CTO at NCSC Summary: week ending October 13th
Europe goes strong with its new law on cybersecurity requirements for products.. 👏
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note other that edge devices being exploited once more..
In the high-level this week:
Russian foreign intelligence poses global threat with cyber campaign exploiting established vulnerabilities - NCSC UK and US partners warn:
“UK and US cyber agencies highlight ongoing exploitation of vulnerabilities at scale by Russian cyber actors.
Organisations encouraged to rapidly deploy patches and prioritise software updates to prevent systems being accessed by online actors linked to Russia’s Foreign Intelligence Service.”
Not all types of MFA are created equal... - NCSC UK blogs about new guidance - “Our updated multi-factor authentication (MFA) guidance recommends organisations use techniques that give better protection against phishing attacks.”
Cyber security tips for barristers, solicitors and legal professionals - NCSC UK provides advice - “The following steps are aimed at sole practitioners and also small/medium-sized legal firms, to help them to reduce the likelihood of becoming victims of a cyber attack. Larger sized organisations should consult with their in-house IT/support teams.”
Funded Cyber Essentials Programme - NCSC UK - “a free Cyber Essentials programme to small organisations working in AI, Quantum, engineering or synthetic biology and semiconductors. “
Represent the UK Cyber Team - SANS announces - “Are you an 18–25-year-old cyber security enthusiast ready to put your skills to the test?.. The UK Cyber Team Competition consists of three Capture the Flag (CTF) rounds, with the final event taking place in January 2025. The selected UK Cyber Team will represent the UK on the international Capture The Flag stage.”
Introduction of landmark Cyber Security Legislation Package - Australian Home Affairs announces - “The Cyber Security Legislative Package will implement seven initiatives under the 2023-2030 Australian Cyber Security Strategy, addressing legislative gaps to bring Australia in line with international best practice and take the next step to ensure Australia is on track to become a global leader in cyber security. These measures will address gaps in current legislation to:
mandate minimum cyber security standards for smart devices;
introduce mandatory ransomware reporting for certain businesses to report ransom payments;
introduce a ‘limited use’ obligation for the National Cyber Security Coordinator and the Australian Signals Directorate (ASD); and
establish a Cyber Incident Review Board.”
Cyber resilience act: Council adopts new law on security requirements for digital products - European Council announces - “The Council adopted today a new law on cybersecurity requirements for products with digital elements with a view to ensuring that products, such as connected home cameras, fridges, TVs, and toys, are safe before they are placed on the market (cyber resilience act). The new regulation aims to fill the gaps, clarify the links, and make the existing cybersecurity legislative framework more coherent, ensuring that products with digital components, for example ‘Internet of Things’ (IoT) products, are made secure throughout the supply chain and throughout their lifecycle.”
NCSC NZ launches new incident response exercise - NCSC NZ launches - “a new resource to help New Zealand organisations test their incident response plan and, in turn, help to improve their cyber resilience.”
Research shows most Kiwi are positive about cyber security, wary of AI tools - NCSC NZ researches - “results of an annual international survey on cyber security attitudes and behaviours, titled Oh Behave!. Over 6,500 individuals across New Zealand, the United States, Canada, Germany, the United Kingdom, Australia, and India were asked about key cybersecurity behaviours, attitudes and trends.”
Dutch government will replace hackable traffic lights to avoid movie-like carnage - Cyber News reports - “The solution, the Ministry of Infrastructure and Water Management soon confirmed, was to replace the traffic lights completely. There are tens of thousands of them, though, so the process will take time – the plan is to finish replacing the traffic lights by 2030.” - this is technical debt!
Growing Cyber threats prompt Philippine Army’s 1st 16th AF visit - US Air Force announces - “Colonel Edward Rivera, 616th Operations Center, director of operations, welcomed Philippine Army Col. Windell Rebong, Command and Control Communications and Cyber Systems, deputy assistant chief, and five associates, here, July 18, for a subject-matter-expert exchange amid rising cyberattacks.”
Free support for small businesses [in Australia] that face cyber attacks - The North West Star reports - “The $11.1 million small business cyber resilience service will offer free, one-on-one assistance to small business owners to help them recover from and build resilience against cyber attacks The federal government has appointed IDCARE, a not-for-profit advisory group, to run the service.”
Semiconductors
AI chip packaging drives peak investment at Japan's Ibiden - Nikkei Asia reports - “Japanese chip packaging supplier Ibiden has been busy expanding capacity to manufacture advanced products for the artificial intelligence market. The spending includes two factories in Gifu prefecture that are due to be up and running in the next few years.”
Huawei is sending samples of its new AI chip meant to rival Nvidia - South China Morning Post reports - “Huawei has offered samples of its Ascend 910C processor to large Chinese server companies for hardware testing and configuration, according to two sources briefed by the matter. The chip, an upgraded version of the 910B, is being offered to large Chinese internet firms, which are also major Nvidia customers, according to one of the sources, a distributor of Huawei AI chips.”
Reporting on/from China
Eight jailed after China used crypto to pay its spies in Taiwan - DL News reports - “This case effectively halted the continued leak of military secrets and uncovered the Chinese Communist Party’s new criminal tactic of offering bribes in the form of virtual currency,”
Business Priorities of Chinese Cyber Range Providers Go Hand in Hand with State Cyber Capability Development - Natto Thoughts asserts - “China’s cyber range market booms, fueled by the state’s demand for developing capable cyber talent and improving the effectiveness of “attack and defense live-fire capability”
Tracking China Leaked Documents - four part Japanese analysis by NHK of the alleged activities of i-Soon
Artificial intelligence
Automated Red Teaming with GOAT: the Generative Offensive Agent Tester - Meta researches - “We instantiate GOAT with 7 red teaming attacks by prompting a general-purpose model in a way that encourages reasoning through the choices of methods available, the current target model's response, and the next steps. Our approach is designed to be extensible and efficient, allowing human testers to focus on exploring new areas of risk while automation covers the scaled adversarial stress-testing of known risk territory. We present the design and evaluation of GOAT, demonstrating its effectiveness in identifying vulnerabilities in state-of-the-art LLMs, with an ASR@10 of 97% against Llama 3.1 and 88% against GPT-4 on the JailbreakBench dataset.”
ShadowLogic - HiddenLayer researches - “[We] discovered a novel method for creating backdoors in neural network models dubbed ‘ShadowLogic’. Using this technique, an adversary can implant codeless, surreptitious backdoors in models of any modality by manipulating a model’s ‘graph’ – the computational graph representation of the model’s architecture. Backdoors created using this technique will persist through fine-tuning, meaning foundation models can be hijacked to trigger attacker-defined behavior in any downstream application when a trigger input is received, making this attack technique a high-impact AI supply chain risk.
The Bletchley Park process could be a building block for global cooperation on AI safety - Brookings think tanks - “While progress to date has been significant, major challenges to reaching agreement on a networked approach to AI safety remain. The following takes a closer look at where the Bletchley Park process now stands in the run-up to Paris 2025.”
China Telecom say AI model with 1 trillion parameters trained with Chinese chips- South China Morning Post reports - “The Institute of AI at China Telecom, one of the country’s large state-backed telecoms operators, said in a statement on Saturday that its open-source TeleChat2-115B and a second unnamed model were trained on tens of thousands of domestically produced chips, marking a milestone amid tightening US restrictions on China’s access to advanced semiconductors, including Nvidia’s latest AI chips.”
How do Workers Adjust to Robots? Evidence from China - The Economic Journal reports - “We find that a one standard deviation increase in robot exposure led to a decline in labour force participation (-1%), employment (-7%), and hourly earnings (-8%) of Chinese workers. At the same time, among those who kept working, robot exposure increased the number of hours worked by 8%. These effects were concentrated among the less educated and larger among men, prime-age, and older workers”
Tianyi Cloud Xiran Integrated Intelligent Computing Service Platform - Sina Finance reports - “The training and pushing service capabilities were significantly upgraded, with new closed-source, multi-modal base large models and data sets, supporting large-scale training of tens of thousands of cards, and further improving training stability.”
Cyber proliferation
Blacklisted Israeli cyberintelligence firms hope for Trump victory - intelligence Online reports - “The military conflict in the Middle East is pushing the lobbyists of blacklisted Israeli cyberintelligence firms to redouble their efforts in the run-up to the November US presidential election.”
Bounty Hunting
Ukrainian National Pleads Guilty to “Raccoon Infostealer” Cybercrime - US Department of Justice announces - “According to court documents, Mark Sokolovsky, 28, conspired to operate the Raccoon Infostealer as a malware-as-a-service or “MaaS.” Individuals who deployed Raccoon Infostealer to steal data from victims leased access to the malware for approximately $200 per month, paid for by cryptocurrency. These individuals used various ruses, such as email phishing, to install the malware onto the computers of unsuspecting victims”
The ransomware battle is shifting — so should our response - Financial Times opeds - “Earlier this year an attack against a US health insurance giant shut down operations at hospitals and pharmacies for weeks, costing the company a reported $872mn. This does not include the $22mn ransom payment that the company made to a Russia-based gang. On the other side of the world, a ransomware attack shut down the Port of Nagoya — Japan’s busiest port — for two full days.” .. “Some insurance company policies — for example covering reimbursement of ransomware payments — incentivise payment of ransoms that fuel cyber crime ecosystems. This is a troubling practice that must end.”
Reflections this week around the fact that know more about what is in our sausages than our software.
SBOMs tell us that 3rd party libraries are patched but not that the 1st party code is 25 years old, in a memory unsafe language of which only 8% has been touched in the last 4 years.
Transparency in technology has a way to go if we are to make informed decisions..
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Mind the (air) gap: GoldenJackal gooses government guardrails
Matías Porolli details capability that Hollywood would be proud of by this alleged Russian threat actor. Many gaps in the understanding, but also re-enforces why removable media is not a great look in 2024.
GoldenJackal used a custom toolset to target air-gapped systems at a South Asian embassy in Belarus since at least August 2019. In this blogpost, we describe these tools publicly for the first time.
This blogpost also features the first public description of a highly modular toolset GoldenJackal deployed on various occasions between May 2022 and March 2024 against a national government organization of a country in the European Union.
These toolsets provide GoldenJackal a wide set of capabilities for compromising and persisting in targeted networks. Victimized systems are abused to collect interesting information, process the information, exfiltrate files, and distribute files, configurations and commands to other systems.
The ultimate goal of GoldenJackal seems to be stealing confidential information, especially from high-profile machines that might not be connected to the internet.
…
in the GoldenHowl malware, the C&C protocol is referred to as transport_http, which is an expression typically used by Turla (see our ComRat v4 report) and MoustachedBouncer. This may indicate that the developers of GoldenHowl are Russian speakers.
Analysis of attack activities of APT-C-20 (APT28) using compound attack tactics
Chinese report on this alleged Russian threat actor which isn’t really notable for any other fact that the reporting comes from China.
In another common attack method of APT28, attackers usually send phishing emails containing malicious links to target users. Once the user clicks on the link, they will be redirected to a bait page carefully designed by the attacker and induce the user to click on a specific button or link.
When users are fooled and click on the malicious button in the bait page, they will be further directed to a WebDAV server. On this server, the attacker pre-installed a malicious LNK shortcut file. Once the victim double-clicks these LNK files, a series of malicious activities will be triggered without their knowledge.
Reporting on China
Chinese Threat Groups That Use Ransomware and Ransomware Groups That Use Chinese Names
Natto Thoughts alleged that the number of Chinese ransomware operations is increasing. Interesting is the alleged politically motivated attack in 2023 against the gambling industry.
Examining cases of ransomware activities linked to Chinese threat actors shows an increase in the deployment of ransomware since 2016. The majority of the cases that threat hunters have revealed were politically motivated and conducted by threat actors with some degree of relationship to the Chinese state. (The Spectrum of State Responsibility, which cyber law researcher Jason Healey introduced in 2012, categorizes variations on the criminal/state relationship in hacking operations, ranging from “state-prohibited” to “state-encouraged” to “state-integrated.”) Chinese threat actors use ransomware to cause misattribution, distraction, disruption or even destruction and to provide financial gain, cover for espionage operations and the ability to remove the evidence.
nattothoughts.substack.com/p/chinese-threat-groups-that-use-ransomware
Reporting on North Korea
Analysis of Kimsuky Group's 'BlueShark' Threat Tactics A Deep Dive into the Kimsuky Threat Tactics & BlueShark
Genians reenforces what is known about these alleged North Korean groups which act as a useful summary / reminder.
● Use of various types of malware such as LNK, ISO, MSC, HWP, etc.
● Attempt to access by disguising it as an interview, special lecture, or lecture request
● Delivery of malicious files through the cloud such as OneDrive, Proton Drive, etc.
Analysis of cyberattacks from North Korea and Konni attack artifacts
Igloo provides what they alleged is analysis of changes in this North Korean threat actor’s techniques. If nothing else it highlights the need to deal with the very many vulnerable WordPress instances - as where one threat actor innovates others are Likely to follow.
So far, we have looked at the current status of the Konni group, one of the North Korean attack groups, and their representative malware. If we classify the characteristics of Konni's recent attacks, they can be classified into four types:
Changes in social engineering attack keywords,
Changes in attack vectors according to usage environment,
Use of remotely controlled malware for information theft, and
C2 construction using WordPress.
Reporting on Iran
Nothing this week
Reporting on Other Actors
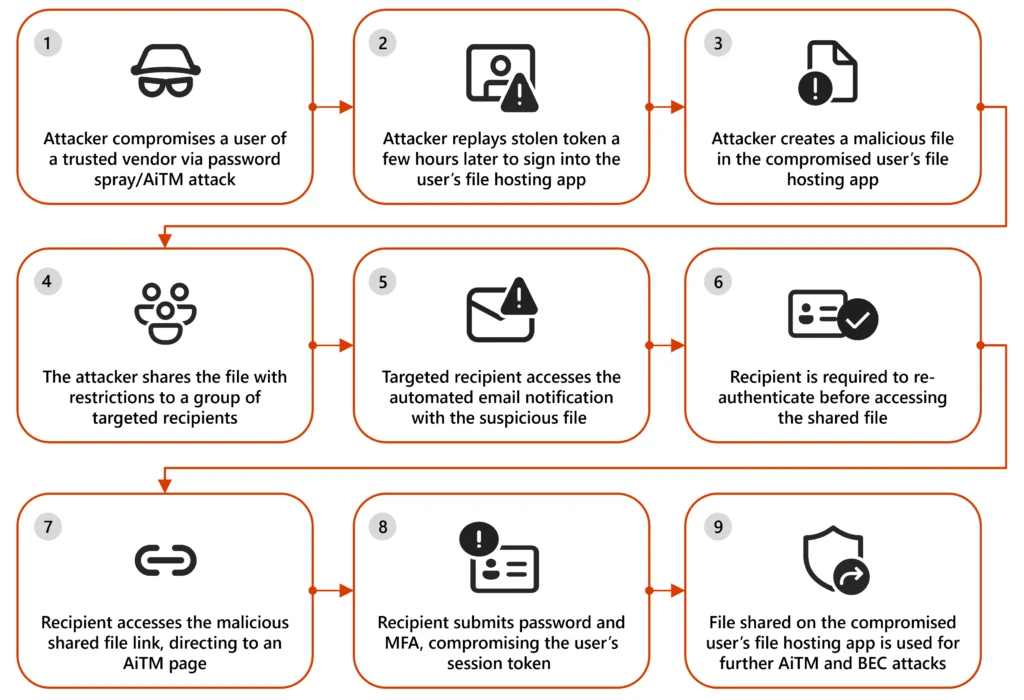
File hosting services misused for identity phishing
Microsoft details an evolution in tradecraft to avoid detection but also misuse trusted placed in the legitimate functionality.
Since mid-April 2024, we observed threat actors increasingly use these tactics aimed at circumventing defense mechanisms:
Files with restricted access: The files sent through the phishing emails are configured to be accessible solely to the designated recipient. This requires the recipient to be signed in to the file-sharing service—be it Dropbox, OneDrive, or SharePoint—or to re-authenticate by entering their email address along with a one-time password (OTP) received through a notification service.
Files with view-only restrictions: To bypass analysis by email detonation systems, the files shared in these phishing attacks are set to ‘view-only’ mode, disabling the ability to download and consequently, the detection of embedded URLs within the file.
Mamba 2FA: A new contender in the AiTM phishing ecosystem
Grégoire Clermont highlights what cotemporary Adversary in The Middle capability looks like. Note the degree of opsec to trip up auto scanners but also to mask their infrastructure.
Until late September 2024, the relay servers were connecting directly to the Entra ID servers when performing authentications with victim’s credentials. As a result, the IP addresses of the relay servers were exposed in the authentication logs of the targeted tenants. However, starting October 2024, the developers of Mamba 2FA implemented an additional indirection layer, utilising proxy servers sourced from a commercial provider (IPRoyal). In consequence, the IP addresses appearing in authentication logs since October 2024 are those of the datacenter proxies, not the relay servers. (These proxy servers are not pictured on the architecture schema above).
https://blog.sekoia.io/mamba-2fa-a-new-contender-in-the-aitm-phishing-ecosystem/
Discovery
How we find and understand the latent compromises within our environments.
Network traffic large model TrafficLLM
China bringing LLM to network traffic analysis and some security use cases…
TrafficLLM jointly released by Dr. Cui Tianyu of Zhongguancun Laboratory and the team of Professor Xu Ke and Professor Li Qi of Tsinghua University.
Through appropriate learning, TrafficLLM can form two core capabilities of traffic detection and generation on a wide range of downstream tasks such as encrypted traffic classification and APT detection. Compared with 15 state-of-the-art traffic detection and generation solutions, TrafficLLM can achieve F1 scores of 0.9875 and 0.9483, with performance improvements of 80.12% and 33.92% respectively. We further demonstrate TrafficLLM's strong generalization ability to unknown data and real-world environments.
https://github.com/ZGC-LLM-Safety/TrafficLLM
Defence
How we proactively defend our environments.
Windows 11 Administrator Protection | Admin Approval Mode
Rudyooms details how this new feature works..
This feature is designed to eliminate always-on admin rights. Instead, it uses a hidden elevation mechanism to provide just-in-time privileges when needed, keeping admin rights in the shadows until required.
The introduction of Administrator Protection and the System Managed Admin Account concept marks a fundamental shift in managing local admin rights. Microsoft mitigates many traditional UAC vulnerabilities by decoupling elevated tasks from the main user context, making the local admin a safer role.
https://call4cloud.nl/2024/10/windows11-administrator-protection/
Passkeys on Windows: Authenticate seamlessly with passkey providers
Katharine Holdsworth outlines how passkeys deployment are going to become ever more compelling. Also shows the value of standards i.e. through the FIDO alliance.
Passkeys on Windows just got easier! As part of Microsoft’s vision for a passwordless future we are working to make passkeys on Windows simple and intuitive.
As part of our cross-industry commitment, we launched new native support for cross-device authentication and an updated experience to help users along the journey from website to platform. Continuing that journey at Authenticate 2024 we are introducing the following, which will be available in our Windows Insider channels in the coming months:
A plug-in model for third-party passkey providers
Enhanced native UX for passkeys
A Microsoft synced passkey provider
Unintentional Evasion: Investigating How CMD Fragmentation Hampers Detection & Response
Kostas unleashes the wisdom but also highlights the value in testing the data you need to investigate an incident is actually present.
In a recent investigation, I came across a subtle yet significant issue that can hinder forensic analysis and threat detection: command line omission and fragmentation in Windows process execution logs. This isn’t my first time encountering such nuances, so I felt it was worth sharing my insights through this article.
Key Takeaways:
Be Aware of Limitations: Recognize that not all commands executed by an attacker will appear in the logs.
Correlate Available Logs: Carefully examine the logs that are available, looking for patterns or sequences that suggest missing commands.
Consider Additional Logging Mechanisms: Exploring other logging mechanisms or tools may help capture a more complete picture of system activity.
Modern print platform - Windows drivers - Windows protected print mode
Well I guess this means two fuzzers might rule all the printers at least even if you can no longer get privilege escalation on Windows from print drivers..
Modern print is Windows' preferred means of communicating to printers, including the Internet Printing Protocol (IPP), eSCL scanning, and Universal Print.
Modern print doesn't require the installation third-party drivers. This provides a simple, streamlined and secure printing experience compared to traditional printers, regardless of the PC's architecture. Modern print is designed to work with Mopria certified printers, and many existing printers are already compatible with modern print.
The Mopria alliance is a collection of printer manufacturers and software vendors that have come together to define the standards for IPP printing and eSCL scanning. Mopria certified devices guarantee conformance to these standards.
https://learn.microsoft.com/en-us/windows-hardware/drivers/print/modern-print-platform
Incident Writeups & Disclosures
How they got in and what they did.
CreditRiskMonitor.com, Inc.
#1
On July 19, 2024 CreditRiskMonitor.com, Inc. (“Company” or “CRMZ”) detected unauthorized occurrences within its computer network. Upon detecting the unauthorized occurrences, the Company immediately activated its incident response plan and began taking steps to contain, assess and remediate the incident, including conducting an investigation with third-party cybersecurity specialists. CRMZ reported the incident to law enforcement and continues to cooperate with law enforcement’s investigation. The incident has not had a material impact on the Company’s operations, and its information systems have continued to be fully operational.
The Company’s investigation determined that certain files stored within CRMZ’s computer environment may have been viewed or copied by an unauthorized actor between July 8, 2024 and July 17, 2024. CRMZ reviewed the files that could have been viewed or copied to determine whether any sensitive information was contained within those files. The Company’s investigation concluded that personally identifiable information of employees and independent contractors, not customers, may have been viewed or copied by an unauthorized actor. Although CRMZ is not aware of any attempted or actual misuse of that personally identifiable information, on October 8, 2024, CRMZ issued notices to individuals whose personal information was stored within the impacted files so that they may take steps to protect their information, if they feel it is appropriate to do so. CRMZ is offering access to credit monitoring and identity theft protection services at no cost to those individuals for twenty-four (24) months.
https://www.sec.gov/Archives/edgar/data/315958/000114036124043034/ef20036707_8k.htm
ADT Inc.
#2
ADT Inc. (“ADT” or the “Company”) recently became aware of unauthorized activity on the Company’s network, and discovered an unauthorized actor had illegally accessed ADT’s network using compromised credentials obtained through a third-party business partner.
The Company promptly took steps to shut down the unauthorized access, notified the third party its systems had been compromised, launched an investigation, and implemented counter measures intended to safeguard the Company’s information technology assets and operations. ADT has hired leading third-party cybersecurity experts to assist with the Company’s response to the incident, and is working closely with federal law enforcement. The Company is also cooperating closely with its third-party business partner to address the incident.
The Company believes the unauthorized actor exfiltrated certain encrypted internal ADT data associated with employee user accounts during the intrusion. Based on its investigation to date, the Company does not believe customers’ personal information has been exfiltrated, or that customers’ security systems have been compromised. ADT’s containment measures have resulted in some disruptions to the Company’s information systems, and the Company’s investigation is at an early stage and ongoing.
https://www.sec.gov/Archives/edgar/data/1703056/000119312524233900/d876174d8k.htm
Consumer routers targeted by multiple botnets
NCSC Netherlands details how you can have co-habiting botnets on routers..
The National Cyber Security Centre (NCSC) has, following an incident response investigation, observed two botnet malware families simultaneously on a consumer router: Alogin botnet malware and TheMoon malware. This blog post explains the investigation and goes deeper into the two malware families.
Vulnerability
Our attack surface.
CVE-2024-45409: Ruby-SAML / GitLab Authentication Bypass
Harsh Jaiswal & Rahul Maini dispel the many eyes fallacy once more..
In this blog post, we will analyze CVE-2024-45409, a critical vulnerability impacting Ruby-SAML, OmniAuth-SAML libraries, which effectively affects GitLab. This vulnerability allows an attacker to bypass SAML authentication mechanisms and gain unauthorized access by exploiting a flaw in how SAML responses are handled. The issue arises due to weaknesses in the verification of the digital signature used to protect SAML assertions, allowing attackers to manipulate the SAML response and bypass critical security checks.
https://blog.projectdiscovery.io/ruby-saml-gitlab-auth-bypass/
The PrintNightmare is not Over Yet
Itm4n’s provides some insight into a configuration which can’t actually be secured..
Following the publication of my blog post A Practical Guide to PrintNightmare in 2024, a few people brought to my attention that there was a way to bypass the Point and Print (PnP) restrictions recommended at the end. So, rather than just updating this article with a quick note, I decided to dig a little deeper, and see if I could find a better way to protect against the exploitation of PnP configurations
..
The key takeaway is that the seemingly innocuous statement “There is no combination of mitigations that is equivalent to setting Restrict Driver Installation To Administrators to 1” in the Microsoft KB article KB5005652 - Manage new Point and Print default driver installation behavior (CVE-2021-34481) should actually be considered literally. Indeed, you can’t secure a Point and Print configuration if you allow low-privileged users to install printer drivers in one way or another.
https://itm4n.github.io/printnightmare-not-over/
Offense
Attack capability, techniques and trade-craft.
Gaining AWS Persistence by Updating a SAML Identity Provider
Adan details one of the lesser covert mechanism (i.e. it isn’t) for persistence. But it will likely inspire others to look for ones which are..
Nick Frichette has collected a few of these methods in his “Hacking the Cloud” encyclopedia of the attacks/tactics/techniques: Hacking the Cloud — IAM Persistence.
This technique not only allows persistence but, if the attacker has access to a limited privileged identity that can replace SAML metadata but can’t perform other tasks, they might be able to assume a role with higher privileges.
However, this technique has a significant impact because, after changing the SAML metadata, legitimate users won’t be able to access via SSO, which will likely trigger an investigation.
DLL Proxy Generator
Namazso gives a capability which we can expect to be misused in 3..2..
Generate a proxy dll for arbitrary dll, while also loading a user-defined secondary dll.
https://github.com/namazso/dll-proxy-generator
pwnlook
Arturo gives the world a capability which it will be interesting to see if the reliance on Redemption allows trivial detection of in practice..
An offensive postexploitation tool that will give you complete control over the Outlook desktop application and therefore to the emails configured in it.
pwnlookcommunicates with Outlook via COM. By using the Redemption library it can gather all kind of information without triggering any alert to the user, even if you read an unread email the email will keep as unread for the user.The tool comes with some limitations that are related with the, most likely, possibility of dealing with very big OST files. Thats why, for example, I didn't implement an option to "list all emails".
The
Redemption64.dllmust be in the same path as thepwnlook.exe. There is no need to register the DLL (Registry free COM) so you can run it on behalf of any user, even if it isn't Local Admin.
https://github.com/amjcyber/pwnlook
Integrating Sliver into Mythic
Spencer Adolph shows crossing the streams in C2 frameworks is indeed possible..
So while Sliver provides an 'all in one' solution for building and managing implants, Mythic by default only provides an 'agnostic' architecture for controlling any compatible implant over any compatible communication. You install which agents and profiles you want to use, and can add your own custom ones as well.
Not only that, but Mythic provides awesome UI to view data that's pulled back from targets, for example a file browser. I didn't yet know how, but I really wanted to type 'ls' into Mythic instead of the Sliver cli and see that awesomeness.
https://github.com/MythicAgents/sliver/blob/main/blog/blog.md
Downgrade attack: a story as old as Windows…
Andrea Aallievi walks through how protecting against downgrade attacks can be really quite challenging..
We created an individual WDAC policy file, called VbsSiPolicy (and present in your insider release system under “\Windows\System32\CodeIntegrity”) which contains all the minimum version of all the modules located into the TCB (I am speaking about OS loader, Boot drivers, HV and VBS modules). From now, in this blog, I will call this WDAC policy as “Anti-rollback” policy.
..
an attacker can replace the policy file itself with an old one, or replace Winload too. How to deal with this?
https://www.andrea-allievi.com/blog/downgrade-attack-a-story-as-old-as-windows/
EtherGhost: A new generation of webshell manager, compatible with Ant Sword and Ice Scorpion's PHP webshell
A mature capability from China..
Youhun is an open source Webshell manager that provides a more convenient interface and simpler and easier-to-use functions. It can be used in conjunction with or instead of other webshell managers to help users control target machines in various penetration scenarios.
Youhun not only supports the common one-line webshell and common webshell manager functions, but also supports adding Bingxie's webshell and providing any webshell to Yijian for connection. By using Youhun, users can use Yijian to control Bingxie webshell, use Yijian's various plug-ins on Bingxie webshell, and enjoy the rich ecology of Yijian and the traffic encryption and anti-killing features of Bingxie.
https://github.com/Marven11/EtherGhost
VMK extractor for BitLocker with TPM and PIN
Defane also detailed how it can be remediated..
Use Firmware TPM (also called fTPM) included in modern CPU of several brands:
For Intel processor: Intel PTT
For AMD processor: AMD fTPM
To select the fTPM, please refer to your vendor manual. For example, in the case of Dell machine, this change can be made in BIOS menu.
The change of TPM will break your
TPM and PINprotector. Please backup the recovery key for the next boot after the change.fTPM is harder to tap than dTPM via its bus such as SPI or i2c. But keep in mind that the fTPM is not a bulletproof solution: attacks are still possible but harder to realize such faulTPM.
https://post-cyberlabs.github.io/Offensive-security-publications/posts/2024_09_tpmandpin/
https://github.com/post-cyberlabs/VMK-extractor-for-bitlocker-with-tpm-and-pin
Exploitation
What is being exploited..
CVE-2024-30052: Exploiting Visual Studio via dump files
10 months for a patch..
This blog post will talk about CVE-2024-30052, which allows arbitrary code execution when debugging dump files in Visual Studio. I reported this issue to Microsoft in August 2023 and they provided an update that addresses this issue in June 2024.
https://ynwarcs.github.io/exploiting-vs-dump-files
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
The Disappearance of an Internet Domain, How geopolitics can alter digital infrastructure
Artificial intelligence
How Do Large Language Models Acquire Factual Knowledge During Pretraining?
MLE-bench: Evaluating Machine Learning Agents on Machine Learning Engineering
LLM Emergent Abilities and Weird Machines - “An interesting consequence of these scaling laws is what is known as "Emergent Abilities". These are capabilities that were not explicitly programmed into the model but arise naturally as a result of scaling and generalizing over vast amounts of pretraining data. In short, an LLM's abilities are not so much designed as they are discovered. This represents a fundamental and important distinction from traditional software which is designed and programmed with an explicit and intended set of functionalities.”
Books
International Law: To Comply, or Not to Comply - “Through interviews with some 80 senior officials from the United States Department of State, across five administrations, Moremen provides readers with a qualitative and quantitative analysis of the considerations that the U.S. and other nations take into account when deciding whether and to what extent to comply and the circumstances in which compliance is more or less likely.”
Events
Transatlantic Forum on GeoEconomics - recap and videos available
Formal Specification and Validation at Scale - 2-day workshop in Cambridge October 21st - 22nd including virtual
Operationalizing Public-Private Partnerships — Disrupting Cyber Threats at Scale - 22 October 2024
Webinar: Defining Cyber War: The Impact of Insurance on Cyber Norms - 29 October 2024
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.