CTO at NCSC Summary: week ending November 19th
CNI cyber resilience is our strategic imperative..
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week of note is the zero day reportedly exploited by criminal actors, alleged data destruction in Israel and a ransomware incident in a Chinese bank’s US arm.
In the high-level this week:
NCSC Annual Review 2023 - some have stated a desire to achieve a more disruptive and destructive impact against western CNI, including in the UK. The NCSC continues to prioritise the resilience of UK CNI.
Our Aussie partners also released ASD Cyber Threat Report 2022-2023
also there was a Report on the state of cyberspace security in the Republic of Poland in 2022
Shields Ready - CISA’s Shields Ready campaign empowers the critical infrastructure community to increase resilience, or the ability to prepare for, adapt to, withstand and rapidly recover from disruptions caused by changing conditions.
MFA roll-out on DNA testing platforms - password spraying and password reuse has led to the a number of DNA testing platforms rolling out MFA - I find this interesting for several reasons, not least it happened. I suspect other services have something to learn from here..
AlphV files an SEC complaint against MeridianLink for not disclosing a breach to the SEC (2) - AlphV has seemingly reported its victim to the SEC. - who had ransomware group reports victim to regulator on their board? Be interesting to see if this drives a greater level of reporting going forward.
Class action lawsuit filed against Intel for security defects in CPUs - Plaintiffs seek redress for Intel’s knowing decision to sell processors with an egregiously defective design without telling the truth, and for a supposed “fix” that destroys their CPUs’ performance—a pernicious cure that rivals the (quite serious) sickness requiring it.
Aussie Telco boards hit with strict cybersecurity rules - Optus, Telstra and other major telco boards will be required to sign off on a new or updated cyber risk management program every year or face hundreds of thousands of dollars in penalties.
Robertson v Singtel Optus Pty Ltd - The applicants seek orders for the discovery and inspection of the report prepared for one or more of the Optus respondents by Deloitte Touche Tohmatsu concerning a data breach which occurred in mid-September 2022 - Optus lost
The attack against Danish critical infrastructure: Report on the largest cyber attack against Danish critical infrastructure that we know of - The attack happened in May 2023. The release is from November 2023 against its Energy sector
NSA and ESF Partners Release Recommended Practices for Software Bill of Materials Consumption - The guidance in this release aids software developers, suppliers, and customer stakeholders in ensuring the integrity and security of software via contractual agreements, software releases and updates, notifications, and mitigations of vulnerabilities.
EU Member states agree common position on a targeted amendment to the cybersecurity act - it clarifies the definition of ‘managed security services’ and the alignment with the revised network information systems (‘NIS 2’) directive
ASIC warns of ‘alarming’ holes in business’ cyber defences - ASIC chairman Joe Longo has warned businesses must close “alarming” gaps in their cybersecurity defences,
Tech firms must clamp down on illegal online materials (in the UK) - Ofcom sets out first steps tech firms can take to create a safer life online
EU Parliament backs plans for better access to, and use of, data - The new legislation establishes rules on the sharing of data generated through the use of connected products or related services (e.g. the Internet of Things, industrial machinery) and allows users to access the data they generate.
RUSI’s Cyber Research Group leads briefing to the White House’s International Counter Ransomware Initiative (CRI) - Last week, the Director of RUSI’s Cyber Research Group James Sullivan presented the team’s findings and recommendations on cyber insurance and the ransomware challenge to a collective of 50 nations and international organisations.
The Mirai Confessions: Three Young Hackers Who Built a Web-Killing Monster Finally Tell Their Story - NONE OF THE three young men who built Mirai fit the profile of a cybercriminal.
Report on Debate on Cybersecurity at the UN First Committee on Disarmament and International Security - OEWG participants were coalescing around a concept of regular institutional dialogue that would be “a single-track state-led permanent mechanism under UN auspices
Ransomware attack on ICBC disrupts trades in US Treasury market - Chinese bank says it has contained a hack that affected some fixed income and equities transactions
ICBC paid ransom after hack that disrupted markets, cybercriminals say
Geopolitical Cybercrime: LockBit attack on the ICBC - The fallout from this LockBit attack on the ICBC has broad geopolitical implications. It directly creates tension and causes issues between China and Russia.
Cyber Risk Accumulation: Fully tackling the insurability challenge - The fast-evolving nature of cyber threats complicates insurers’ efforts to accurately quantify extreme cyber risks and limits the amount of protection they can offer. This, combined with low cyber insurance take-up, means the cyber protection gap remains huge. This report provides an overview of the challenges associated with insuring extreme cyber risks, including the constraints on traditional actuarial techniques in measuring potential cyber losses
How SIM Swappers Straight-Up Rob T-Mobile Stores - Video shot from a getaway car shows how SIM swappers have snatched worker tablets to help them take over phone numbers.
Russia to limit only VPN services which pose a 'threat' to security - Russia plans to block certain Virtual Private Networks (VPNs) and protocols which are deemed by a commission of experts to pose a threat, state news agency RIA reported citing correspondence from the digital ministry.
Reporting on/from China
Artificial intelligence
NIST’s Responsibilities Under the October 30, 2023 Executive Order - The EO directs NIST to develop guidelines and best practices to promote consensus industry standards that help ensure the development and deployment of safe, secure, and trustworthy AI systems.
RSF and 16 partners unveil Paris Charter on AI and Journalism - the Paris Charter on AI and Journalism defines ethics and principles that journalists, newsrooms and media outlets around the world will be able to appropriate and apply in their work with artificial intelligence.
Common guideposts to promote interoperability in AI risk management - The OECD AI Principles call for AI actors to be accountable for the proper functioning of their AI systems in accordance with their role, context, and ability to act.
CISA’s Roadmap for Artificial Intelligence - a whole-of-agency plan aligned with national AI strategy, to address our efforts to: promote the beneficial uses of AI to enhance cybersecurity capabilities, ensure AI systems are protected from cyber-based threats, and deter the malicious use of AI capabilities to threaten the critical infrastructure Americans rely on every day.
Cyber proliferation
Israeli Spyware Firm NSO Demands “Urgent” Meeting With Blinken Amid Gaza War Lobbying Effort
LinkedIn says spy firm targeted Hungarian activists, journalists before 2022 elections
Government users in a European country of Predator spyware targeted their colleagues
Disciplinary proceedings against those who allowed the export of the Predator outside of Greece submitted to parliament
How a tiny Pacific Island became the global capital of cybercrime - In the succeeding years, tiny Tokelau became an unlikely internet giant—but not in the way it may have hoped. Until recently, its .tk domain had more users than any other country’s: a staggering 25 million. But there has been and still is only one website actually from Tokelau that is registered with the domain: the page for Teletok. Nearly all the others that have used .tk have been spammers, phishers, and cybercriminals.
Reflections this week are around CNI and the pace and urgency of the challenge to ensure our collective cyber resilience objectives are achieved. CNI provides strategic optionality for threat actors and as such it is critical we ensure that they (threat actors) can not in the first instance target, then infiltrate or dwell within it. Some of the reporting below shows that globally CNI is being targeted and this should serve as a warning / evidence base there is no room for complacency.
Enjoying this? Don’t get via e-mail? Subscribe:
Think someone else would benefit? Share:
All attribution is by others and not the UK Government, please see the legal text at the end.
Have a lovely Thursday
Ollie
Cyber threat intelligence
Who is doing what to whom and how.
Reporting on Russia
Russia – New Russian digital interference against France
French Government reporting on a disinformation campaign..
VIGINUM has a high degree of confidence that these bots are affiliated to the RRN network, given that one of their main activities consists in redirecting people to RRN websites.
As regards the initial distribution of the photos, while photos of the graffiti seem to have been first published authentically on X at 7.37 p.m. on 30 October, VIGINUM identified the first publication by the RRN bot network on 28 October, from 7.24 p.m. onwards – i.e. some 48 hours earlier.This new Russian digital interference operation against France testifies to the persistence of an opportunist and irresponsible strategy aimed at exploiting international crises in order to spread confusion and create tensions in the public debate in France and Europe.
Sandworm Disrupts Power in Ukraine Using a Novel Attack Against Operational Technology
Ken Proska, John Wolfram, Jared Wilson, Dan Black, Keith Lunden, Daniel Kapellmann Zafra, Nathan Brubaker, Tyler Mclellan and Chris Sistrunk detail a historic disruptive attack which sheds further light on alleged Russian doctrine.
In late 2022, [we] responded to a disruptive cyber physical incident in which the Russia-linked threat actor Sandworm targeted a Ukrainian critical infrastructure organization. This incident was a multi-event cyber attack that leveraged a novel technique for impacting industrial control systems (ICS) / operational technology (OT). The actor first used OT-level living off the land (LotL) techniques to likely trip the victim’s substation circuit breakers, causing an unplanned power outage that coincided with mass missile strikes on critical infrastructure across Ukraine. Sandworm later conducted a second disruptive event by deploying a new variant of CADDYWIPER in the victim’s IT environment.
https://www.mandiant.com/resources/blog/sandworm-disrupts-power-ukraine-operational-technology
Reporting on China
The rootkit virus spreads through the "Dragon Babu" private server and can hijack web pages
Chinese reporting on a local threat which shows a degree of sophistication targeting Microsoft Windows for likely criminal purposes.
In order to reduce the possibility of detection and removal, the virus disguises itself as the system driver pci.sys.
..
The Rootkit virus will also protect itself from being read and modified by Hooking the FSD (File System Driver) device object to avoid detection by anti-virus software.
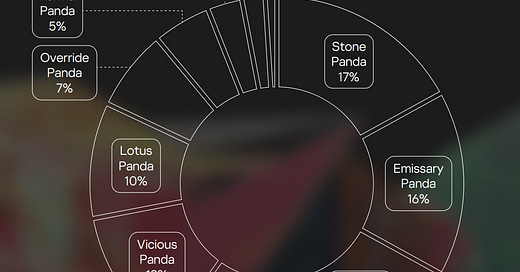
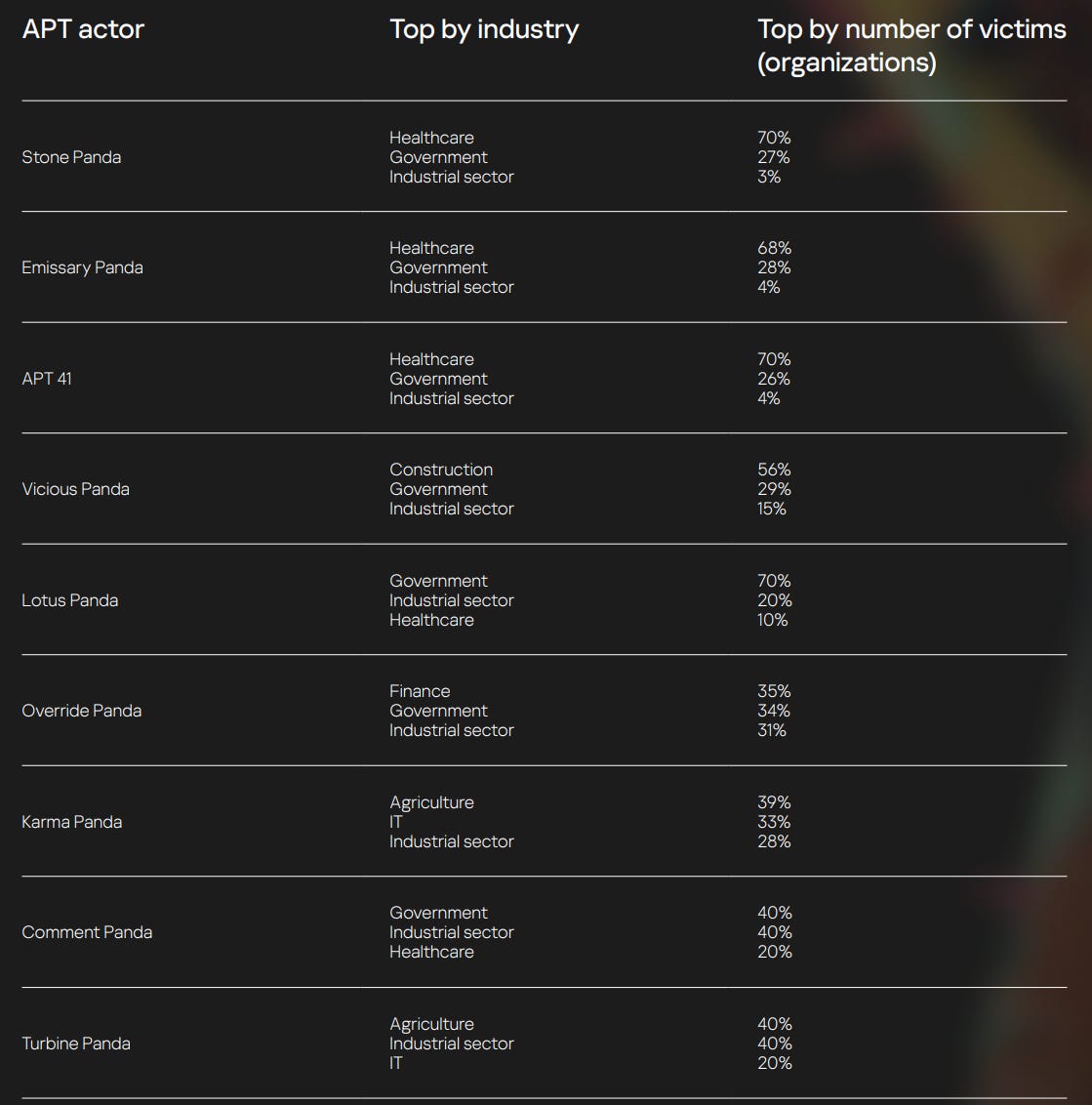
Modern Asian APT groups’ tactics, techniques and procedures (TTPs)
Nikita Nazarov, Kirill Mitrofanov, Alexander Kirichenko, Vladislav Burtsev, Natalya Shornikova, Sergey Kireev, Danila Nasonov and Vasily Berdnikov provide their summary on a range of suspected regional actors with various samples which result in indicating how are the busier groups from their dataset.
also with sectoral targeting breakdowns - agriculture was a bit of surprise to me.
Reporting on North Korea
Detection of attack circumstances abusing asset management program (Andariel Group)
South Korean reporting on an alleged North Korea threat actor targeting a specific asset management product. However the exact means of initial access i.e. vulnerability or product feature is unclear. I suspect however more than likely than not product feature given the type of product…
[We] confirmed that the Andariel threat group, which is known to be affiliated with or a subordinate organization of the Lazarus group, has recently been distributing malware through attacks using a specific asset management program.
It is impossible to tell from the log alone whether it is an attack using a vulnerability or a simple exploit.
Lazarus going after Apple Developers
Reporting on a downloader sample which appears to be going after developers who develop for macOS. More supply chain shenanigans?
https://twitter.com/BaoshengbinCumt/status/1722799049915666869?t=JQlsXB2J8HmcWkPzP1TN3w&s=19
macOS DPRK capability
OSX Nuksped sample reported on here by a South Korean researcher which is allegedly being deployed Lazarus. The thing I noted here is they are using HTTP and HTTPS apparently.
https://wezard4u.tistory.com/6654
Reporting on Iran
IMPERIAL KITTEN Deploys Novel Malware Families
Commercial reporting on what is said to be a suspected Iranian actor leveraging one-day exploits for initial access. Also SQL injection - after memory corruption this is a vulnerability class high up on my wish list for eradicating.
IMPERIAL KITTEN is an Iran-nexus adversary with a suspected connection to the Islamic Revolutionary Guard Corps (IRGC).
[We] identified that contemporary IMPERIAL KITTEN intrusion chains leverage the following tactics, techniques and procedures:
Use of public scanning tools, one-day exploits, SQL injection and stolen VPN credentials for initial access
Use of scanning tools, PAExec and credential theft for lateral movement
Data exfiltration by leveraging custom and open source malware to target Middle Eastern entities
..
several malware samples associated with IMPERIAL KITTEN activity, including:
IMAPLoader, which uses email for command and control (C2)
A similar sample named StandardKeyboard
A malware sample that uses Discord for C2
A Python generic reverse shell delivered via a macro-enabled Excel sheet
This next-stage tooling indicates IMPERIAL KITTEN continues to use email-based C2 mechanisms, similar to those used in their Liderc malware family.
https://www.crowdstrike.com/blog/imperial-kitten-deploys-novel-malware-families/
MuddyC2Go
Simon Kenin reports on apparent evolution in underlying C2 framework by what he cites as a suspected Iranian threat actor. Takeaway is they continue to invest and evolve
[We] identified a previously unreported C2 framework suspected to be in use by MuddyWater
The C2 framework may have been in use by the MuddyWater group since at least 2020
The framework’s web component is written in the Go programming language – hence the name we gave it: MuddyC2Go
MuddyWater seems to have stopped using PhonyC2 and is now using MuddyC2Go instead
[We] observed the following changes in recent activity:
The archives are now password protected. This is done to evade email security solutions that scan files inside archives without a password.
Instead of using a remote administration tool where an operator executes a PowerShell script to connect to MuddyWater’s C2, a new executable is now being sent. This executable contains an embedded PowerShell script that automatically connects to MuddyWater’s C2, eliminating the need for manual execution by the operator.
The Caracal Kitten organization has been active in Iran recently
An Android sample which implies a relation to Kurdistan targeting based on the domain name - a country with which Iran shares a border.
[We] captured the mobile RAT sample of the Caracal Kitten organization. This RAT program will collect a series of sensitive information such as the infected person's mobile phone device information, address book, mobile phone files, etc. and send it back to the hacker server.
BiBi Wiper Used in the Israel-Hamas War Now Runs on Windows
The destructive attacks have rolled into Israel. Further evidence that some threat actors have destruction in their playbook.
On Oct. 30, Israeli-based incident response company SecurityJoes posted findings about a new wiper malware for Linux systems used by pro-Hamas hacktivists in the Israel-Hamas war. The company is currently tracking the malware as the BiBi-Linux Wiper.
The next day, the BlackBerry Research and Intelligence Team found a variant that targets Windows systems, which we’ve labeled the BiBi-Windows Wiper.
https://blogs.blackberry.com/en/2023/11/bibi-wiper-used-in-the-israel-hamas-war-now-runs-on-windows
Our team's in-depth open-source intelligence (OSINT) investigation also revealed similar modus operandi used by other hacktivist groups, notably the Iranian-linked APT - Moses Staff.
Agonizing Serpens (Aka Agrius) Targeting the Israeli Higher Education and Tech Sectors
Or Chechik, Tom Fakterman, Daniel Frank and Assaf Dahan provide further linkage with suspected Iranian threat actors and their destructive attacks.
[We] investigated a series of destructive cyberattacks beginning in January 2023 and continuing as recently as October 2023, targeting the education and technology sectors in Israel.
Agonizing Serpens (aka Agrius) is an Iranian-linked APT group that has been active since 2020. The group is known for its destructive wiper and fake-ransomware attacks and mainly targets Israeli organizations across multiple industries and countries.
https://unit42.paloaltonetworks.com/agonizing-serpens-targets-israeli-tech-higher-ed-sectors/
Identifiers for Wipers activity in Israel
Finally we have some TTPs released by the Israeli government.
https://www.gov.il/he/departments/publications/reports/alert_1660
Reporting on Other Actors
Ransomware Actors Continue to Gain Access through Third Parties and Legitimate System Tools
FBI warning - noting the use of interaction with victims via voice to lay down their system management tools in order to obtain remote access.
The FBI continues to track reporting of third-party vendors and services as an attack vector for ransomware incidents. Between 2022 and 2023, the FBI noted ransomware attacks compromising casinos through third-party gaming vendors. The attacks frequently targeted small and tribal casinos, encrypting servers and the personally identifying information (PII) of employees and patrons.
As of June 2023, the Silent Ransom Group (SRG), also called Luna Moth, conducted callbackphishing data theft and extortion attacks by sending victims a phone number in a phishing attempt, usually relating to pending charges on the victims’ account. Once the victims called the provided phone number, malicious actors directed them to join a legitimate system management tool via a link provided in a follow-up email. The threat actors then used the management tools to install other legitimate system management tools that can be repurposed for malicious activity. The actors then compromised local files and the network shared drives, exfiltrated victim data, and extorted the companies.
https://www.ic3.gov/Media/News/2023/231108.pdf
Malvertiser copies PC news site to deliver infostealer
Jérôme Segura provides further evidence not all is wholesome in the advertising ecosystem.
In a new campaign, we observed a threat actor copying a legitimate Windows news portal to distribute a malicious installer for the popular processor tool CPU-Z.
This type of website is often visited by geeks and system administrators to read the latest computer reviews, learn some tips and download software utilities. The Windows Report was never compromised and is legitimate, but rather threat actors copied its content to trick users.
This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix and VNC Viewer as seen in its infrastructure (domain names) and cloaking templates used to avoid detection. We have informed Google with the relevant details for takedown.
Unlucky Kamran: Android malware spying on Urdu-speaking residents of Gilgit-Baltistan
Lukas Stefanko highlights a watering hole come phishing attack to laydown a mobile capability to handsets. This tradecraft of website → mobile app prompt → download I suspect will be adopted by others as it is a legitimate use pattern that people will be familiar with.
ESET researchers have identified what appears to be a watering-hole attack on a regional news website that delivers news about Gilgit-Baltistan, a disputed region administered by Pakistan. When opened on a mobile device, the Urdu version of the Hunza News website offers readers the possibility to download the Hunza News Android app directly from the website, but the app has malicious espionage capabilities.
TA402 Uses Complex IronWind Infection Chains to Target Middle East-Based Government Entities
Joshua Miller and team reporting on a suspected Gazaian threat actor who is said to be using phishing and malicious documents for initial access.
From July through October 2023, [our] researchers observed TA402 engage in phishing campaigns that delivered a new initial access downloader dubbed IronWind. The downloader was followed by additional stages that consisted of downloaded shellcode.
During the same period, TA402 adjusted its delivery methods, moving from using Dropbox links to using XLL and RAR file attachments, likely to evade detection efforts.
This threat actor has consistently engaged in extremely targeted activity, pursuing less than five organizations with any single campaign. They have also maintained a strong focus on government entities based in the Middle East and North Africa.
Proofpoint has tracked TA402 since 2020. Our researchers assess the threat actor is a Middle Eastern advanced persistent threat (APT) group that historically has operated in the interests of the Palestinian Territories and overlaps with public reporting on Molerats, Gaza Cybergang, Frankenstein, and WIRTE.
Discovery
How we find and understand the latent compromises within our environments.
Detects artifacts associated with post exploitation activity of LaceTempest related to the SysAid 0day
Matt Green provides a work aid for everyone hunting for exploitation of this vulnerability.
Detects artifacts associated with post exploitation activity of LaceTempest related to the SysAid 0day.
There are several sub artifact scopes, with configurable regex parameters to target.
Yara.Process: Targets observed malware and cobalt strike via process yara
Disk.Ntfs: targets known disk IOCs via Windows.ntfs.mft
Forensic.Usn: targets known disk IOCs via USN journal
Evtx.Defender: Searches Defender event logs for evidence of associated alerts
Evtx.NetworkIOC: targets known strings of network IOCs in Firewall, Sysmon logs.
Evtx.PowershellIOC: targets known strings of powershell IOCs in Powershell logs.
https://docs.velociraptor.app/exchange/artifacts/pages/sysaid/
Detecting “Effluence”, an Unauthenticated Confluence Web Shell
Reporting which shows you don’t always need to be super stealthy to be effective. Also the web server level implant we have seen before on IIS and Apache, but another good example here.
The web shell encountered during [our] investigation, however, hijacks the underlying Apache Tomcat webserver and silently inserts itself between Confluence and Tomcat–making itself available on every webpage, including the unauthenticated login page. The web shell does not make any changes to the webpages and allows requests to pass through it unnoticed until a request matches specific parameters.
[We] identified this web shell on public malware repositories with no detections, indicating others may be at risk of this malware.
Detect threats using Microsoft Graph activity logs - Part 2
Fabian Bader provides the next post on how to use this new logging source for effect.
MicrosoftGraphActivityLogsis an excellent source of data that can be used to analyze the usage in any environment. There are some caveats to be aware of, mostly that other APIs are not part of this log and therefore there might some gaps that you as an defender should be aware of.
https://cloudbrothers.info/detect-threats-microsoft-graph-logs-part-2/
Okta Incident Response Notes and Threat Hunting in Okta
Huseyin Rencber guides us through how to do threat hunting through Okta’s logging.
Important for the debug data, it will provide new IP new location new device details. It will give fresh IP addresses, locations, and device details, all of which are crucial for the debug data. Keep a focused eye on admin login activity; if you see any unusual device behavior or location, for example, you can send out an alert.
Debug Case Study: Analysis of ProxyShell via IIS Worker Memory Dumps
Lovely analysis showing the value of memory forensics to gain further insight into threat actor behavior.
This section covers the process of tracking ProxyShell activity within memory dumps of the IIS Worker Process (w3wp.exe). While it's common to detect ProxyShell artifacts via IIS logs and standard event logs on disk. This write-up is used as a reference for analyzing w3wp.exe memory dumps where different debugging techniques are being leveraged, and so on.
Defence
How we proactively defend our environments.
ACSC and CISA Release Business Continuity in a Box
I ❤️ the value this provides. Solutions like this is how we help those that might not otherwise recover in part from devasting cyber attacks.
Today, the Australian Signals Directorate’s Australian Cyber Security Centre (ASD's ACSC) and CISA released Business Continuity in a Box. Business Continuity in a Box, developed by ACSC with contributions from CISA, assists organizations with swiftly and securely standing up critical business functions during or following a cyber incident.
https://www.cisa.gov/news-events/alerts/2023/11/13/acsc-and-cisa-release-business-continuity-box
How to improve your security incident response processes with Jupyter notebooks
Tim Manik, Bryant Pickford, and Daria Pshonkina walks through a way of taking an analysts view of a cyber event if dealing with an incident in AWS.
We will show you how to use Jupyter Notebook to investigate a security event. With this solution, you can automate the tasks of gathering data, presenting the data, and providing procedures and next steps for the findings.
Incident Writeups
How they got in and what they did.
Nothing this week
Vulnerability
Our attack surface.
Dissecting Intel’s Explanation of Key Usage in Integrated Firmware Images (IFWI)
Why including example keys in reference code is bad ..
One of the shocking discoveries during our initial analysis was that the same Intel Boot Guard keys had been reused by multiple device vendors. How is this even possible if the keys should be generated by device manufacturers or OEMs who develop and support firmware code for them?
In its paper, here’s how Intel explains the potential root cause of the Intel OEM keys reuse between multiple product lines and vendors:
“However, some production systems have been identified that were using the example keys from the reference code instead of OEM/ODM-generated keys.” – Intel Corporation.
Access Server Security Update (CVE-2023-46849, CVE-2023-46850) | OpenVPN
Thankfully only in versions which have been released since January - but also highlights that continuously changing code can continuously introduce vulnerability if not tightly coupled with comprehensive security validation/testing.
The use after free memory security issue is a more serious one as there is the potential for leaking sensitive information from memory.
https://openvpn.net/security-advisory/access-server-security-update-cve-2023-46849-cve-2023-46850/
Offense
Attack capability, techniques and trade-craft.
Abusing Microsoft Access "Linked Table" Feature to Perform NTLM Forced Authentication Attacks
Haifei Li details a capability we can expect to be more widely used in 3..2.
Microsoft Access (part of the Office suite) has a “linking to remote SQL Server tables” feature.
This feature can be abused by attackers to automatically leak the Windows user’s NTLM tokens to any attacker-controlled server, via any TCP port, such as port 80.
The attack can be launched as long as the victim opens an .
accdbor .mdbfile. In fact, any more-common Office file type (such as a .rtf) can work as wellThis technique allows the attacker to bypass existing Firewall rules designed to block NTLM information stealing initiated by external attacks.
LdrLibraryEx
A capability which will trip up some EDRs
low dependencies & function use (only ntdll.dll used)
position independent code
lightweight and minimal
easy to use
load modules from memory
load modules from disk
api sets support
bypass image load callbacks (using private memory)
support for images with delayed import, tls, seh, etc.
https://github.com/Cracked5pider/LdrLibraryEx
Exploitation
What is being exploited.
SysAid On-Prem Software CVE-2023-47246
Sasha Shapirov details a vulnerability which appears based on industry reporting to have been exploited criminal threat actors as a zero day.
On Nov 2nd, a potential vulnerability in our on-premise software came to our security team’s attention.
The investigation determined that there was a zero-day vulnerability in the SysAid on-premises software
https://www.sysaid.com/blog/service-desk/on-premise-software-security-vulnerability-notification
then we have further industry reporting:
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
What IIS that malware
John Southworth develops a new tool to help in the analysis of Microsoft IIS targeted implants.
we have released a plugin for IDA Pro to help facilitate native IIS module analysis at multiple stages; including:
Loading in relevant classes/symbolic constants;
Identifying and renaming the virtual methods of IIS classes;
Applying function prototypes to the known implemented virtual methods; and,
Attempting initial retyping of variables in these methods.
https://www.pwc.com/gx/en/issues/cybersecurity/cyber-threat-intelligence/what-iis-that-malware.html
https://github.com/PwCUK-CTO/iis-helper-plugin
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Gaming-related threat report 2023 - [we] conducted extensive research into prevalent threats targeting the gaming community. Our investigation encompassed attacks that involved threats disguised as game apps, mods and cheats, and features analysis of some of the most active malware families operating in this domain.
Monthly Threat Actor Group Intelligence Report, September 2023 - released November - Korean
Ransomware: how to act against a cyber attack of this type - by the Argentinian government
Two summer schools at Oxford University
English Publications from the Dutch NCSC including:
Factsheet Post-quantum cryptography
Nationwide Crisis Response Plan for Digital Crises
Dealing with risks in the Supply Chain
Artificial intelligence
Awesome GPTs (Agents) Repo - represents an initial effort to compile a comprehensive list of GPT agents focused on cybersecurity (offensive and defensive), created by the community
JARVIS-1: Open-World Multi-task Agents with Memory-Augmented Multimodal Language Models
Books
None this week
Events
2023 Aspen Cyber Summit - Stream from Nov 15th
CVE/FIRST VulnCon 2024, Raleigh (NC), US - March 25th-27th, 2024
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.