.
Fingerprint Heists
Pavel Naumo, Dmitry Pisarev, Dmitrii Yankelevich and Giovanni Barbieri detail an aspect which is interesting as it evidences the continued arms race.
Advanced Fingerprinting Techniques: Cybercriminals exploit sophisticated methods to extract unique browser characteristics without user consent.
Identified malicious campaign collecting fingerprints of unaware users: a threat actor is compromising Magento websites to inject malicious code aimed at collecting the fingerprints of visiting users.
To automate the process and avoid detection fraudsters can use different tools. By leveraging these capabilities attackers can test thousands of stolen username-password pairs against multiple websites without triggering traditional security mechanisms. Fingerprinting spoofing ensures their requests appear as legitimate user activity, bypassing detection.
https://www.group-ib.com/blog/fingerprint-heists/
FindGPPPasswords
Rémi GASCOU provides a tool which will be like a hot knife through butter for some environments..
A cross-platforms tool to find and decrypt Group Policy Preferences passwords from the SYSVOL share using low-privileged domain accounts.
https://github.com/p0dalirius/FindGPPPasswords
implant.js
Zander Work releases an impact framework which is worth being aware of..
Proof-of-concept modular implant platform leveraging v8
https://github.com/captainGeech42/implant.js
Abusing VBS Enclaves to Create Evasive Malware
Ori David details a set of techniques which although unlikely to be used in the short term do provide opportunity for misuse.
While enclaves can help secure systems, they can also be very appealing to attackers — a piece of malware that manages to run inside an enclave can be potentially invisible to memory-based detection and forensics.
We set out to explore VBS enclaves and understand how they could be used for malicious purposes, and this blog post will detail our key findings. We’ll dive into VBS enclaves by exploring previously undocumented behaviors, describing the different scenarios that can enable attackers to run malicious code inside them, and examining the various techniques “enclave malware” can use.
We’ll also introduce Mirage, a memory evasion technique based on a new approach that we dubbed “Bring your own vulnerable enclave.” We’ll explore how attackers can use old, vulnerable versions of legitimate enclaves to implement this stealthy evasion technique.
https://www.akamai.com/blog/security-research/2025-february-abusing-vbs-enclaves-evasive-malware
Exploitation
What is being exploited..
Wallbleed: A Memory Disclosure Vulnerability in the Great Firewall of China
Shencha Fan, Jackson Sippe, Sakamoto San, Jade Sheffey, David Fifield, Amir Houmansadr, Elson Wedwards and Eric Wustrow interpret the law to allow them to undertake this research..
We present Wallbleed, a buffer over-read vulnerability that existed in the DNS injection subsystem of the Great Firewall of China. Wallbleed caused certain nation-wide censorship middleboxes to reveal up to 125 bytes of their memory when censoring a crafted DNS query. It afforded a rare insight into one of the Great Firewall’s well-known network attacks, namely DNS injection, in terms of its internal architecture and the censor’s operational behaviors.
To understand the causes and implications of Wallbleed, we conducted longitudinal and Internet-wide measurements for over two years from October 2021.
https://gfw.report/publications/ndss25/en/
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Unpacking Pyarmor v8+ scripts
Leonard Rapp and Hendrik Eckardt shows how to pull it off.
Pyarmor is a product for protecting Python scripts from reverse engineering. It also offers licensing features, such as binding scripts to specific hardware or outfitting scripts with a kill date. Sadly, as is often the case with such products, it is also occasionally abused by malware in order to hide malicious code.
https://cyber.wtf/2025/02/12/unpacking-pyarmor-v8-scripts/
Introduction to eBPF for Windows
Pavel Yosifovich walks through how to get started..
https://scorpiosoftware.net/2025/02/22/introduction-to-ebpf-for-windows/
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Memory Safety Will Be Key to Tackle Fundamental Cyber Security
Spatial-Domain Wireless Jamming with Reconfigurable Intelligent Surfaces - beam forming to within 5mm of the receiver - this is precision!
Artificial intelligence
The state of AI - a research repository of vulnerabilities and similar
Performance of Zero-Shot Time Series Foundation Models on Cloud Data
Books
Events
JSAC2025 Event Report, day 1 - a look back
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.