Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note..
In the high-level this week:
Facing the cyber threat behind the headlines - UK NCSC publishes - “NCSC CEO urges all businesses to face the stark reality of the cyber threat they face, whether in the spotlight or not.”
UK and allies expose Russian intelligence campaign targeting western logistics and technology organisations - UK NCSC with allies publishes - “GRU Unit 26165’s malicious activity includes credential guessing, spear-phishing and exploiting Microsoft Exchange mailbox permissions, as well as targeting internet-connected cameras at Ukrainian border crossings and near military installations.”
New ETSI standard protects AI systems from evolving cyber threats - UK NCSC details - “The standard defines 13 core security principles grouped into 5 key stages within the AI system development life cycle. These are:
secure design
secure development
secure deployment
secure maintenance
secure end of life”
Cyber security charter - letter to supplier CEOs - NHS publishes - “This is an open letter to all current, potential or aspiring suppliers to the NHS, to highlight the growing and ever-changing cyber security threat level that we collectively face. The severity of incidents, and increasing frequency, has demonstrated a step change in recent months.” - market incentives in action
“This is a copy of a letter sent to CEOs of suppliers to the NHS, asking them to sign our charter of cyber security best practice.”
Business and Trade Sub-Committee on Economic Security, Arms and Export Controls - Parliament publishes - an industry panel looking emerging technology and cyber security in the context of economic security.
Research indicates online threats cost New Zealanders $1.6 billion in 2024 - NZ NCSC publishes - “It is encouraging to see so many people engaged in new cyber security behaviour,” Mr Jagusch said. These behaviours include using two-factor authentication on main accounts, changing default passwords on devices like Wi-Fi routers, and using a password manager.”
New Japan law allows preemptive defense of infrastructure cyberattack - Kyodo News reports - “Under the measures, police will take initial responsibility for neutralizing an attacker's server and the Self-Defense Forces will step in if an incident is deemed particularly sophisticated, organized and premeditated.”
Japan enacts new Active Cyberdefense Law allowing for offensive cyber operations - The Record reports - “It explicitly allows law enforcement agencies to infiltrate and neutralize hostile servers before any malicious activity has taken place and to do so below the level of an armed attack against Japan”
Counting the costs: A cybersecurity metrics framework for policy - Atlantic Council publishes - “The report then explores the current limitations of available metrics, illustrating how wide-ranging estimates of incident costs and inconsistent data collection methods hamstring policymakers. It outlines the difficulty of measuring and interpreting harm data at scale due to factors such as silent failures, complex indirect costs, and underreporting, but it argues that such challenges are not insurmountable and that a desire for perfect metrics cannot impede progress toward better ones.”
Taiwan boosts smart robotics industry with $664m plan - Tech in Asia reports - “The initiative aims to increase the production value of professional service robots from NT$4 billion (US$132.47 million) to NT$50 billion (US$1.66 billion) over the next five years.” - flagging this due the rise of cyber physical systems in the guise of robotics - this is marching on literately at pace..
NTIA Should Fully Incorporate Cybersecurity and Interoperability Practices - U.S. Government Accountability Office publishes - “NTIA is working to modernize its spectrum management IT systems but hasn't fully followed leading practices for doing so. For example, it hasn't completed an organization-wide risk assessment. This, and other practices, would enable NTIA to identify, track, mitigate, and reduce cybersecurity risks and more.”
27 mil. user records leaked in SK Telecom data breach - Korea Times reports - “The leaked data amounts to 9.82 gigabytes and includes 26.95 million records, primarily containing International Mobile Subscriber Identity (IMSI) data — a critical identifier used to authenticate users on mobile networks… However, they added that the malware was first installed on June 15, 2022”
Cyber Breach Daily Briefing May 19 - SK Telecom publishes
More forms of espionage punishable - AIVD announces - “Due to the rise of digital espionage, computer crimes can also be punished more severely if they are committed for a foreign government. For example, hacking a computer system.”
Vyacheslav Volodin spoke about the adopted law, which provides for additional mechanisms for registering migrants - Russian State Duma reports - “the amendment proposed by the deputies introduces for foreign citizens … monitoring the geolocation of subscriber devices.”
Intel aims to overtake Samsung in contract chipmaking. TSMC might help - Nikkei Asia reports - “Intel laid out four foundry business models at the event, including one that allows customers to choose Intel for only the packaging process -- after testing and assembly are carried out by other foundries.”
Reporting on/from China
China’s lack of advanced chips hinders adoption of AI models: Tencent executive - South China Morning Post reports - Wang said he expected the tightened trade controls to “widen the gap [regarding AI adoption] between China and the US in the short term”.
Nvidia plans Shanghai research centre in new commitment to China - Financial Times reports - “According to people with knowledge of the plans, the R&D centre would research the specific demands of Chinese customers and the complex technical requirements needed to satisfy Washington’s curbs.”
China makes first 5G satellite-to-phone video call. Will it defy TikTok curbs? - South China Morning Post reports - “The test was carried out earlier this month using a new technology demonstration satellite, according to Liang Baojun, head of China Satellite Network Group (China SatNet). The state-owned company manages the country’s planned 13,000-satellite Guowang internet megaconstellation”
AI
AI Data Security: Best Practices for Securing Data Used to Train & Operate AI Systems - CISA and allies publish - “This guidance highlights the critical role of data security in ensuring the accuracy, integrity, and trustworthiness of AI outcomes. It outlines key risks that may arise from data security and integrity issues across all phases of the AI lifecycle, from development and testing to deployment and operation.”
Remote Prompt Injection in GitLab Duo Leads to Source Code Theft - Omer Mayraz publishes - a detailed walk through showing the impact of AI system exploitation in 2025
How I used o3 to find CVE-2025-37899, a remote zeroday vulnerability in the Linux kernel’s SMB implementation - Sean Heelan publishes - a walk through on how AI augments humans in vulnerability research - “o3 finds the kerberos authentication vulnerability in 1 out of 100 runs with this larger number of input tokens, so a clear drop in performance, but it does still find it… Reading this report I felt my expectations shift on how helpful AI tools are going to be in vulnerability research. If we were to never progress beyond what o3 can do right now, it would still make sense for everyone working in VR to figure out what parts of their work-flow will benefit from it, and to build the tooling to wire it in.”
Taxonomy of Prompt Injection Methods - Pangea publishes - a poster..
Assuring an accurate research record - MIT discloses - “Following the posting of the preprint paper “Artificial Intelligence, Scientific Discovery, and Product Innovation” on arXiv in November 2024, concerns were raised about the integrity of the research. MIT conducted an internal, confidential review and concluded that the paper should be withdrawn from public discourse.”
Power Hungry - MIT Technology Review publishes - “Data centers in the US used somewhere around 200 terawatt-hours of electricity in 2024, roughly what it takes to power Thailand for a year.”
Forensics tool ‘reanimates’ the ‘brains’ of AIs that fail in order to understand what went wrong - “AI Psychiatry takes in as input a memory image, a snapshot of the bits and bytes loaded when the AI was operational. The memory image at the time of the crash in the autonomous vehicle scenario holds crucial clues about the internal state and decision-making processes of the AI controlling the vehicle.”
Extending Minds with Generative AI - Nature Communications publishes -”there is suggestive evidence that what we are mostly seeing are alterations to the human-involving creative process rather than simple replacements. For example, a study of human Go players revealed increasing novelty in human-generated moves following the emergence of ‘superhuman AI Go strategies’"
Providing legal guarantees for the high-quality development and high-level security of artificial intelligence - People’s Daily broadcasts -”Promote AI education at all levels and general education for the whole society. Empowering the high-quality development of the private economy with the advantages of talent resources”
Cyber proliferation
Pegasus spyware maker rebuffed in efforts to get off trade blacklist - Washington Post reports - “The Trump administration will not seek the removal of Israeli tech firm NSO Group from a Commerce Department trade blacklist that has significantly dented the company’s financial fortunes, U.S. officials said this week.”
How the Pall Mall Process Can Help Combat Commercial Spyware Abuse - Freedom House publishes -”Additionally, governments rely on civil society and academic research that exposes the abuse of commercial spyware. To facilitate greater information sharing, civil society groups should release reporting on CCIC-facilitated human rights violations, with information presented in a way that is tailored to government audiences.”
Bounty Hunting
Justice Department Seizes Domains Behind Major Information-Stealing Malware Operation - US Department of Justice announces - “As alleged in the affidavits filed in support of the government’s seizure warrants, the administrators of LummaC2 used the seized websites to distribute LummaC2, an information-stealing malware, to their affiliates and other cyber criminals.”
Full Year Results for the 52 Weeks Ended 29 March 2025 - M&S publish - “our current estimate before mitigation is an impact on Group operating profit of around £300m for 2025/26, which will be reduced through management of costs, insurance and other trading actions. It is expected that costs directly relating to the incident will be presented separately as an adjusting item.”
Brief reflection this week is around AI cyber security optimism. At NCSC we see that AI will be a net positive for cyber security. However we see the path between where we are today and this end state of net positivity to be a rocky and uneven one.
Along this journey there will be some cyber defensive wins, but also some cyber offensive losses… but in the long term we will net out positive..
Not getting this via email? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Unpacking Russia’s cyber nesting doll
Justin Sherman breaks down the Russian system as he understands it..
Lessons from cyber operations—and about cyber operations and capabilities—from the Russian full-on war against Ukraine will continue to emerge in the coming years. This trickle of information may slowly dissipate some of the “fog of war” surrounding the back-and-forth hacks and shed much-needed light on issues such as coordination and conflict between Russian security agencies in cyberspace.
https://www.atlanticcouncil.org/content-series/russia-tomorrow/unpacking-russias-cyber-nesting-doll/
Russia-Aligned TAG-110 Targets Tajikistan with Macro-Enabled Word Templates
Insikt GroupⓇ details an alleged Russian operation which uses extremely basic tradecraft. The victimology is noteworthy..
TAG-110 has changed its spearphishing tactics in recent campaigns against Tajikistan, as they now rely on macro-enabled Word templates (.dotm files).
This campaign has been attributed to TAG=110 based on its reuse of VBA code found in lures from previous campaigns, overlap in C2 infrastructure, and use of suspected legitimate government documents for lure material.
TAG-110ʼs persistent targeting of Tajik government, educational, and research institutions supports Russiaʼs strategy to maintain influence in Central Asia. These cyber-espionage operations likely aim to gather intelligence for influencing regional politics or security, particularly during sensitive events like elections or geopolitical tensions.
TAG-110ʼs recent use of macro-enabled Word templates (.dotm), placed in the Microsoft Word STARTUP folder for automatic execution, highlights a tactical evolution prioritizing persistence. Organizations should monitor the Word STARTUP directory for unauthorized additions and enforce strict macro security policies.
https://go.recordedfuture.com/hubfs/reports/cta-2025-0522.pdf
Reporting on China
China-Nexus Threat Actor Actively Exploiting Ivanti Endpoint Manager Mobile Vulnerability
Arda Büyükkaya details alleged Chinese exploitation of this vulnerability. The pace with which the vulnerability was exploited after the vendor disclosed is of note as is the breadth of victims.
The earliest observed exploitation activity dates back to May 15, 2025. Targeted organizations span critical sectors including healthcare, telecommunications, aviation, municipal government, finance, and defense across Europe, North America, and the Asia-Pacific region.
..
UNC5221 demonstrates a deep understanding of EPMM’s internal architecture, repurposing legitimate system components for covert data exfiltration. This includes the extraction of large volumes of personally identifiable information (PII), authentication credentials, and other sensitive data used for lateral movement within compromised environments.
Reporting on North Korea
CJ OliveNetworks' digital certificate leaked in suspected N. Korean cyberattack
Yna reports on X-derived intelligence that a code signing certificate was compromised and then used to codesign an alleged North Korean implant. Not overly novel, but noteworthy nevertheless given the benefit that signed code gives.
A digital certificate belonging to CJ OliveNetworks Co., the IT service arm of South Korea's CJ Group, has been found to have been leaked and exploited in a suspected North Korean cyberattack, according to cybersecurity sources Wednesday.
According to the sources, a malicious file linked to North Korea discovered late last month was found to contain a digital certificate issued by CJ OliveNetworks.
https://m-en.yna.co.kr/view/AEN20250507006600320
Saja DPRK Employment Scam Network
Nisos details an interesting alleged North Korean fake IT worker sub campaign which poses as Polish individuals. The concern is that there is so much demand for development resource that such a concerted campaign risks just lucking out in terms of where it lands.
[We are] tracking an IT worker employment scam network posing as Polish and US nationals with the goal of obtaining employment in remote engineering and full-stack blockchain developer roles. Threat actors in this network are using GitHub accounts, portfolio websites, freelancer accounts, and a global freelance software development company, Inspiration With Digital Living (IWDL), to trick companies into hiring them for full-time remote positions and project-based freelance jobs. This network is the first indication that possibly DPRK-affiliated IT workers are setting up fake freelance software development companies with legitimate looking websites to gain freelancer work.
https://nisos.com/research/saja-dprk-employment-scam/
Reporting on Iran
Nothing overly of note this week..
Reporting on Other Actors
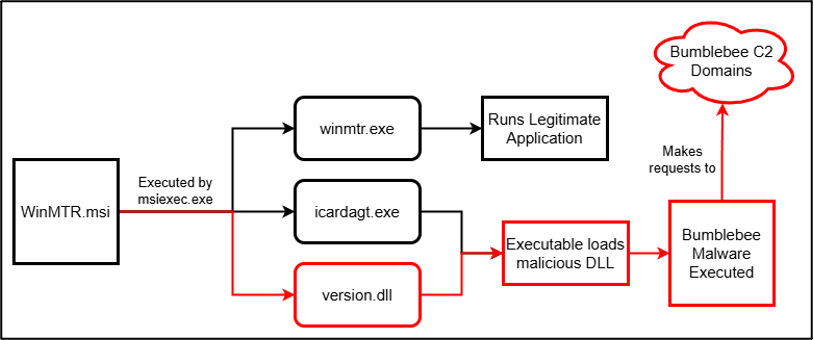
RVTools Supply Chain Attack Delivers Bumblebee Malware
Andres Ramos alerts to a criminal supply chain attack. Noteworthy as it required them to build a malicious installer. This is criminal.. let that sink in..
While the exact timeline of the compromise is unknown, reports of the malicious installer began emerging in mid-May 2025. At the time of writing, both legitimate RVTools sites (Robware.net and RVTools.com) are down, with no indication of when they will be restored.
Once the malicious installer was downloaded, the installer attempts to make outbound connections to known command and control infrastructure. However, the attempts were intercepted and sinkholed, preventing additional analysis on the final payload.
https://arcticwolf.com/resources/blog/rvtools-supply-chain-attack-delivers-bumblebee-malware/
Joe Wrieden reports on the same incident with more technical detail:
Cloudy with a Chance of Hijacking Forgotten DNS Records Enable Scam Actor
Jacques Portal and Renée Burton highlight once again that it is always DNS. Joking aside the attack surface here is clearly material..
The hijacked domains are used to host large numbers of URLs that send users to scams and malware by way of different traffic distribution systems (TDSs). This actor came to our attention after successfully gaining control of subdomains of the U.S. Center for Disease Control (CDC) in February 2025.
Discovery
How we find and understand the latent compromises within our environments.
Live Forensic Collection from Ivanti EPMM Appliances (CVE-2025-4427 & CVE-2025-4428)
Jonathan Haldarov and Carl Breindel walk through how to do a forensic acquisition of these devices. In short it involves getting SSH and running UAC. But it highlights once again why vendors must implement our Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances
UAC (Unix-like Artifact Collector) is a lightweight, open-source forensic triage tool used to gather logs, configuration, system state, and activity timelines from Unix systems.
https://profero.io/blog/ivanti-epmm-attacks
Misbehaving Modalities: Detecting Tools, Not Techniques
John Uhlmann builds on this concept with some specifics..
For modality-based detection approaches, the value becomes apparent when we baseline all expected low-level telemetry for a given modality - and trigger on any deviations.
Historically, attackers have been able to choose modality for convenience. It is more cost effective to write tools in C# or PowerShell than in C or assembly. If we can herd modality then we’ve imposed cost.
https://www.elastic.co/security-labs/misbehaving-modalities
Scarcity signals: Are rare activities red flags?
Darin Smith shows the power of some good old data science in detection engineering..
Cisco Talos reviewed six months of network connection telemetry logs spanning June 1, 2024 – Dec. 31, 2024, containing 3,220,829 log events and 742 unique base domains, to explore if domains that PowerShell rarely contacts are more likely to be malicious.
Key findings reveal that the odds of a rare domain being malicious were 3.18 times higher than for frequently contacted domains (95% CI: 0.39–25.9), suggesting a trend towards higher risk in rare domains.
Notably, the non-rare domain ‘githubusercontent.com’ was flagged as malicious due to activity from its subdomain ‘raw.githubusercontent.com’. This is an example of why subdomains should be considered when looking for malicious network traffic, especially for cloud services where the service itself is legitimate, but the content hosted on it is not guaranteed to be.
https://blog.talosintelligence.com/scarcity-signals-are-rare-activities-red-flags/
Palo Alto’s WildFire antivirus solution saves its detections in a temporary file
Stephan Berger details this fact which is useful for variety of cyber defence use cases.
Can collect WildFire detections by using a simple file pattern like this: C:\Windows\Temp\PAN[A-Z0-9]{4}.tmp
The file contains details such as the reason for the detection, timestamps, and hash values.
Defence
How we proactively defend our environments.
Enhance your application security with administrator protection
Microsoft publish..
Administrator protection is a new Windows 11 platform security feature that aims to protect the admin users on the device while still allowing them to perform the necessary functions which may require use of admin level permissions.
..
New security boundary with separate profile: Administrator protection uses a hidden, system-managed, profile-separated local user account to create the isolated admin token. This helps ensure that user-level malware cannot access and compromise the code running in the elevated context, thus making elevation a security boundary. Application developers please note: This System Managed Administrator Account (SMAA) has a different security identifier (SID).
Just-in-time admin token: The admin token which is required to perform system tasks is generated from SMAA. This token is non-persistent and created just in time to perform elevation and is discarded once the task is completed. The whole cycle repeats itself when the user tries to perform another task which requires admin privileges.
Removal of auto-elevation: Auto-elevation refers to allowing certain Windows processes and applications to automatically gain elevated privileges without prompting the user to consent. This can be exploited to perform User Access Control (UAC) bypass attacks where malware may misuse admin privileges to install an unwanted application on the device or for changing device security configuration thus compromising the security. With administrator protection, all auto-elevations in Windows are removed and users need to interactively authorize every admin operation. This helps ensure that the user stays in full control and that admin privileges are not abused.
Windows Hello integration: Administrator protection is recommended to be used in conjunction with Windows Hello. This further enhances security while providing a convenient authentication experience with face, fingerprint or PIN.
Likely Exploited Vulnerabilities: A Proposed Metric for Vulnerability Exploitation Probability
NIST and CISA publish..
This work presents a proposed security metric to determine the likelihood that a vulnerability has been observed to be exploited. Only a small fraction of the tens of thousands of software and hardware vulnerabilities that are published every year will be exploited. Predicting which ones is important for the efficiency and cost effectiveness of enterprise vulnerability remediation efforts. Currently, such remediation efforts rely on the Exploit Prediction Scoring System (EPSS), which has known inaccurate values, and Known Exploited Vulnerability (KEV) lists, which may not be comprehensive. The proposed likelihood metric may augment EPSS remediation (correcting some inaccuracies) and KEV lists (enabling measurements of comprehensiveness). However, collaboration with industry is necessary to provide necessary performance measurements.
https://csrc.nist.gov/pubs/cswp/41/likely-exploited-vulnerabilities-a-proposed-metric/final
Incident Writeups & Disclosures
How they got in and what they did.
LND Security Breach Post Mortem
LND details what went down..
On May 9, 2025, LND experienced a security breach that led to the unauthorized transfer of approximately $1.27 million USD. The incident was traced to a developer unknowingly hired by the team whom turned out to be a undercover DPRK IT worker. This individual/team unlawfully accessed the project’s administrative keys and executed a series of unauthorized transactions.
..
The stolen funds have since been bridged across multiple networks, and our security team continues to actively monitor and trace their movement.
https://medium.com/@lndfi/lnd-security-breach-post-mortem-2c54ac006050
Vulnerability
Our attack surface.
elf: static setuid binary dlopen may incorrectly search LD_LIBRARY_PATH
Carlos O'Donell details an unexpected vulnerability..
A statically linked setuid binary that calls dlopen (including internal dlopen calls after setlocale or calls to NSS functions such as getaddrinfo) may incorrectly search LD_LIBRARY_PATH to determine which library to load, leading to the execution of library code that is attacker controlled.
The only viable vector for exploitation of this bug is local, if a static setuid program exists, and that program calls dlopen, then it may search LD_LIBRARY_PATH to locate the SONAME to load. No such program has been discovered at the time of publishing this advisory, but the presence of custom setuid programs, although strongly discouraged as a security practice, cannot be discounted.
https://sourceware.org/cgit/glibc/tree/advisories/GLIBC-SA-2025-0002
There is also some interesting further detail / root cause analysis in this post:
https://www.openwall.com/lists/oss-security/2025/05/17/2
SAML Signature Wrapping attack
Yep, less than ideal..
A Signature Wrapping attack has been found in samlify <v2.10.0, allowing an attacker to forge a SAML Response to authenticate as any user.
An attacker would need a signed XML document by the identity provider.
https://github.com/tngan/samlify/security/advisories/GHSA-r683-v43c-6xqv
Memory leak in Oracle Transparent Network Substrate (TNS)
Driftnet Engineering detail a remote memory revelation vulnerability, thank fully Internet exposure is small..
We identified an information disclosure vulnerability in the Oracle Transparent Network Substrate (TNS) protocol, which is used for Oracle database communications. Oracle assigned CVE-2025-30733 to the vulnerability, and fixed it in the patch released on April 15, 2025.
The issue can result in potentially sensitive system memory, including environment variables, being exposed to an unauthenticated remote user over the internet. The leaked information appears to be a read of uninitialised memory.
The default configuration of Oracle RDBMS since version 10g limits unauthenticated external access, so we didn’t expect to see widespread exposure of this vulnerability. However, because only minor changes to the default configuration are needed for the issue to become remotely observable, we do see limited numbers of exposed servers.
…
Despite the default and recommended configuration being secure, to date we’ve observed a limited number of servers (around 40) exhibiting this memory leak vulnerability.
https://driftnet.io/blog/oracle-tns-memory-leak
Endless Subscriptions: Open RAN is Open to RIC E2 Subscription Denial of Service Attacks
Felix Klement, Alessandro Brighente, Anup Kiran Bhattacharjee, Stefano Cecconello, Fernando Kuipers, Georgios Smaragdakis, Mauro Conti and Stefan Katzenbeisser detail a vulnerability which goes to show there is much to do in terms of telecommunications specific vulnerabilities..
By deploying a malicious xApp, we demonstrate how an adversary can flood the Near-RT RIC with excessive subscription requests, leading to service disruption. This attack exploits the lack of rate-limiting mechanisms within the Service Model (SM), a critical component of the Near-RT RIC responsible for handling E2 subscription requests.
https://gsmaragd.github.io/publications/EuroSP2025-ORAN/
gist.github.com/fklement/3a43dbb9fb361dddd8db7703080ade0f
Frame by Frame, Kernel Streaming Keeps Giving Vulnerabilities
Angelboy shows that when you find a rich seam of vulnerabilities you can indeed turn up gold repeatedly..
After discovering several vulnerabilities — including those related to the Proxying series — in Kernel Streaming, we decided to dive deeper into its internals. Between late 2023 and the end of 2024, we identified over 20 vulnerabilities. Approximately 14 of them are related to AVStream, with most occurring during frame handling. In this post, I’ll focus on these frame-related issues.
https://devco.re/blog/2025/05/17/frame-by-frame-kernel-streaming-keeps-giving-vulnerabilities-en/
Ericsson Packet Core Controller (PCC), May 2025
Ericsson releases a patch.. hey we know those teams!
Ericsson Packet Core Controller (PCC) contains a vulnerability where an attacker sending a large volume of specially crafted messages may cause service degradation.
Ericsson thanks following people for reporting this issue to us:
The UK’s National Cyber Security Centre (NCSC)
The UK Telecoms Lab (UKTL)
https://www.ericsson.com/en/about-us/security/psirt/cve-2024-53827
Offense
Attack capability, techniques and trade-craft.
Uncovering Exposed Industrial Control Systems and Honeypots in the Wild
Martin Mladenov, Laszlo Erdodi and Georgios Smaragdakis provide some profound stats on the volume of ICS honeypots on the Internet..
We classify them thanks to large-scale application-layer scanning on all ports and multiple independent attributes, including network information, number of open ports, and known honeypot signatures. Our results show that 15% to 25% of the exposed industrial control systems are honeypots (with two-thirds of them belonging to the medium- or high-confidence categories). Our results challenge previous reports on the prevalence and distribution of exposed industrial control systems. The developed methodology enables industry operators to assess exposed assets and aid protection teams in creating stealthier honeypots
https://gsmaragd.github.io/publications/EuroSP2025-ICS/EuroSP2025-ICS.pdf
Exploitation
What is being exploited..
UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware
Asheer Malhotra and Brandon White detail what looks like an alleged Chinese campaign exploiting a zero-day in software which is a software platform designed to help organizations manage assets, work, and property, particularly those in public works, utilities, and similar sectors.
Post-compromise activity involves the rapid deployment of web shells such as AntSword and chinatso/Chopper on the underlying IIS web servers. UAT-6382 also employed the use of Rust-based loaders to deploy Cobalt Strike and VSHell malware to maintain long-term persistent access.
We track the Rust-based loaders as “TetraLoader,” built using a recently publicly available malware building framework called “MaLoader.” MaLoader, written in Simplified Chinese, allows its operators to wrap shellcode and other payloads into a Rust-based binary, resulting in the creation of TetraLoader.
https://blog.talosintelligence.com/uat-6382-exploits-cityworks-vulnerability/
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
TriageMCP: Vibe Malware Triage
eversinc33 releases what will the first of many in the agentic enabled world of triage..
MCP server for static PE analysis.
https://github.com/eversinc33/TriageMCP
Bypassing kASLR via Cache Timing
r0keb details how this technique works - interestingly not stable across all CPU vendors..
Windows KASLR bypass using prefetch side-channel
https://r0keb.github.io/posts/Bypassing-kASLR-via-Cache-Timing/
specifically the original work says reliable on Intel, not so on AMD.
https://github.com/exploits-forsale/prefetch-tool
Inside the Volume Shadow Copy Service: Exploring the Internals of VSS
DebugPrivilege details how it works under the hood which will no doubt inspire some offensive as well as defensive use cases..
Each VSS writer may support different types of backup operations, so it’s important for the requestor to check which backup types are available before proceeding. The choice of backup type affects how data is collected and how restores are performed later.
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Annual report
Nothing overly of note this week
Cyber Hard Problems Focused Steps Toward a Resilient Digital Future (2025) - US National Academies of Sciences, Engineering Medicine - not sure I agree on all fronts here
Artificial intelligence
Books
Events
OffensiveCon25 - videos
10th IEEE European Symposium on Security and Privacy, Venice, June 30 - July 4, 2025
Video of the week - Perri Adam’s keynote from OffensiveCon
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.