CTO at NCSC Summary: week ending October 6th
€91 million fine for storing password in clear-text ...
Welcome to the weekly highlights and analysis of the blueteamsec subreddit (and my wider reading). Not everything makes it in, but the best bits do.
Operationally this week nothing overly of note… other than the cost imposed on various criminal actors..
In the high-level this week:
Multi-factor authentication for your corporate online services - NCSC UK publishes - “This guidance describes how administrators responsible for managing access to online digital services for their organisation can apply the strongest types of multi-factor authentication (MFA). It describes the various types of MFA that are commonly available, explains some pitfalls to avoid, and encourages the use of services that support the strength of MFA you require.” - the single most effective control in analysis of root caused breaches - we also need to get past the point where SSO which often enables MFA is charged as extra by platforms!
UK Cyber Security and Resilience Bill - Department for Science, Innovation and Technology publishes - “The Bill will strengthen our defences and ensure that more essential digital services than ever before are protected, for example by expanding the remit of the existing regulation, putting regulators on a stronger footing, and increasing reporting requirements to build a better picture in government of cyber threats.”
Celebrating eight years of being the NCSC – a part of GCHQ - NCSC UK publishes - “As a part of GCHQ, the NCSC, as the National Technical Authority for cyber security, unifies these functions. We take a combined approach, governed by a robust legislative regulatory framework and oversight regime that allows us to safeguard these technologies while maximising their potential for intelligence work.”
UK sanctions members of notorious ‘Evil Corp’ cyber-crime gang, after Lammy calls out Putin’s mafia state - Foreign, Commonwealth & Development Office, National Crime Agency, Dan Jarvis MBE MP and The Rt Hon David Lammy MP sanction - “the UK sanctions 16 members of prolific Russian cyber-crime gang Evil Corp, alongside the US and Australia “
UK and Singapore lead international action to support ransomware victims - Home Office and Dan Jarvis MBE MP announce - “The new guidance - agreed yesterday (1 October 2024) at the Counter Ransomware Initiative - will encourage organisations to carefully consider their options instead of rushing to make payments to cyber criminals in an attempt to stop disruption and data loss. It makes clear that paying a ransom will often only embolden these criminals to target other victims, and there is no guarantee of data retrieval, malware removal or the end of a ransomware attack. “
Biden-Harris Administration Convenes Fourth Global Gathering to Counter Ransomware - The White House announces- “At the gathering, CRI members advanced the Initiative’s commitments to resilience, cooperation, and disruption through the CRI’s Policy Pillar, Diplomacy and Capacity Building Pillar, and the International Counter Ransomware Task Force (ICRTF).”
International Counter Ransomware Initiative 2024 Joint Statement
Why you only need to remember two words to avoid password misery - The Times publishes - “The NCSC suggests using three random words as your password. Ollie Whitehouse, its chief technical officer, told the BBC: “People are very good at remembering three random words. So: spaceship, green, bridge — things like that. People can remember a collection of those and use them uniquely on different websites.”
Irish Data Protection Commission fines Meta Ireland €91 million - Data Protection Commission announces - "after MPIL notified the DPC that it had inadvertently stored certain passwords of social media users in ‘plaintext’ on its internal systems (i.e. without cryptographic protection or encryption)."
T-Mobile Required to Change Business Practices After Data Breaches - Federal Communications Commission announces “T-Mobile has agreed to important forward-looking commitments to address foundational security flaws, work to improve cyber hygiene, and adopt robust modern architectures, like zero trust and phishing-resistant multifactor authentication. The Commission believes that implementation of these commitments, backed by a $15.75 million cybersecurity investment by the company as required by the settlement, will serve as a model for the mobile telecommunications industry.”
Global Strategic Trends: Out to 2055 - UK Ministry of Defence publishes - “Global Strategic Trends: Out to 2055 (Seventh Edition) (GST 7) offers foresight analysis from a thematic and geographic perspective, complemented by five scenarios which describe hypothetical pathways into a future world order. “
White House agonizes over UN cybercrime treaty - Politico reports - “The uncertainty over the treaty stems from fears that countries including Russia, Iran and China could use the text as a guise for U.N. approval of their widespread surveillance measures and suppression of the digital rights of their citizens.”
CISA Faces Challenges Sharing Cyber Threat Information as Required by the Cybersecurity Act of 2015 - Office of Inspector General inspects and CISA responds - “CISA’s Cybersecurity Division (CSD) is conducting an independent evaluation of the AIS service, which includes exploring alternative approaches to its automated threat intelligence and information-sharing capabilities to align with the new long-term Threat Intelligence Enterprise Services strategy. CSD is exploring a longterm vision for Threat Intelligence Enterprise Services, which seeks to address the challenges identified in the audit, build on existing capabilities for AIS, and provide a platform for future growth and evolution, including recruiting and retaining participants and Federal data producers.”
Semiconductors
U.S. National Science Foundation and Department of Commerce announce a new $30M funding opportunity, funded by the CHIPS & Science Act, to prepare talent for semiconductor jobs nationwide - US National Science Foundation announces - “NSF and DOC will select an institution of higher education, nonprofit organization, or group of such institutions and organizations to establish and operate the Network Coordination Hub. The Hub will be responsible for coordinating a coalition of regional consortia, each with its own programs and centers, to offer consistent, rigorous, engaging curricula, instructional materials, experiential opportunities, teacher professional development and more throughout the U.S.”
Britain buys semiconductor factory to secure supply for military - Reuters announces - “The government said on Friday that the plant in Newton Aycliffe in northern England was the only secure domestic manufacturer of the semiconductors.”
China, South Korea, Taiwan to spend most on chip equipment over next two years - South China Morning Post reports - “Semiconductor manufacturers will spend a record US$400 billion on computer chip-making equipment in 2025-2027, global industry association SEMI said in estimates published on Thursday, with China, South Korea and Taiwan leading the way.”
US, India unite on chips to open up new front in tech war against China - South China Morning Post reports - South China Morning Post reports - “During Indian Prime Minister Narendra Modi’s visit to Washington earlier this month, he and US President Joe Biden finalised the agreement to establish a semiconductor fabrication plant in Kolkata. The facility in the eastern Indian city will focus on defence equipment, telecommunications, and renewable energy”
US sets new rule that could spur AI chip shipments to the Middle East - Reuters reports - “Under the new rule, data centers will be able to apply for Validated End User status that will allow them to receive chips under a general authorization, rather than requiring their U.S. suppliers to obtain individual licenses to ship to them.”
Chinese start-up Numemory claims memory chip breakthrough amid US tech sanctions - South China Morning Post reports - “Numemory, formally known as Xincun Technology (Wuhan) Co, recently introduced to the domestic market its 64-gigabyte NM101, a type of storage-class memory (SCM) chip that is “expected to break the long-term monopoly of international giants in this field””
ByteDance said to be turning to Huawei chips to train AI model amid US curbs, sources say - South China Morning Post reports - “ByteDance’s next step in the AI race is to use Huawei’s Ascend 910B chip to train a large language AI model, said the people”
Reporting on/from China
U.S. Wiretap Systems Targeted in China-Linked Hack - The Wall Street Journal reports - “The hackers appear to have engaged in a vast collection of internet traffic from internet service providers which count businesses large and small, and millions of Americans, as their customers. Additionally, there are indications that the hacking campaign targeted a small number of service providers outside of the U.S., the people said. “
Inside Beijing’s app collecting information from Belt and Road companies - The Strategist reports - “China’s Ministry of Foreign Affairs operates a secure digital platform that connects it directly with Chinese companies operating abroad, requiring participating companies to submit regular reports about their activities and local security conditions to the government, internal documents reveal.”
FBI probes whether Silicon Valley venture firm passed secrets to China - Financial Times reports - The Times reports - “California-based Hone Capital, which launched in 2015 with $115mn of initial capital from a Chinese private equity group, invested in 360 US tech start-ups in less than three years. This included acquiring stakes in driverless-car maker Cruise, payments group Stripe and aerospace engineer Boom.”
After US, Europe probes Chinese car software - Politico reports - “After the U.S. government on Monday announced it wanted to ban Chinese tech linking cars to the internet from American roads, European officials have echoed Washington's concerns about the spying, surveillance and sabotage risks posed by what EU digital czar Margrethe Vestager described as “computers on wheels.”
Exclusive: China surpasses S. Korea in key sectors, sparking industry worries - The Chosun Daily reports - “During the interviews, executives pointed out that China has not only caught up with S. Korea in most industries, except semiconductors, but in many areas, it has already surpassed the nation.”
China Urges Local Companies to Stay Away From Nvidia’s Chips - Bloomberg reports - “Chinese regulators have been discouraging companies from purchasing Nvidia’s H20 chips, which are used to develop and run AI models, according to people familiar with the matter. The policy has taken the form of guidance rather than an outright ban, as Beijing wants to avoid handicapping its own AI startups and escalating tensions with the US, said the people, who asked not to be identified because the matter is private.”
Huawei: Chinese firm reduced to a shadow of former size as UK restrictions bite - CityAM Reports - “Turnover at the UK arm of Chinese telecommunications giant Huawei has been slashed by more than £1bn since 2019 as the impact of UK and US restrictions bite. The London-headquartered business has reported a turnover of £229.56m for 2023, down from the £359m it posted in 2022.”
‘Huawei too closed, monopolistic’: Chinese academic’s rare outburst signals emerging rift - South China Morning Post reports - “In a video clip posted on video-sharing service Bilibili on Sunday night, Sun criticised Huawei’s development model as too closed and monopolistic, saying the company’s control of the industrial chain would not help China to defeat the United States in their ongoing tech war.”
Artificial intelligence
German-French recommendations for the use of AI programming assistants - French Cybersecurity Agency (Agence nationale de la sécurité des systèmes d‘information, ANSSI) and the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) publish - “perspectives are given on the opportunities that arise through the use of AI coding assistants as well as risks associated with the technology. Concrete mitigation measures are outlined.”
China to roll out cybersecurity rules covering generative AI - Nikkei Asia reports - “The network data security management regulations contain 64 clauses based on China's cybersecurity and data security laws. They will go into force on Jan. 1.”
China Unveils World's First 10 Billion Parameter Remote Sensing Foundation Model - Yicai Global reports - “A research team from the Chinese Academy of Sciences has launched the world's first remote sensing foundation model with over 10 billion parameters at a new industry forum.”
Investigating the Intersection of AI and Cybercrime: Risks, Trends, and Countermeasures - Boston University and The University of Akron research - “The study highlights the critical need to prioritize individual cyber hygiene to mitigate the growing risks posed by AI-based threats. By investigating the digital transfer of AI-facilitated malicious information and content across the dark and clear web, this research shed light on the complex dynamics of cybercrime”
Cyber proliferation
Cypriot firm linked to Greek ‘Predator’ surveillance scandal - in-Cyprus reports - “A Cypriot company struck off the official register, has emerged as a key shareholder in a Greek business entity connected to the Predator software surveillance scandal.”
ICE Signs $2 Million Contract With Spyware Maker Paragon Solutions - Wired reports - “The one-year contract between the company’s US subsidiary in Chantilly, Virginia, and ICE’s Homeland Security Investigations Division 3 was signed on September 27 and covers a “fully configured proprietary solution including license, hardware, warranty, maintenance and training.”
NSO Group indicates rare agreement with Apple over dismissal of lawsuit - Cyber Scoop reports - “The filing states that Apple has done little to prosecute its claims, and as such the judge should dismiss the lawsuit “with prejudice,” meaning that it couldn’t be refiled later. But if the judge dismisses it without prejudice, then NSO Group said it would like to be reimbursed for its court costs as the work it has done on the case couldn’t be recycled”
Bounty Hunting
Justice Department Disrupts Russian Intelligence Spear-Phishing Efforts - Justice Department announces - “The Justice Department announced today the unsealing of a warrant authorizing the seizure of 41 internet domains used by Russian intelligence agents and their proxies to commit computer fraud and abuse in the United States.”
Further Evil Corp cyber criminals exposed, one unmasked as LockBit affiliate - UK National Crime Agency announces - “Sixteen individuals who were part of Evil Corp, once believed to be the most significant cybercrime threat in the world, have been sanctioned in the UK, with their links to the Russian state and other prolific ransomware groups, including LockBit, exposed”
LockBit power cut: four new arrests and financial sanctions against affiliatesLockBit power cut: four new arrests and financial sanctions against affiliates - Europol announces - “Europol supported a new series of actions against LockBit actors, which involved 12 countries and Eurojust and led to four arrests and seizures of servers critical for LockBit’s infrastructure.”
Cyber operations and the law - Shehzad Charania responds -”GCHQ Director of Legal Affairs, Mission Policy and International Relations, and Neil M, a Deputy Director at GCHQ, reflect on the importance of law as one of the many essential elements in delivering effective cyber operations”
Reflections this week around how we deal with technical debt in practice. It is clear that as each month clicks by the volume gets larger. One way of reducing it is ensuring it is measurable and understood in board rooms.
In discussions with various accountants on how we might capture technical debt on balance sheets the best suggestion so far has been to quantify the amount of £/$/€ of technology assets which have been capitalised, amortized back in and then not recapitalised. Doing so would hint at that the volume of assets which are being sweated and thus a source of technical debt along with a £/$/€ amount attached to them.
If you have other ideas, would love to hear them..
Think someone else would benefit? Share:
All attribution is by others and not the UK Government unless specifically stated as such, please see the legal text at the end.
Have a lovely Saturday..
Ollie
Cyber threat intelligence
Who is doing what to whom and how allegedly.
Reporting on Russia
Russian Cyber Operations
State Service of Special Communications and Information Protection of Ukraine publishes this analysis of alleged Russian activity.
In 2024, we observe a pivot in their focus towards anything directly connected to the theatre of war and attacks on service providers aimed at maintaining a low profile, sustaining a presence in systems related to war and politics. Hackers are no longer just exploiting vulnerabilities wherever they can but are now targeting areas critical to the success and support of their military operations.
Reporting on China
Separating the bee from the panda: CeranaKeeper making a beeline for Thailand
Romain Dumont details alleged Chinese activity against Thailand, but the initial access vector is not known.
ESET researchers discovered a new China-aligned threat actor, CeranaKeeper, targeting governmental institutions in Thailand. Some of its tools were previously attributed to Mustang Panda by other researchers.
The group constantly updates its backdoor to evade detection and diversifies its methods to aid massive data exfiltration.
CeranaKeeper abuses popular, legitimate cloud and file-sharing services such as Dropbox and OneDrive to implement custom backdoors and extraction tools.
The group uses GitHub’s pull request and issue comment features to create a stealthy reverse shell, leveraging GitHub, a popular online platform for sharing and collaborating on code, as a C&C server.
…
The compromise vectors that CeranaKeeper used in the case we analyzed have yet to be found. When the group obtained a foothold in the network of a Thai governmental institution, in the middle of 2023, a compromised machine conducted brute-force attacks against a domain controller server in the local area network.
Reporting on North Korea
North Korean IT Workers
The Bundesamt für Verfassungsschutz (BfV) warns against this alleged North Korean activity which is used to obtain access to organisations through various ruse…
North Korean intelligence services carry out offensive cyber operations worldwide to obtain foreign currency. In this context, undercover IT specialists (IT workers) are offering their services to companies around the globe via remote work. The proceeds benefit the North Korean regime. The IT workers also aid in the theft of intellectual property and internal data.
Our Private Sector Security Advisory 02/2024 informs about the risks associated with North Korean IT workers and provides companies with guidance on what to watch out for when working with freelancers in order to protect themselves from know-how loss as well as from reputational risks and legal consequences resulting from violating international sanctions.
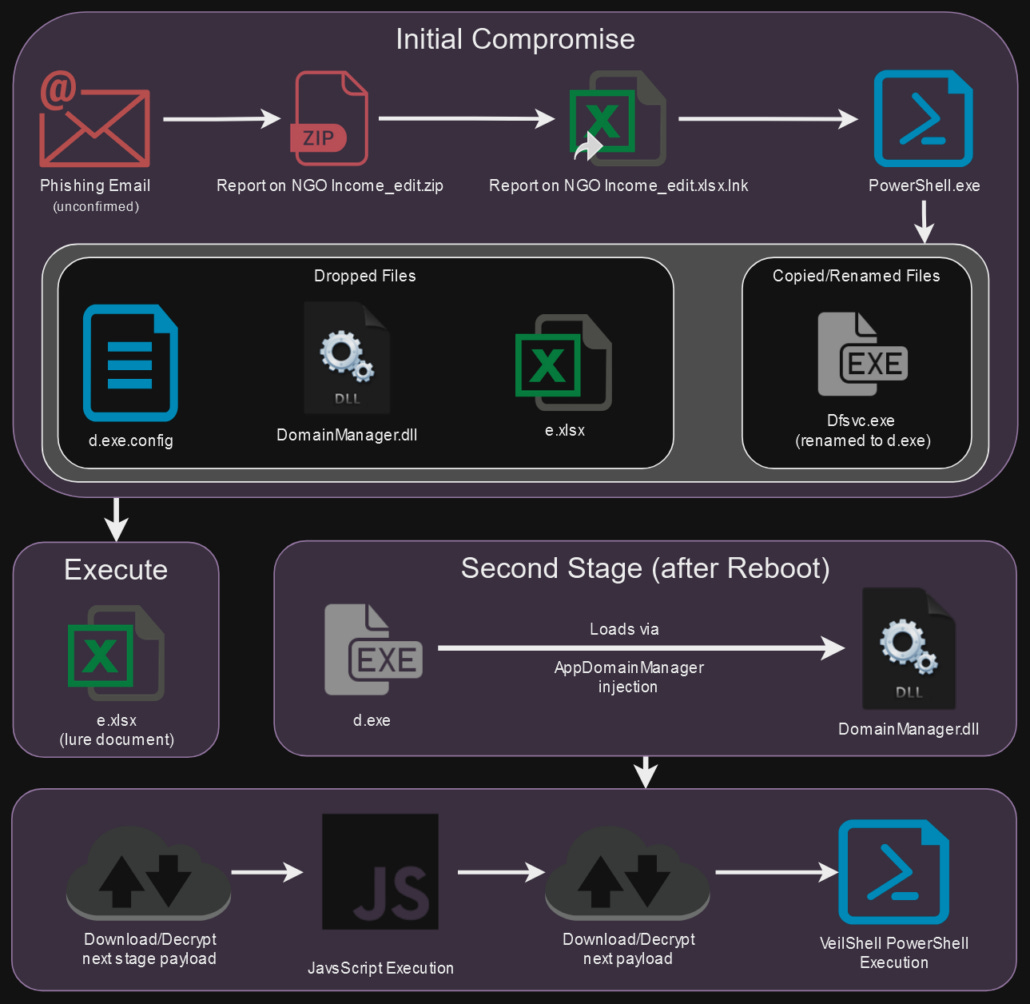
Shrouded Sleep
Den Iuzvyk and Tim Peck detail alleged North Korean activity which can only be described as convoluted and run of the mill..
Towards the end of a rather lengthy chain of malicious stages, the threat actors leveraged a custom PowerShell backdoor featuring a wide range of RAT (Remote Access Trojan) capabilities. Our team has been tracking the custom backdoor as VeilShell due to its stealthy method of execution and capabilities. The backdoor trojan allows the attacker full access to the compromised machine. Some features include data exfiltration, registry, and scheduled task creation or manipulation. We’ll highlight each of these further down in the publication.
Stonefly: Extortion Attacks Continue Against U.S. Target
Symantec’s Threat Hunter Team allege North Korean activity hasn’t stopped due to sanctions..
has found evidence that the North Korean Stonefly group (aka Andariel, APT45, Silent Chollima, Onyx Sleet) is continuing to mount financially motivated attacks against organizations in the U.S., despite being the subject of an indictment and a multi-million dollar reward.
While the attackers didn’t succeed in deploying ransomware on the networks of any of the organizations affected, it is likely that the attacks were financially motivated. All the victims were private companies and involved in businesses with no obvious intelligence value.
https://symantec-enterprise-blogs.security.com/threat-intelligence/stonefly-north-korea-extortion
Reporting on Iran
Continues To Use Credential Phishing Infrastructure to Target Individuals Perceived as a Threat to the Iranian Regime
Domain Tools allege this fresh infrastructure is related to Iranian operations..
Since June 2024, the Iran-nexus actor CHARMING KITTEN (APT42, Mint Sandstorm, TA453) continues to create new network infrastructure consistent with what the Mandiant intelligence team identifies as Cluster B.
There are no confirmed targets of the new infrastructure; however, it is likely that the actor’s target scope remains focused on entities deemed a threat to the Iranian regime.
https://cti-grapevine.com/charming-kitten/
Reporting on Other Actors
Analysis of APT-C-00 (OceanLotus) Dual Loader and Homologous VMP Loader
Chinese reporting on alleged Vietnamese activity which asserts that the VMProtect source code leak has been co-opted to impose cost on defence.
What is different from previous attacks is that OceanLotus "processed" the dual backdoor loader that had been used for nearly two and a half years, and used VMProtect software to protect the loader
This attack used the VMP source code after it was leaked to protect the loader, which greatly increased the cost of analysis .
GorillaBot: The New King of DDoS Attacks
Chinese reporting on what can only be described as an active botnet..
data shows that Gorilla Botnet issued over 300,000 DDoS attack commands in September 2024, with a daily peak of over 20,000 commands. From the timing of the attacks, Gorilla Botnet sent out commands continuously over 24 hours, with a relatively even distribution of commands.
Gorilla Botnet supports multiple CPU architectures such as ARM, MIPS, x86_64, and x86, and is a modified version of the Mirai source code.
https://nsfocusglobal.com/over-300000-gorillabot-the-new-king-of-ddos-attacks/
Discovery
How we find and understand the latent compromises within our environments.
Event Log Talks a Lot: Identifying Human-operated Ransomware through Windows Event Logs
中村 恭脩(Kyosuke Nakamura) releases information which might just help in the event of a human-operated ransomware attack is you respond at machine speed.
JPCERT/CC's investigation confirmed that some ransomware leaves traces in the Windows event log, and that it is sometimes possible to identify the ransomware based on these characteristics. The following four Windows event logs were used in this investigation.
Application Log
Security Log
System Log
Setup Log
The following sections introduce the logs recorded in the Windows Event Log when ransomware is executed.
https://blogs.jpcert.or.jp/en/2024/09/windows.html
Announcing LOLRMM: A Unified Approach to RMM Software Tracking
Michael Haag provides dataset that will help detect attackers who deploy remote monitoring and management software to achieve their aims..
Today, we are thrilled to announce the launch of the Living Off The Land Remote Monitoring and Management (LOLRMM) software project. This groundbreaking initiative aims to revolutionize how we track and manage Remote Monitoring and Management (RMM) utilities in cybersecurity.
Entra Cross-Tenant Activity Monitoring
Steven Lim releases this wonderful work aid against tradecraft seen in use by APT..
AADSpnSignInEventsBeta table is currently in beta and available for a limited time, enabling you to explore Microsoft Entra sign-in events. Monitor cross-tenant activity, which can help detect potential OAUTH app compromises. e.g Midnight Blizzard Case.
Measuring Sentinel WatchList Effectiveness using Behaviour Analytics
Steven Lim release another work aid which will help spot the single in the noise..
If Sentinel UEBA is enabled, running the following KQL will generate a dashboard chart showing the number of watchlist triggers over the past three months. Notable spikes in watchlist hits can offer valuable insights
Defence
How we proactively defend our environments.
Principles of operational technology cyber security
Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), and co-sealed by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), Federal Bureau of Investigation (FBI), Multi-State Information Sharing and Analysis Center (MS-ISAC), United Kingdom’s National Cyber Security Centre (NCSC-UK), Canadian Centre for Cyber Security (Cyber Centre), New Zealand’s National Cyber Security Centre (NCSC-NZ), Germany’s Federal Office for Information Security (BSI Germany), the Netherlands’ National Cyber Security Centre (NCSC-NL), Japan’s National Center of Incident Readiness and Strategy for Cybersecurity (NISC) and National Police Agency (NPA), and the Republic of Korea’s National Intelligence Service (NIS) and NIS’ National Cyber Security Center (NCSC)
describes six principles that guide the creation and maintenance of a safe, secure critical infrastructure OT environment:
Safety is paramount
Knowledge of the business is crucial
OT data is extremely valuable and needs to be protected
Segment and segregate OT from all other networks
The supply chain must be secure
People are essential for OT cyber security
Incident Writeups & Disclosures
How they got in and what they did.
Hacking Kia: Remotely Controlling Cars With Just a License Plate
Sam Curry shows that the technical debt rabbit hole is indeed deep in our every day lives..
On June 11th, 2024, we discovered a set of vulnerabilities in Kia vehicles that allowed remote control over key functions using only a license plate. These attacks could be executed remotely on any hardware-equipped vehicle in about 30 seconds, regardless of whether it had an active Kia Connect subscription.
https://samcurry.net/hacking-kia
Insecurity through Censorship: Vulnerabilities Caused by The Great Firewall
Shubham Shah provides some interesting insight into how the great firewall works..
Diving deeper, we tried to create a minimal reproducible example, and managed to distill it down to specifically any query including webproxy.id. Later we would find out there were a number of “keywords” that would be intercepted.
Vulnerability
Our attack surface.
HPE Aruba Networking Access Points Multiple Vulnerabilities
UDP remote-code-execution for all..
Command injection vulnerabilities in the underlying CLI
service could lead to unauthenticated remote code execution by
sending specially crafted packets destined to the PAPI (Aruba's
Access Point management protocol) UDP port (8211). Successful
exploitation of these vulnerabilities results in the ability to execute
arbitrary code as a privileged user on the underlying operating
system.
https://support.hpe.com/hpesc/public/docDisplay?docId=hpesbnw04712en_us&docLocale=en_US
Offense
Attack capability, techniques and trade-craft.
Nameless C2
trickster0 releases inspiration for others..
I am mostly publishing it due to the fact that I have not seen another Windows Rust implant as small as 256kb (if my memory serves me right) and also has a working sleeping obfuscation method of EkkoEx.
https://github.com/trickster0/NamelessC2
Windows Defender Bypass Dump LSASS Memory with Python
I suspect not for very long..
In this article, we will walk through how to use Python with pywin32 and ctypes to dump LSASS memory into a minidump file while bypassing detection by Windows Defender.
https://mohitdabas.wordpress.com/2024/10/01/windows-defender-bypass-dump-lsass-memory-with-python/
Getting a Havoc agent past Windows Defender (2024)
I also suspect not for very long..
We are going to do some offensive powershell, we are going to find a powershell shellcode runner then combine it with a working AMSI bypass to execute it in memory.
Exploitation
What is being exploited..
CVE-2024-36435
Ivanovanton releases a exploit for this vulnerability which will cause some pain when used by APT..
Buffer overflow vulnerability in Supermicro BMC IPMI firmware due to unchecked length of user-supplied value
https://github.com/binarly-io/ToolsAndPoCs/blob/master/Posix/Supermicro/CVE-2024-36435.py
Tooling and Techniques
Low level tooling and techniques for attack and defence researchers…
WhoYouCalling
Hannes gets a 🥇 for this release because of the sheer time saving it will bring. I remember writing something to catch passwords being sent across the wire in various encoded forms whilst at BlackBerry, it was a real faff in pre ETW days..
Monitors network activity made by a process through the use of Windows Event Tracing (ETW) and Full Packet Capture (FPC). Filters a generated .pcap file with BPF based on the detected network activity made by the process. This application makes process network monitoring hella' easy.
https://github.com/H4NM/WhoYouCalling
Unicorn Engine v2.1.0
This is just one highlight from this release..
memory snapshots/CoW [Copy on Write] support, to enable approximate emulation of all code paths
https://github.com/unicorn-engine/unicorn/releases/tag/2.1.0
Dna: LLVM based static binary analysis framework
Colton Skees and Larkwiot release this work aid..
Dnaimplements an iterative control flow graph reconstruction inspired heavily by the SATURN paper. It iteratively applies recursive descent, lifting (using remill), and path solving until the complete control flow graph is recovered. In the case of jump tables, we use a recursive algorithm based onSouperand z3 to solve the set of possible jump table targets.
https://github.com/Colton1skees/Dna
Footnotes
Some other small (and not so small) bits and bobs which might be of interest.
Aggregate reporting
Cybersecurity in practice: The vigilant logic of kill chains and threat construction
Collection of Docker honeypot logs from 2021 - 2024 - “This is a set of logs collected from running a Docker honeypot on ports 2375 and 4243 (no SSL).”
Deciphering Ransomware in Virtual Machines: A Technical Examination of Reverse Engineering
How does iOS restrict functions by region: A brief analysis of MobileGestalt and Eligibility (Chinese)
Cyber Security as Counter-Terrorism: Seeking a Better Debate - from 2021
Charting the Future of Organised Crime – and the UK’s Response
Hacking the Cosmos: Cyber operations against the space sector. A case study from the war in Ukraine
Artificial intelligence
Semiconductors
Books
Events
Nothing this week
Unless stated otherwise, linked or referenced content does not necessarily represent the views of the NCSC and reference to third parties or content on their websites should not be taken as endorsement of any kind by the NCSC. The NCSC has no control over the content of third party websites and consequently accepts no responsibility for your use of them.
This newsletter is subject to the NCSC website terms and conditions which can be found at https://www.ncsc.gov.uk/section/about-this-website/terms-and-conditions and you can find out more about how will treat your personal information in our privacy notice at https://www.ncsc.gov.uk/section/about-this-website/privacy-statement.